SELinux is an upgrade to the file system that creates labels to enhance the policies for groups and users.
Created by Red Hat and the NSA it also comes natively in CentOS and Fedora but can be installed in any other Linux and Unix distributions because it uses Kernel security modules.
Install the packets:
sudo apt update sudo apt install policycoreutils selinux-utils selinux-basics -y
Check the status and activate:
sestatus sudo selinux-activate sudo reboot
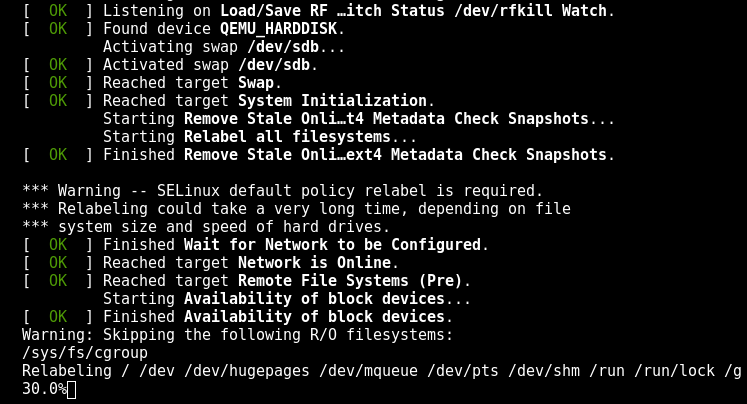
Then it will reboot automatically one more time.
By default, it will be permissive when enabled.
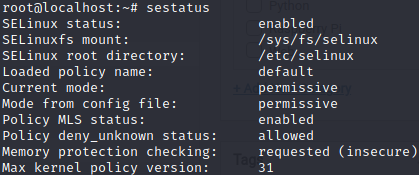
The permissive mode will allow the applications to access the file even if it is not labeled accordingly but it will log everything.
Enforcing will restrict access based on the labeling policy of SELinux.
sudo selinux-config-enforcing sestatus
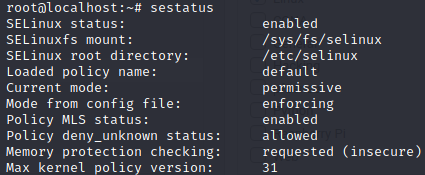
The following commands can get the current mode and set the current mode:
getenforce setenforce setenforce 0
The mode can also be defined in the configuration file:
sudo nano /etc/selinux/config
The configuration file can be also modified by following the commands:
sudo sed -i 's/SELINUX=.*/SELINUX=enforcing/' /etc/selinux/config
sudo sed -i 's/SELINUX=.*/SELINUX=permissive/' /etc/selinux/config
sudo sed -i 's/SELINUX=.*/SELINUX=disabled/' /etc/selinux/config
By listing the content of the directory the labels can be seen for each file:
ls -Zd
Change the label:
semanage fcontext -a -t FILE_TYPE "/web"
For a webserver, the FILE_TYPE would be httpd_sys_content_t.
Apply the changes:
restorecon -Rv /web
Checking the log messages:
grep AVC /var/log/messages
AVC (Access Vector Cache) can be understood as Access Violation.
Another way is to look for Alerts on the same file:
grep sealert /var/log/messages
Then copy and execute the command relative to the alert you want more details, for example:
sealert -l askjc1c63deb-2af3-9d23-a3247a234ab34
Note that files created will inheritance the labels from the parent directory. In the case of moving files, they will maintain the labels and will require to be re-labeled.
Keep the system in permissive mode, check the logs, and apply all the necessary labels according to the applications running.
In conclusion, SELinux requires a lot of work labeling all the file-system before enabling enforcing mode. Otherwise, it will crash many applications and possibly the system itself.
SE Linux is embedded in RHEL-based distributions and the installation of it on a Debian-based distribution looks simple but might create side effects and needs to be done very carefully.
A native alternative for Debian-based dist that is not embedded but runs as a service is called AppArmor and may have a similar security feature. Read more about it at [Link].
Check out Seccomp too. It can sandbox the applications to prevent a vulnerability in it to protect the pode/node/cluster of a Kubernetes environment, for example. It uses a profile to allow/deny permissions in order to restrict the process to the scope to the namespaces the app can see (as granular as per system call). Not too different but simple than apparmor and much simple than selinux but same concept.