Wazuh is a security platform that combines XDR and SIEM for monitoring and protecting endpoints and cloud workloads [Link]. Virtually any platform has a respective agent available: Linux, Windows, MacOS, Solaris, HPUX, and AIX.

Bare minimal requirements (start small and expand as needed):
- 2 vCPU
- 4 GB of RAM
- 50 GB of Storage
Even though the minimum requirements that I recommended are half of the official documentation, I managed to monitor over 50 endpoints with it at 2.5% avg CPU utilization and 65 to 85% of RAM. The key to my use case is the fact that I monitor Linux endpoints that have no users playing around. Only stand-alone servers with their automatic loads. This reduces the amount of events to the minimum.
INSTALLATION
curl -sO https://packages.wazuh.com/4.11/wazuh-install.sh && sudo bash ./wazuh-install.sh -a
It may take some time but when the installation is completed, it will print the generated password for the Admin account:
INFO: Starting Wazuh installation assistant. Wazuh version: 4.11.0
INFO: Verbose logging redirected to /var/log/wazuh-install.log
(...)
INFO: --- Summary ---
INFO: You can access the web interface https://<wazuh-dashboard-ip>:443
User: admin
Password: XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
24/03/2024 14:23:29 INFO: Installation finished.
Navigate to the URL using the newly created credentials.
SETTING UP AGENTS
After logging in to the Dashboard, click on Add Agent.
Select the platform + architecture of the end point to be monitored, provide the server address (ideally a local name that points to the server, in case it changes IP), and the group (in my case I left the default).
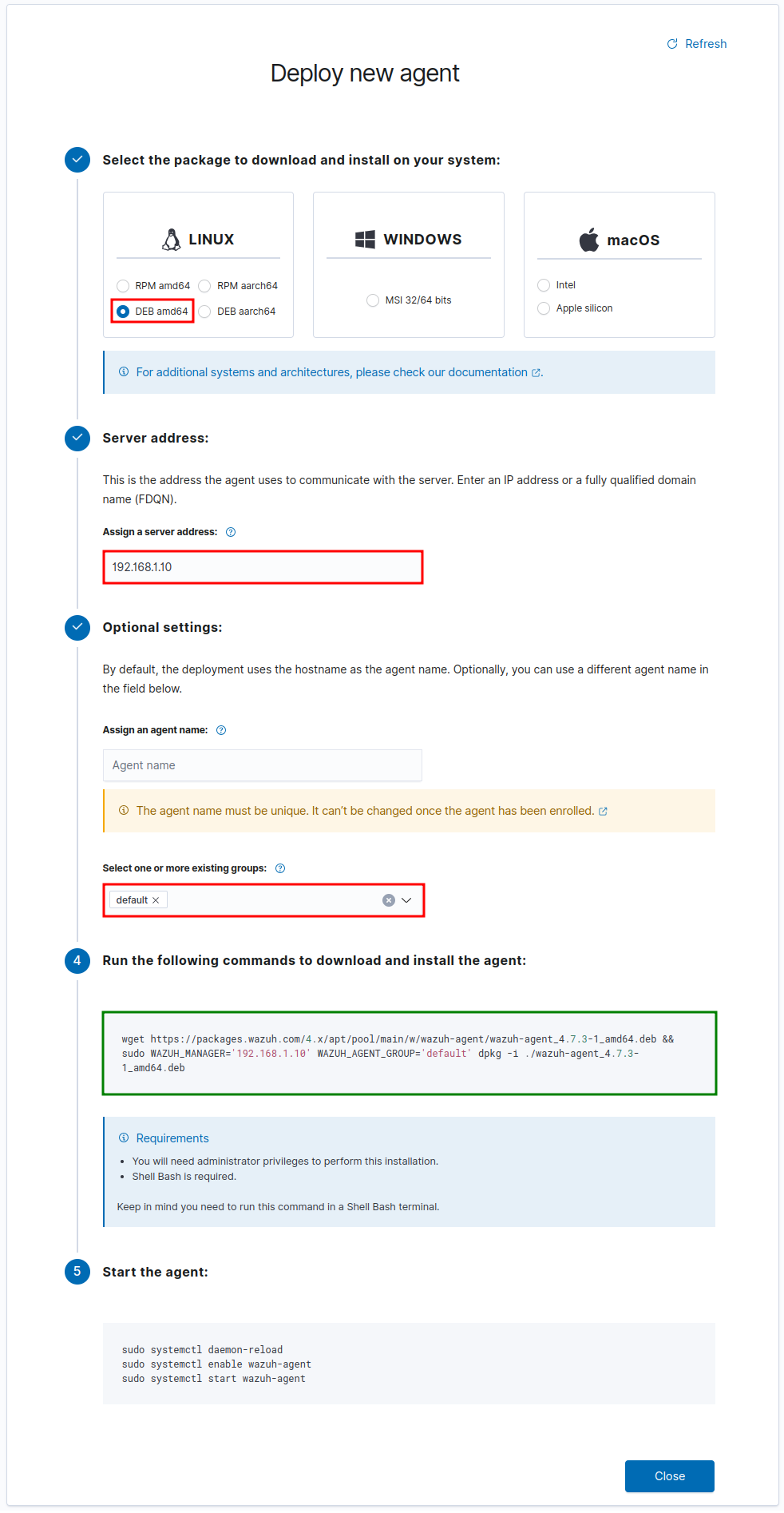
Note that it will not perform anything other than compose a command line that can be copied and executed on the hosts.
