Red teaming is an authorised emulation of real attackers’ TTPs (Tactics, Techniques and Procedures) from MITRE ATT&CK, pretending to be a threat actor, and attempting intrusion against an organisation.
ATOMIC READ TEAM
Atomic Read Team is a tool that allow to easily run “fake” attacks based on known TTPs in order to test detection and prevention systems [Link]. It used a PoweShell module called Invoke-AtomicRedTeam to execute the desired attack’s procedure [Link].
Install Execution Framework Only
Install-Module -Name invoke-atomicredteam,powershell-yaml -Scope CurrentUser
Install Execution Framework and Atomics Folder
IEX (IWR 'https://raw.githubusercontent.com/redcanaryco/invoke-atomicredteam/master/install-atomicredteam.ps1' -UseBasicParsing); Install-AtomicRedTeam -getAtomics -Force
Importing the Module in the PowerShell Session
Import-Module "~\AtomicRedTeam\invoke-atomicredteam\Invoke-AtomicRedTeam.psd1" -Force
List Atomic Tests and Check Any
Invoke-AtomicTest All -ShowDetailsBrief Invoke-AtomicTest All -ShowDetailsBrief -anyOS
Invoke-AtomicTest T1016-8 -ShowDetailsBrief Invoke-AtomicTest T1016-8 -ShowDetails Invoke-AtomicTest T1016-8 -CheckPrereqs
Then, Execute!
Invoke-AtomicTest T1016-8 Invoke-AtomicTest T1016-8 -PromptForInputArgs Invoke-AtomicTest T1016-8 -Interactive
Other Options
Invoke-AtomicTest T1089 -Cleanup Invoke-AtomicTest T1218.010 -ExecutionLogPath 'C:\log.csv' Invoke-AtomicRunner -listOfAtomics .\testsList.csv -PauseBetweenAtomics 30
Start the Atomic GUI
Start-AtomicGUI
CALDERA
Caldera is an Automated Adversary Emulation Platform developed by MITRE [Link]. Its code can be found at [Link].
Both, Red and Blue teams can use this platform to install their Agents and monitor the operations occur.
Install and start Caldera on Kali
sudo apt install caldera -y caldera
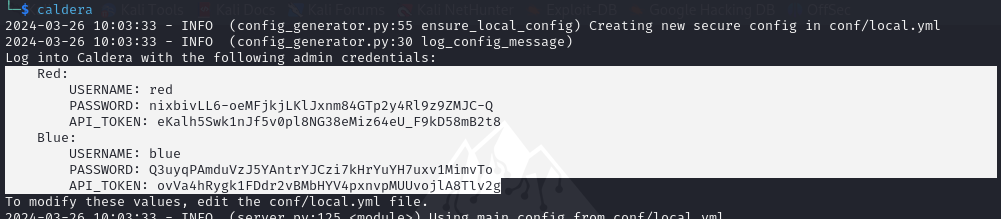
Note the credentials for both teams on the terminal:
Navigate to http://localhost:8888/.

Each team (Red and Blue) will have its own dashboard but they both look and work the same way:
Setup the Agents.
