REMnux is a Linux distribution based on Ubuntu 20.04 that offers a curated collection of free tools for reverse-engineering of malicious software, out of the box [Link].
It is distributed in many forms but the most popular is the Virtual Appliance format: self contained system (Linux distribution) that is built for dedicated purpose.
- After the deployment, create a snapshot or a template of the base instance (VM),
- Before every investigation, create a fresh clone from the base instance,
- After the investigation is completed, destroy the ephemeral clone or rollback to the snapshot taken.
WARNING: any malware investigation is risky. Do not even try if not absolutely secure that you master what you are trying to do. Network segregation and sandboxing is fundamental but totally our of the scope of this post.
DEPLOYING ON PROXMOX (PVE 8.1)
On the Web-UI:
- Create a VM:
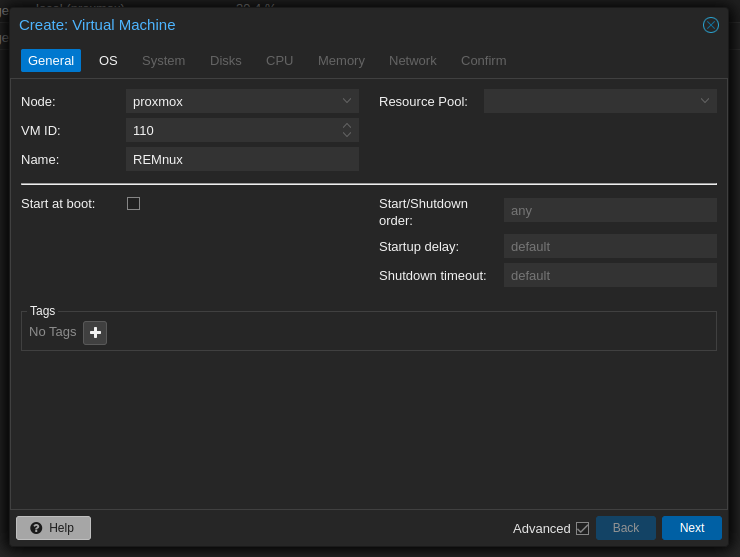
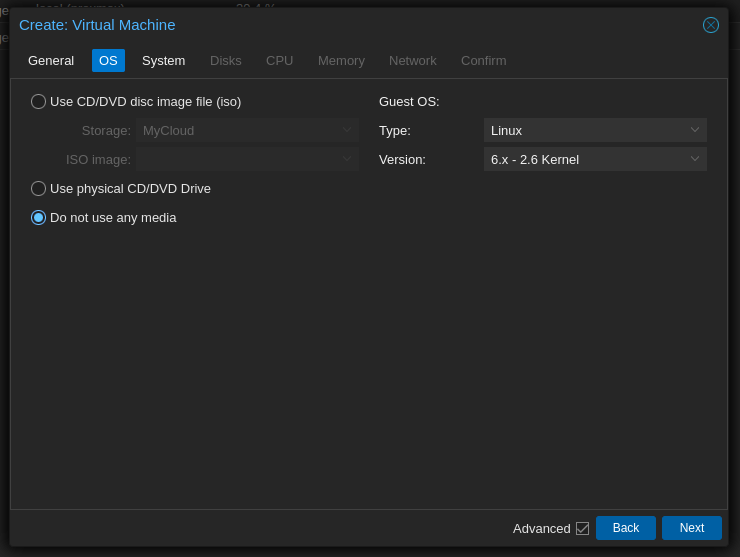
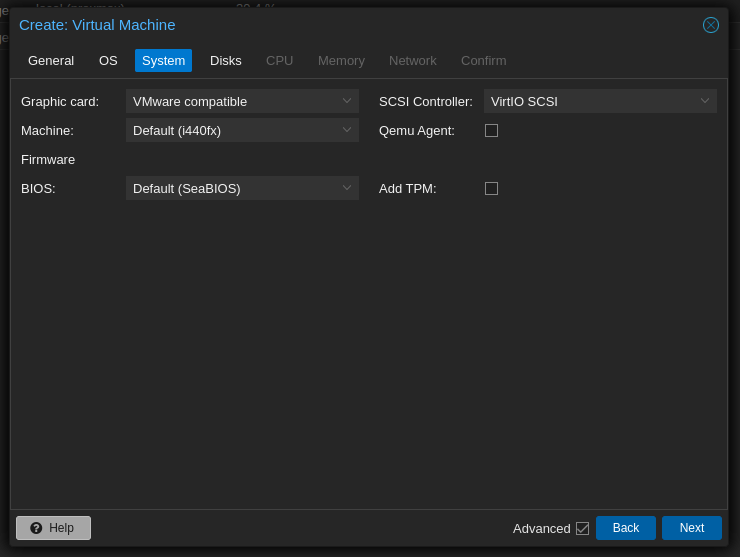
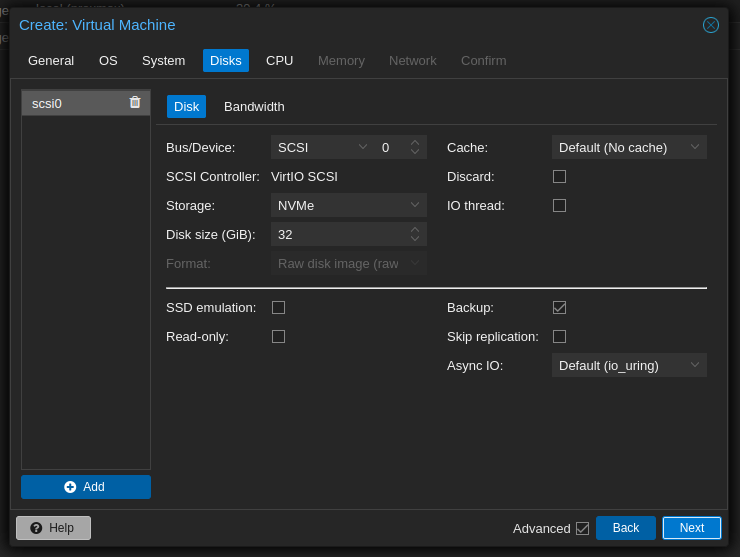
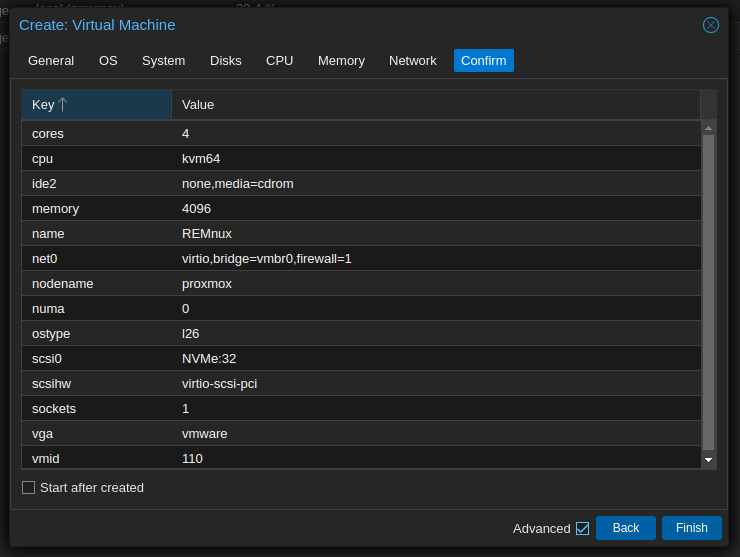
- Detach and Remove the Disk:
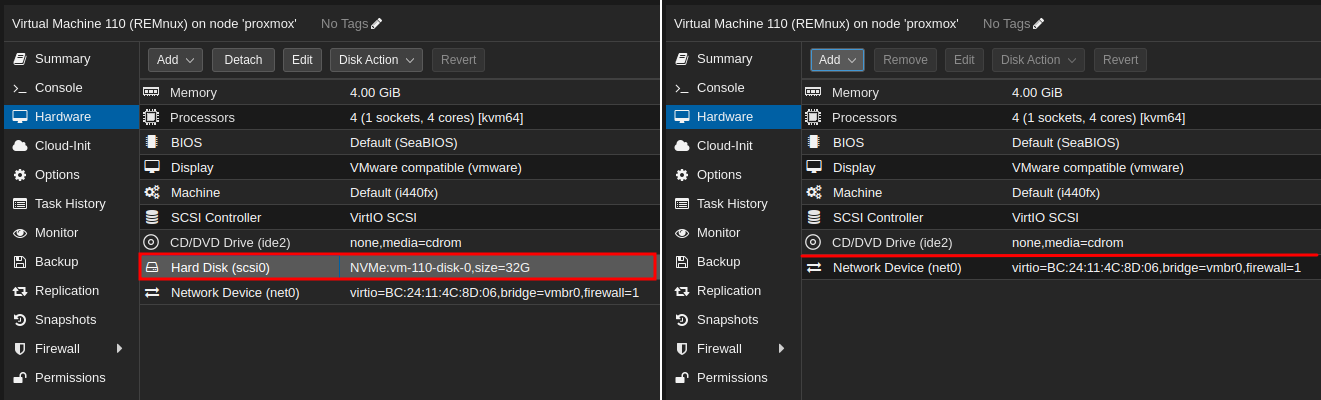
On a session as root:
