OSV-Scanner is a command-line open source tool developed by Google Open Source Security Team to enumerate and check open-source dependencies for known vulnerabilities [Link].
It uses an aggregator of vulnerability database of those that adopted the OSV schema, including GitHub Security Advisories, PyPA, RustSec, and Global Security Database [Link].
Some of the 16 currently the available ecosystems are:
- Alpine
- Android
- crates.io
- Debian
- Go
- Linux
- Maven (Java, C#, C++)
- npm (JavaScript)
- NuGet (C#)
- OSS-Fuzz
- Packagist (PHP)
- PyPI (Python)
- RubyGems (Ruby)
INSTALLING ON UBUNTU 22.04
Environment
sudo apt update && sudo apt install golang-go -y && go version
Application:
go install github.com/google/osv-scanner/cmd/osv-scanner@v1
USING THE SCANNER
cd ~/Documents/ git clone https://github.com/nette/nette.git ~/go/bin/osv-scanner -r ~/Documents/nette
The output looks like as follows (I manually added few dependencies to the clean copy of the repository to provide some example):
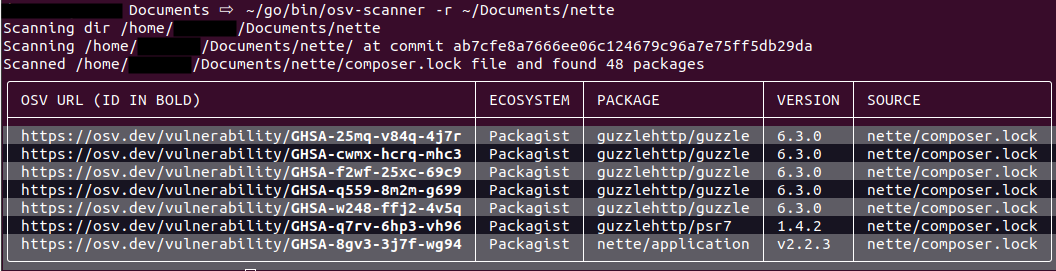
It can also scan based on SBOM or Lockfiles:
osv-scanner --sbom=sbom.json osv-scanner --lockfile=lock.json osv-scanner --docker image_name:latest