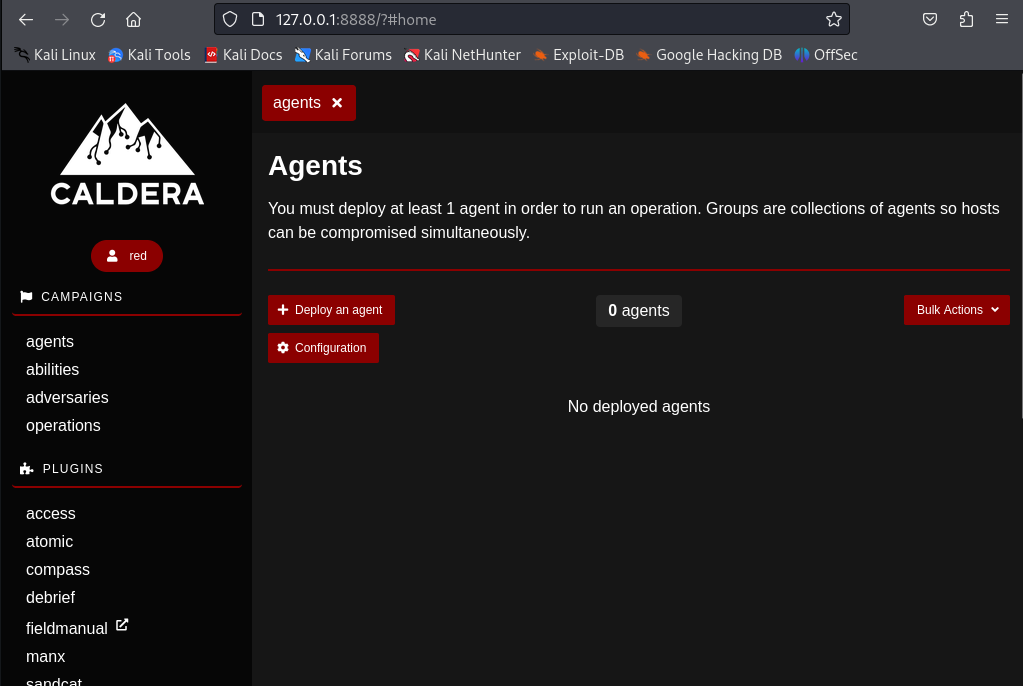
- Important points to setup:
- Select the Agent based on criteria like the desired communication protocol: TCP, HTTP, HTTPS, etc.
- Enter the IP or hostname of Caldera Server and make sure it is reachable from the Agents.
- It will produce multiple deployment commands that can copied and pasted on the end-points (Agents):
- Caldera’s default Red team’s agent,
- Blue team’s agent,
- With a randomised name for quick start in background,
- One that compiles in the end-point (requires GoLang),
- Another that uses GIST C2,
- And one that is capable of P2P communication.
Check the Adversary Profiles and define what will be emulated.
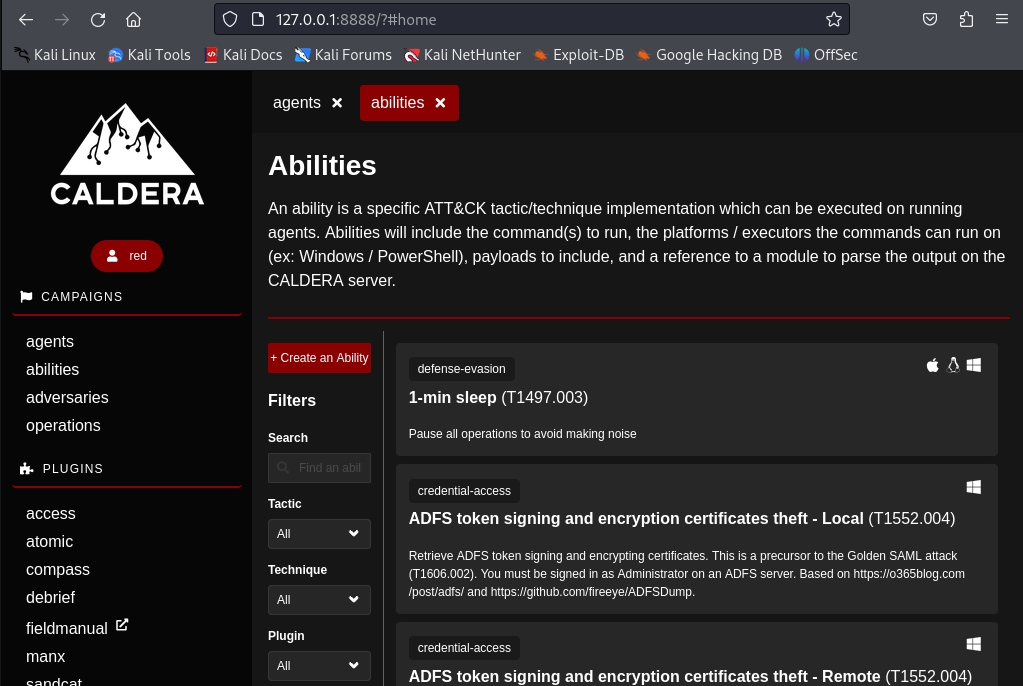
- Important points to setup:
- Re search the Abilities database for TTPs that match the organisation attach surface.