cd /tmp wget "https://gigenet.dl.sourceforge.net/project/remnux/ova-general/remnux-v7-focal.ova" tar -xvf remnux-v7-focal.ova gunzip remnux-v7-focal-disk1.vmdk.gz qemu-img convert -f vmdk remnux-v7-focal-disk1.vmdk -O qcow2 remnux-v7-focal-disk1.qcow2 qm importdisk 110 remnux-v7-focal-disk1.qcow2 local-lvm rm /tmp/remnux-*
Note: Change the VM ID and local storage names accordingly.
On the Web-UI:
- Edit and Add the newly attached Disk:
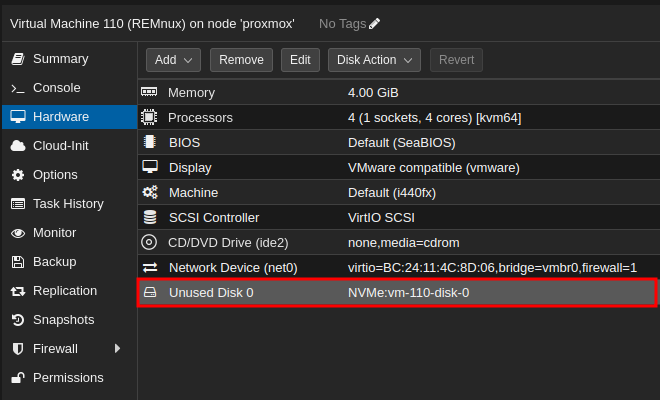
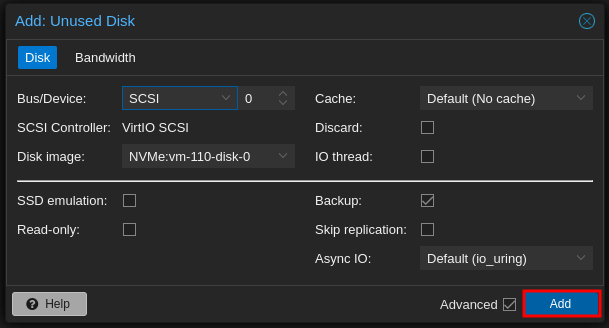
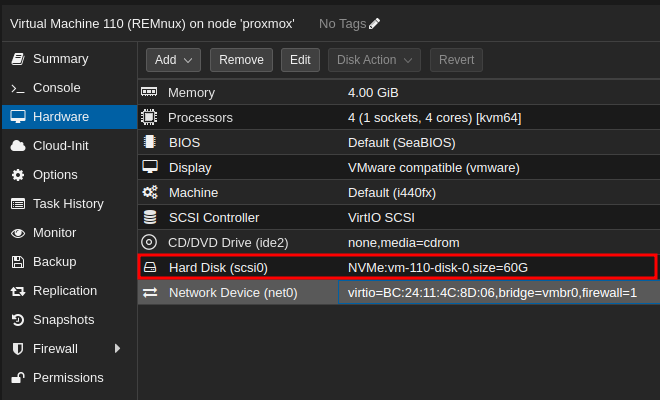
Note: mine says NVMe because that us the label I gave to my secondary storage.