wget https://packages.wazuh.com/4.x/apt/pool/main/w/wazuh-agent/wazuh-agent_4.11.0-1_amd64.deb && sudo WAZUH_MANAGER='192.168.1.10' WAZUH_AGENT_GROUP='default' dpkg -i ./wazuh-agent_4.11.0-1_amd64.deb
Unfortunately, after setting up the agent it does not start or enable boot automatically. So, run the following command too.
sudo systemctl daemon-reload && sudo systemctl enable wazuh-agent && sudo systemctl start wazuh-agent
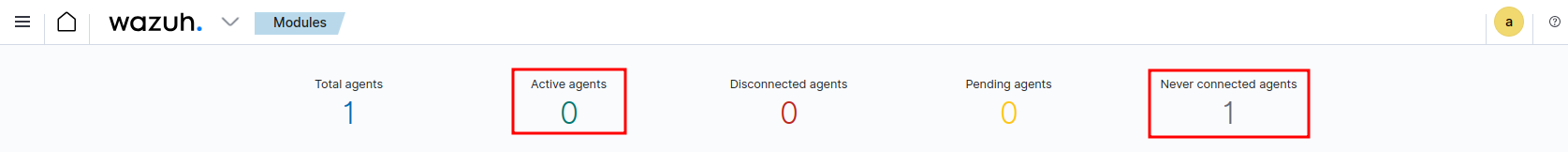
It may take a few seconds to change to Active Agents.
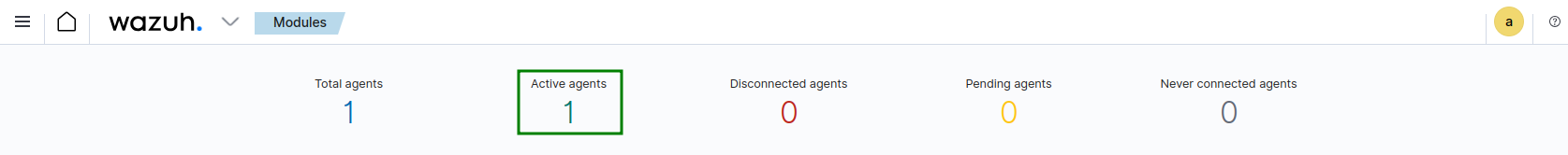
All good, now!
If the agent does not connect to the server, check the logs for clues.
sudo tail -f /var/ossec/logs/ossec.log | grep -i -E "error|warn"
MONITORING END-POINTS
By clicking any Agent (end-point), events will start to be populated. A series of checks will happen right after they are joined (not too resource-intensive).