Create an Operation with the Adversary Profile chosen.
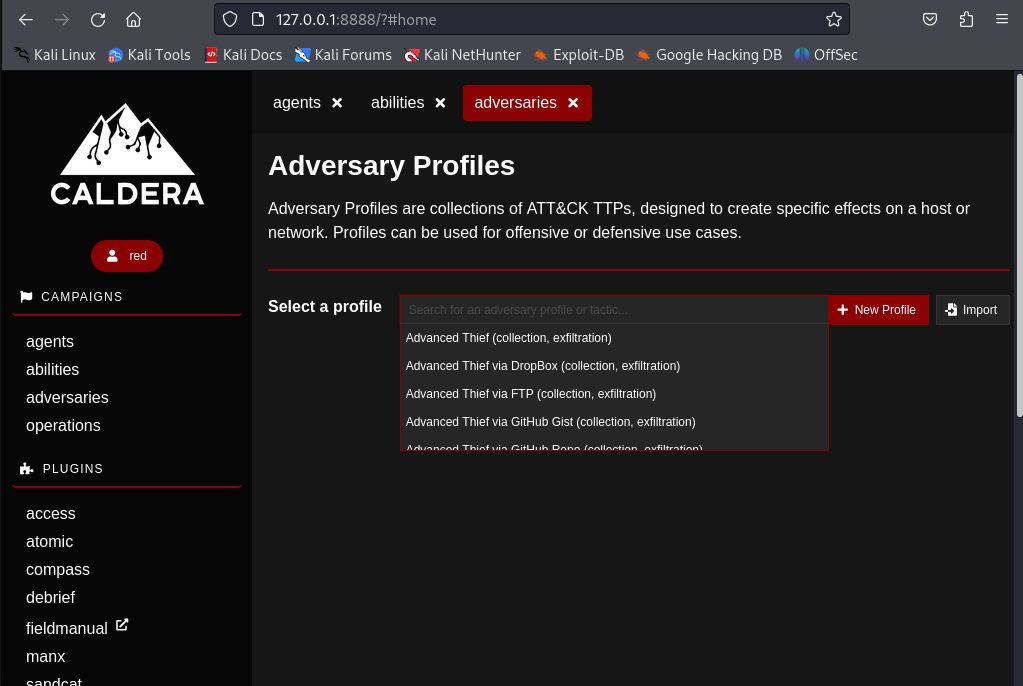
- Important points to setup:
- Study what adversaries are more likely to target your organisation or industry.
- The adversaries are based on real threat actors observer behaviours and their abilities.
- Study what adversaries are more likely to target your organisation or industry.
Create an Operation with the Adversary Profile chosen.