- Enable to boot from the Disk:
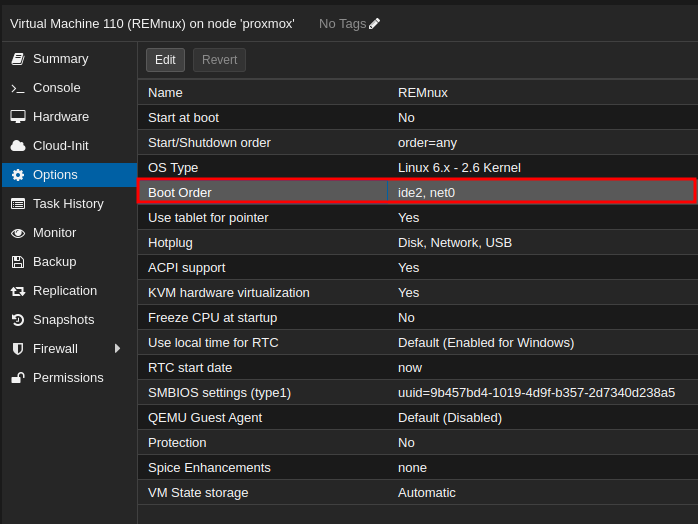
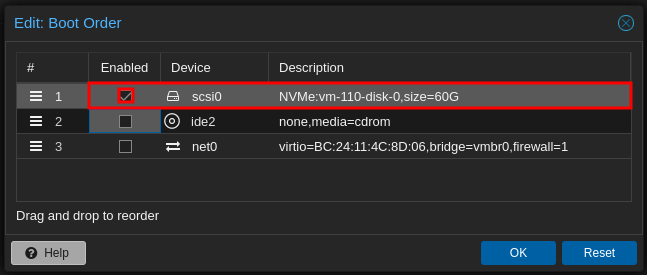
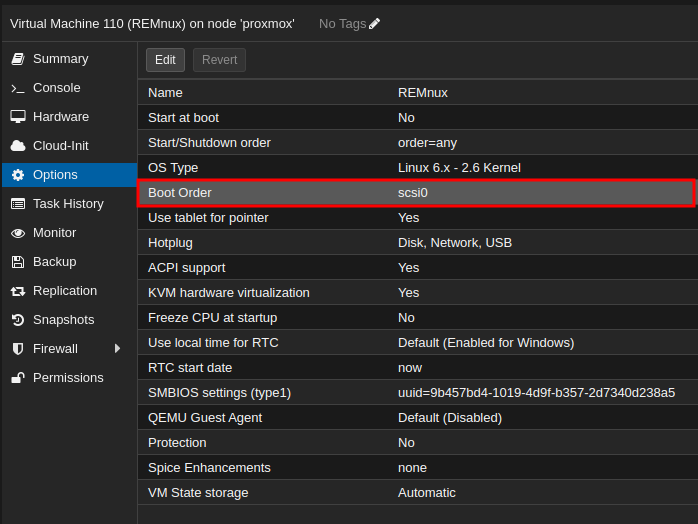
- Start the VM:

MANAGING REMNUX
Default credentials:
- Username:
remnux - Password:
malware
Note: consider changing the default password.
