IP Tables uses the filter to act as a firewall but also controls the routing of packets on Linux.
A table in IP Tables is a collection of chains for a particular networking function.
- Filter Table (Firewall)
- Input Chain
- Output Chain
- Forward Chain
- NAT Table
- Output Chain
- Prerouting Chain
- Postrouting Chain
- Mangle Table
- Input Chain
- Output Chain
- Forward Chain
- Prerouting Chan
- Postrouting Chain
Chains are the tags that define and match packets to their state.
- iptables -L
- List rules.
- iptables -L –line-numbers
- List rules numbered.
- iptables -D INPUT
- Delete rule from the INPUT chain.
- iptables -F
- Flush all the rules.
- iptables –policy INPUT ACCEPT
- Set default policy to accept.
- iptables –policy INPUT DROP
- Set default policy to drop.
- iptables -I -s 1.1.1.1 -j ACCEPT
- Insert rule to the top.
- The rule will allow connections from the IP.
- iptables -A -s 1.1.1.0/24 -j DROP
- Append rule to the end.
- The rule will allow connections from the Network.
- iptables -I INPUT -p tcp –dport 80 -j DROP
- Block connections to a port.
- iptables -I OUTPUT -tcp –dport 443 -j DROP
- Drop outgoing packets to destination port.
- sudo iptables -t nat -L -n -v –line-numbers
- Listing all rules in the NAT table with numbers.
- sudo iptables -t nat -D PREROUTING 10
- Deleting rule number 10 from NAT table and PREROUTE chain.
- iptables -I INPUT -p tcp –dport -j REJECT –reject-with tcp-reset
- Helps to prevent enumeration by sending a response when instead of dropping the packet, making the result of the scanning less accurate and less reliable.
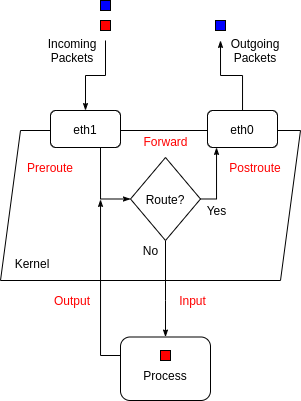
Chain Traversal for Incoming Traffic.
- PREROUTING -> INPUT
- Inbound traffic to the host.
- PREROUTING -> FORWARD -> POSTROUTING
- Traffic routed through the host.
- PREROUTING -> OUTPUT -> POSTROUTING
- Outbound traffic from the host.
CREATE PERSISTENCE
sudo /sbin/iptables-save | sudo tee /root/iptables-rules.v4 sudo apt install iptables-persistent -y
Or create the file /etc/rc.local and add the lines of configuration:
#!/bin/bash sudo iptables -t nat -A PREROUTING -i ens5 -p udp --dport 1144 -j DNAT --to 10.8.0.2:1144 sudo iptables -t nat -A PREROUTING -i ens5 -p tcp --dport 49152:49159 -j DNAT --to 10.8.0.2:49152-49159 exit 0
FLUSHING ALL TABLES AND DELETING ALL CHAINS
sudo iptables -t filter -F sudo iptables -t filter -X sudo iptables -t mangle -X sudo iptables -t mangle -F sudo iptables -t raw -X sudo iptables -t raw -F sudo iptables -t security -X sudo iptables -t security -F sudo iptables -t nat -X sudo iptables -t nat -F