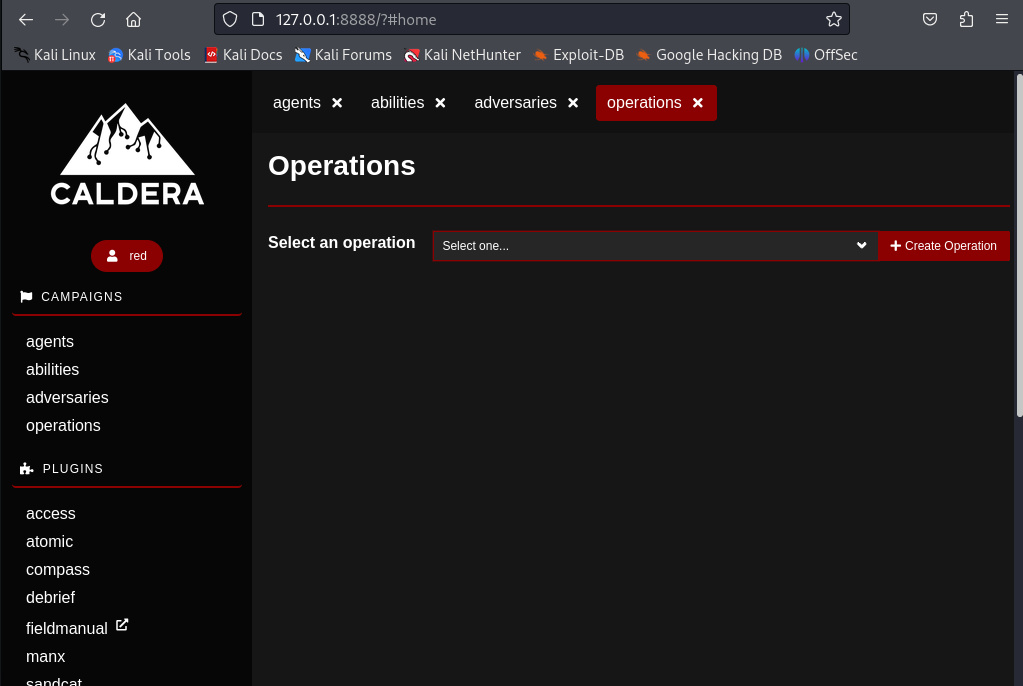
- Important points to setup:
- Create a new Operation and select the Adversary you want to emulate.
- Adjust the desired obfuscation level and how much noise it will cause in the network.
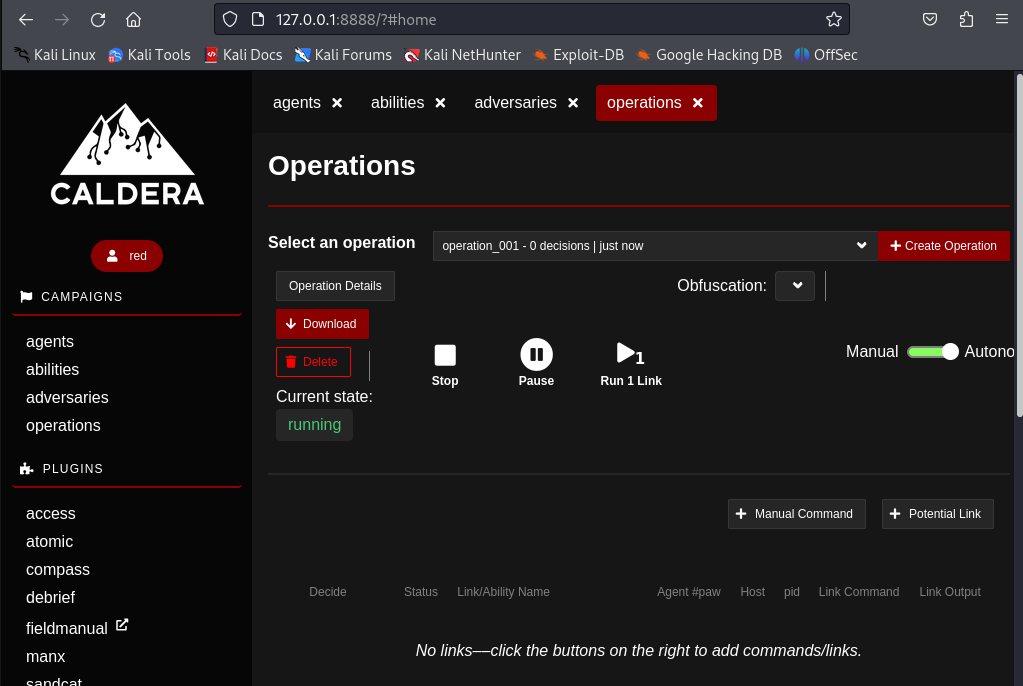
Now, monitor the operation as it unfolds.
BONUS
Run Atomic Red Team from a Container with:
docker run -it redcanary/invoke-atomicredteam:latest
Run Caldera from a Container with:
docker run -it -d mitre/caldera