System updates:
sudo remnux upgrade sudo remnux update
In case of any issyes, try the following commands:
sudo apt update && sudo apt autoremove -y && sudo apt --fix-broken install
Network Connectivity
As any recent release of Ubuntu, it uses Netplan for managing the network configuration.
Identify the network interface’s name:
ipconfig -a
ip a
Remnux’s out of the box configuration might not match with the interfaces names assigned at the deployment. Change the configuration accordingly at:
sudo nano /etc/netplan/01-netcfg.yaml
Test then apply:
sudo netplan try sudo netplan apply
Disabling Wayland (back to old X11):
/etc/gdm3/custom.conf
WaylandEnable=false
sudo reboot
Running in the Cloud:
sudo nano /etc/remnux-config
- Change the mode from
dedicatedtocloud.
sudo systemctl enable ssh sudo reboot
Note: consider do not expose it directly to the internet if possible.
Other Useful Commands:
myip cabextract file.cab
USING REMNUX
In the suite of tools that come out of the box with REMnux you will find among others, tools for:
- Examine Static Proprieties and Deobfuscation of binaries,
- Windows Files
- TrID – reveals file signature.
- Yara Rules – identifies common malicious capabilities.
- ExifTool – reads and writes metadata.
- DroidLysis – static analysis of apk.
- zipdump.py – analyze compressed file.
- msitools – creates, inspect, and extract .msi files.
- re-search.py – searches for regular expressions of common suspicious artifacts in files.
- disitool – manipulate embedded digital signatures.
- Name-That-Hash – hash identification tool.
- Hash ID – hash identification tool.
- signsrch – finds patterns of common encryption, compression, or encoding algorithms.
- ssdeep – fuzzy hashes.
- wxHexEditor – hex editor.
- ClamAV – signature-based anti-virus.
- bulk_extractor – extract strings from files.
- Hachoir – view and edit binaries.
- Sleuth Kit – recovers files from disk.
- binwalk – extract and analyze firmware.
- Manalyze – static analysis of PE files.
- StringSifter – ranks relevance strings from PE files.
- PEframe – analyze PE and MS Office files.
- dllcharacteristics.py – reads and sets DLL characteristics of a PE file.
- PE Tree – examine structure of PE files.
- pedump – extracts PE files.
- pecheck – analyzes proprieties of PE files.
- pev – analyzes and extract PE files.
- PortEx – analyzes PE files.
- bearparser – parses PE files.
- debloat – remove junk contents from bloated PE files.
- Linux Files
- pyelftools – libraries for ELF and DWARF tfiles.
- .NET
- dnfile – shows static proprieties.
- dotnetfile – shows static proprieties.
- Deobfuscation
- Malchive – does static analysis of various aspects of malicious code.
- 1768.py – analyze Cobalt Strike beacons.
- cs-decrypt-metadata.py – decrypt Cobalt Strike metadata.
- CSCE – decrypts Cobalt Strike beacons.
- xortool – analyze XOR-encoded data.
- RATDecoders – Python3 library Decoder for RATs.
- DC3-MWCP – parses configuration information from malware.
- Chepy – Python library and command line tool for data transformation.
- Balbuzard – finds and deobfuscates patterns.
- xor-kpa.py – performs XOR plaintext attacks.
- NoMoreXOR.py – guesses a file’s 256-byte XOR by using frequency analysis.
- unXOR – deobfuscates XOR’ed files.
- brxor.py – bruteforces XOR’ed strings of English words.
- xorBruteForcer.py -ruteforce an XOR-encoded file.
- strdeob.pl – locates and decodes stack strings.
- ex_pe_xor.py – searches XOR’ed for indication of executable binaries.
- XORStrings – searchs for XOR encoded strings in a file.
- XORSearch – finds and decodes strings obfuscated using common techniques.