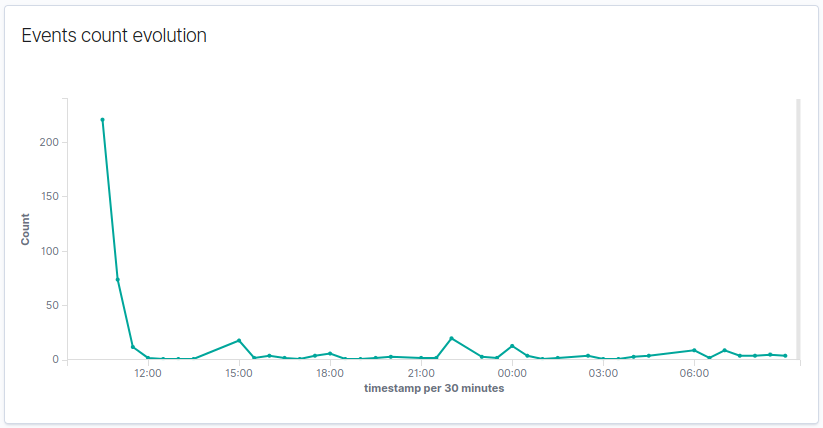
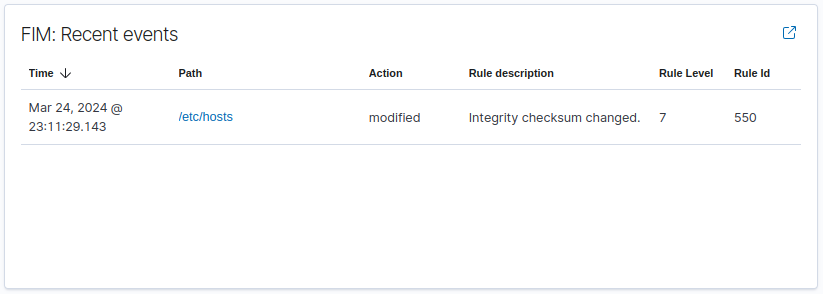
Then, new events will be created as they happen in the server.
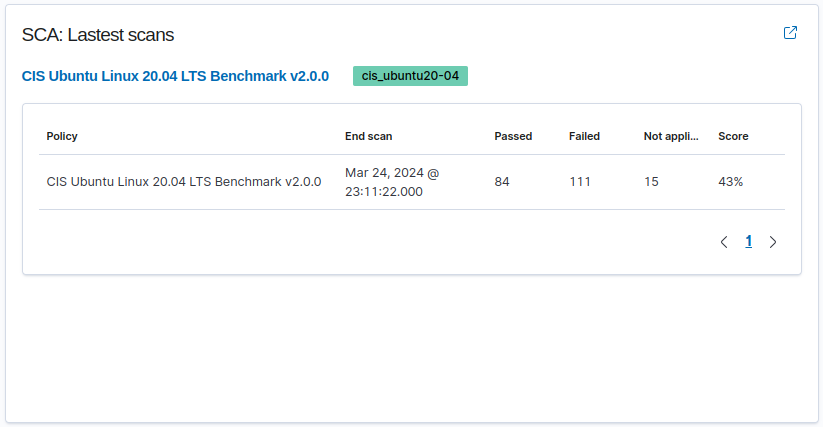
A summary of the current status of the Agent. It classifies each “issue/event” with a respective TTP (Tactic, Technique, and Procedure) from the Mitre and correlates to the compliance regulations.
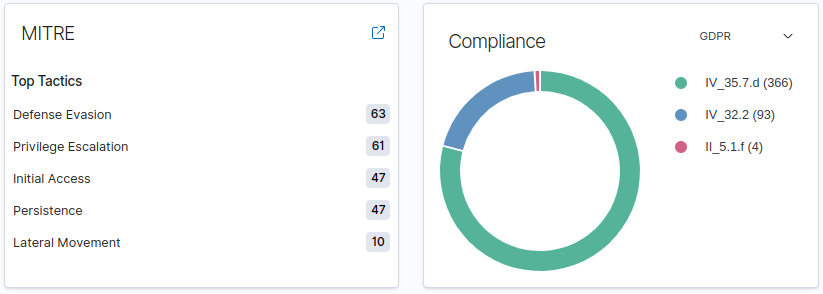
See example:
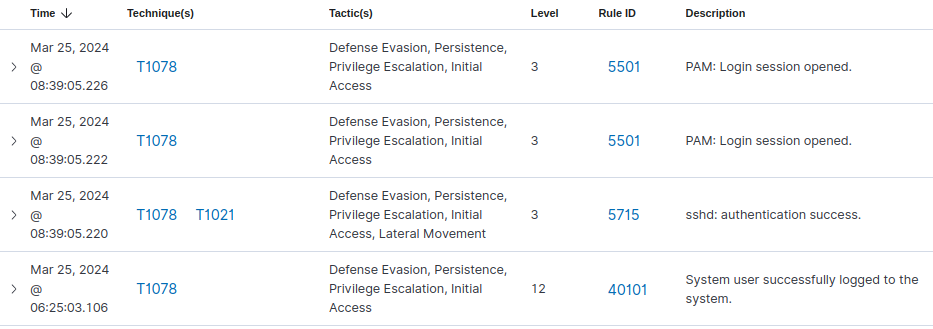
Note: it will flag a lot of false positives that will need a thorough understanding of the system and its applications to define what is normal operation from what needs investigation. For example, users/admin logins will be recorded as events. System patches will cause a massive number of events. And so on…
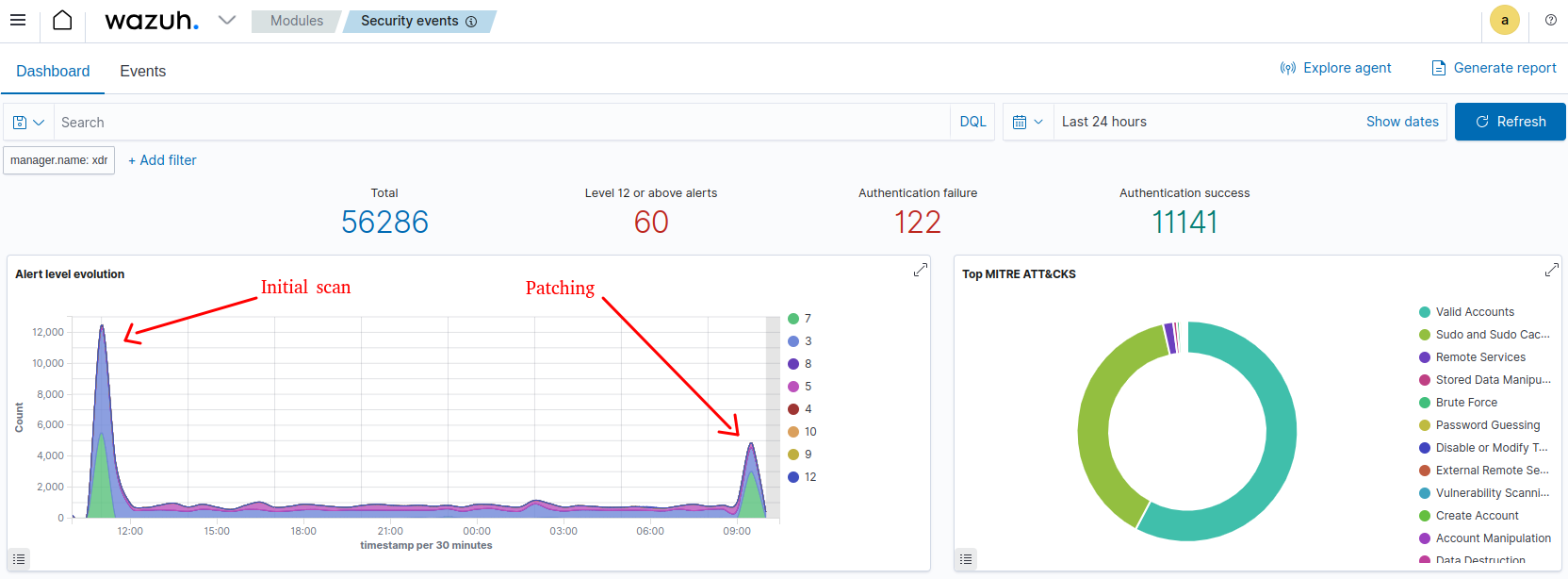
Here is where the real work starts!
BONUS
Wazuh started as a fork of OSSEC a long time ago. OSSEC looks like being under much slower development but is still popular and relevant in the cyber security universe [Link].
git clone https://github.com/ossec/ossec-hids.git cd ossec-hids sudo apt update sudo apt install libz-dev libssl-dev libpcre2-dev build-essential libsystemd-dev -y ./install.sh
Or using APT [Link].
wget -q -O - https://www.atomicorp.com/RPM-GPG-KEY.atomicorp.txt | sudo apt-key add - echo "deb https://updates.atomicorp.com/channels/atomic/ubuntu $DISTRIB_CODENAME main" >> /etc/apt/sources.list.d/atomic.list sudo apt update sudo apt install ossec-hids-server -y
For MS Windows endpoints (yes, some people use it), check out BLUESPAWN [Link]. It is another open-source EDR.