- FLOSS – extract and deobfuscate strings from PE executables.
- Windows Files
- Statically Analyze code from multiple languages and platforms:
- BinNavi – IDE for disassembled code.
- Ghidra – reverse engineering tool suite developed by the NSA.
- Cutter – reverse engineering platform.
- Detect-It-Easy – reveals file properties.
- Qiling – emulates code execution for a variety of OS and hardware platforms.
- Vivisect – examines and emulates binary files.
- objdump – disassembler.
- Bytehist – generate byte-usage-histograms.
- UPX – packs and unpacks PE files.
- Speakeasy – emulates code execution.
- binee – analyze I/O operations of PE files by emulating its execution.
- capa – detect suspicious capabilities in PE files.
- PyInstaller Extractor – extracts PyInstaller-generated PE files.
-
Decompyle++ – Python bytecode decompiler.
- ExtractScripts – extract scripts from HTML files.
- decode-vbe.py – decodes encoded VBS/VBE scripts.
- cfr – Java decompiler.
-
JAD Java Decompiler – Java decompiler.
- JD-GUI Java Decompiler – GUI Java decompiler.
- Java IDX Parser – analyze Java IDX files.
- Javassist – Java bytecode engineering toolkit/library.
- Procyon – Java decompiler.
- de4dot – deobfuscates and unpack .NET files.
- ILSpy – examines and decompiles .NET files.
- JADX – generate Java source code from .dex and .apk files.
- apktool – reverse-engineering for .apk files.
- DroidLysis – analyzes .apk files.
- androguard – examines .apk files.
- AndroidProjectCreator – converts a .apk back to Android Studio project.
- baksmali – disassembler for the .dex files.
- dex2jar – examine .dex files.
- Frida – trace the execution of a process.
- radare2 – examine binary files.
- shcode2exe – converts 32 and 64-bit shellcode to PE executable.
- shellcode2exe.bat – converts 32 and 64-bit shellcode to PE executable.
- scdbg – traces and analyzes shellcode execution.
- runsc – traces and analyzes shellcode execution.
- bddisasm – Bitdefender disassembler.
- SpiderMonkey – Mozilla’s standalone JavaScript engine for deobfuscating JavaScript.
- objects.js – deobfuscates JavaScript.
- STPyV8 – Python3 and JavaScript interop engine.
- JStillery – deobfuscates JavaScript scripts.
- box-js – analyzes JavaScript.
- Rhino Debugger – GUI JavaScript debugger.
- PowerShell Core – runs PowerShell on Linux.
- GNU Project Debugger – multi-language debugger.
- edb – AArch32/x86/x86-64 debugger.
- ltrace – traces library calls.
- strace – traces system calls.
- Perform Memory Forensics:
- Volatility 3 – memory forensics tool and framework.
- Volatility Framework – memory forensics tool and framework.
- linux_mem_diff_tool – uses Volatility to compare two memory images.
- AESKeyFinder – finds 128-bit and 256-bit AES keys in a memory image.
- RSAKeyFinder – finds BER-encoded RSA private keys in a memory image.
- Explore Network Interactions and System Interactions:
-
Burp Suite CE – web pentesting suite.
- Network Miner Free Edition – packet sniffer.
- PolarProxy – intercept and decrypt TLS traffic.
- CapTipper – HTTP sniffer.
- mitmproxy – MITM web proxy.
- tshark – packet sniffer.
- wireshark – GUI packet sniffer.
- tcpdump – packet sniffer.
- ngrep – finds patterns in network traffic.
- tcpxtract – extracts files from network traffic.
- tcpflow – analyzes network flow.
- tcpick – packet sniffer.
- Unfurl – deconstruct and decode data from a URL.
- thug – honeyclient for examining websites.
- Anomy – tunels wget, ssh, sftp, ftp, and telnet through Tor.
- EPIC IRC Client – sniffs IRC traffic.
- fakedns – responds DNS queries with fake IPs.
- dnsresolver.py – responds to DNS queries.
- fakemail – SMTP sniffer.
- accept-all-ips – intercepts traffic to all IPs.
- inspircd 3 – sniffs IRC traffic.
- INetSim – mulates common network services.
- FakeNet-NG – mulates common network services.
-
- Analyze Documents from many formats:
- Tesseract OCR – extracts optical character recognition from image files.
- peepdf – analyses PDF files.
- pdftool – identifies incremental updates to PDF files.
- pdf-parser.py – analyses elements of PDF files.
- pdfid.py – identifies suspicious elements in PDF files.
- SSView – analyses OLE2 structure storage files.
- oletools – analyzes OLE2 compound files.
- emldump – analyzes OLE2 compound files.
- msoffcrypto-tool – decrypts Microsoft Office files.
- msoffcrypto-crack.py – cracks passwords from encrypted files.
- pcodedmp – disassembles VBA p-code.
- pcode2code – decompiles VBA macro p-code.
- EvilClippy – modifies MS Office documents’ proprieties.
- XLMMacroDeobfuscator – deobfuscates XLM macros from MS Office files.
- ViperMonkey – emulates VBA executions for analysis.
- rtfdump – analyses RTF files.
- xmldump.py – extracts content form OOXML-formated documents.
- msoffice-crypt – encrypts and decrypts OOXLM documents.
- emldump – analyses EML files.
- msg-extractor – extracts attachments from MSG files.
- msgconvert – converts MSG to MBOX files.
- mail-parser – parses raw SMTP and MSG and generates objects.
- Others:
- Sysdig – exposes Linux system activities.
- ProcDOT – visualization for output of Process Monitor.
- sandfly-processdecloak – finds hidden processes in Linux.
- Unhide – reveals hidden processes and connections in Linux.
- Automater – gathers OSING information about IPs, domains, hashes, etc.
- dissect – a DFIR framework and toolset.
- ioc_parser – extracts IOC objects from security report PDFs.
- ioc_writer – library to create and edit OpenIOC objects.
- malwoverview – calls public APIs from malware data repositories like VirusTotal and HybridAnalysis.
- VirusTotal API – command line tool for interacting with the API.
- virustotal-submit – submits files for analysis by Virus Total.
- virustotal-search – searches for a hash in Virus Total’s database.
- shodan – command line tool for interacting with the API.
- PyPDNS – library for querying online services that provide Passive DNS and IP address lookup.
- pdnstool – queries Passive DNS online databases.
- DeXRAY – extracts and decodes data from antivirus quarantined files.
- Scalpel – carves contents from binaries and disk images/partitions.
- nsrllookup – look for the MD5 of files in the NIST database.
- Yara – identifies and classifies malware samples based on the YARA rule-based approach.
- VBinDiff – compared binary files.
Enumerate all the tools related to the investigation and try them all out. Each tool may provide a different perspective. Additional tools might eventually needed in special cases.
BONUS
RENmux Alternative Installations
- Docker container:
-
sudo docker run --rm -it -u remnux remnux/remnux-distro:focal bash sudo docker run --rm -it -u remnux -d -p 22:22 -v /LOCAL/PATH:/home/remnux/files remnux/remnux-distro bash
-
- Or on an existent system:
-
wget https://REMnux.org/remnux-cli chmod +x remnux sudo mv remnux /usr/local/bin sudo apt install gnupg curl -y sudo remnux install sudo reboot
-
- Or install it from scratch (too much work!)
- Or even on the Cloud.
For those who use Kasm Desktops, try it out as a disposable desktop workspace.
Malware Analysis on Windows
Checkout FlareVM if you need to prepare an existent Windows VM for malware analysis [Link]. It is a collection of software installations scripts created by Mendiant.
Managed Cloud Hosted Malware Analysis Platform
For an easy malware analysis experience with no infrastructure setup and lots of statistic and open-source intelligence, check out ANY.RUN [Link].