Whonix is a privacy-focused operating system that aims to provide users with the highest level of privacy and security possible.
It is designed to be used in conjunction with the Tor network, a decentralized network that protects users’ online privacy by routing their internet traffic through multiple servers.
Why Proxmox and not VirtualBox as it offers out of the box?
- Because Proxmox does not require a host operation system such as Windows, Mac, Linux. It can run on a bare metal headless host.
Why Whonix CLI and not the one with graphic interface?
- Because there is no reason to have a GUI on a gateway that will be headless 100% of the time. It will reduce RAM and CPU overhead.
Why Whonix and not OpenWRT or Pfsense?
- Whonix will enforce all traffic through Tor network and is conceptually designed to minimise (potentially eliminate) the risk of leaks.
BASIC STEPS
- Download Whonix
- Import to VirtualBox
- Complete installation and Test
- Export only the Gateway
- Copy the disk to Proxmox
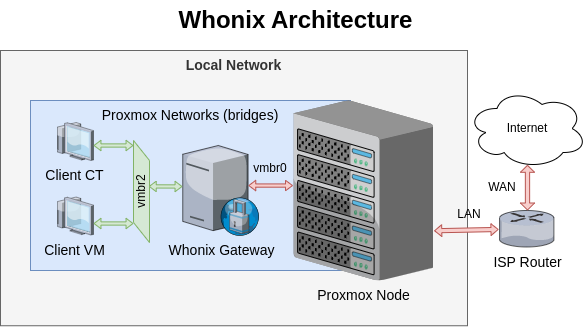
- Configure Proxmox Networks (create vmbr2)
- Manually create a VM in Proxmox
- Convert and attach the disk to the VM
- Attach the second network to the VM (vmbr2)
- Configure VM’s boot sequence
- Configure Whonix network interfaces (vmbr0)
- Run a client VM or container (to vmbr2)
DOWNLOAD
Download the OVA (Open Virtualization Format) file from the official repository [Link].
Alternatively, the version with GUI could also be downloaded. I don’t see why not.
IMPORT TO VIRTUALBOX
This step is not mandatory but provides an opportunity to finish the installation, accept terms of services, test, and so on.
Go to VirtualBox Manager > File > Import Appliance…
Click on Next then Import.
Accept both terms, of course.
Both VMs will be deployed effortless. Start them.
COMPLETE INSTALLATION AND TEST
Log in on both. Some people may say you should do the Gateway first then the Workstation. Up to you!
The default credentials are user and changeme. As one may guess, change it as soon as you can
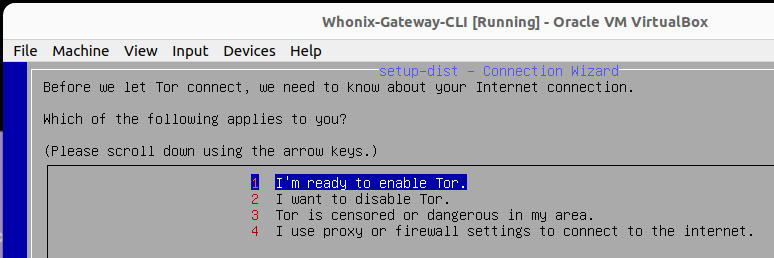
On the Gateway VM, select the option according to your reality. For most, the option 1 will be the one.
The completion of the setup might take several minutes.
Testing the Gateway
curl http://ip.me
The output must be an IP that is different to your real IP because it is reaching the internet through a random Exit Node of the Tor network.
This is a good time to change your password and fully update the gateway.
passwd
sudo apt update && sudo apt upgrade -y
Testing the Workstation
curl http://ip.me
Same type of result is expected. Power of both VMs.
sudo shutdown now
EXPORT WHONIX GATEWAY
Go to VirtualBox Manager > File > Export Appliance… > Select Whonix-Gateway-CLI.
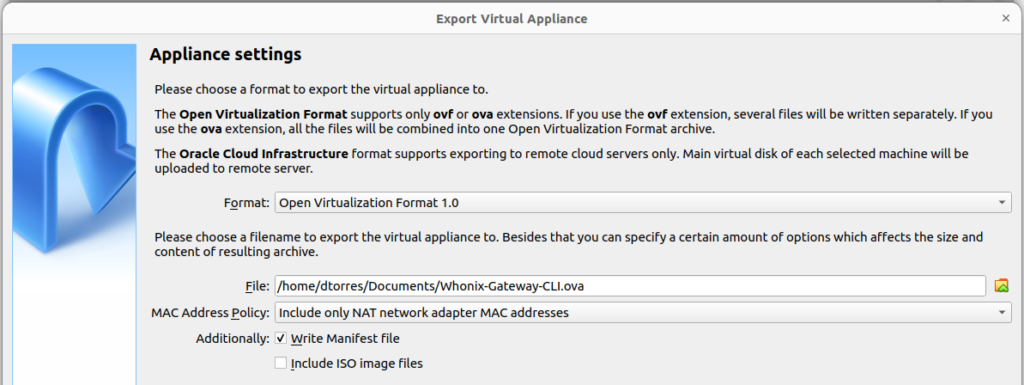
Click on Next, then Export.
When completed, both Whonix VMs can be removed and files deleted.
COPY THE DISK TO PROXMOX
The OVA files is similar to a TAR or a ZIP file. Extract all the files from the newly exported OVA:
tar xvf Whonix-Gateway-CLI.ova
Open a temporary web server from the directory where the OVA was extracted to.
python3 -m http.server 8080
Alternatively, scp (SSH) can also be used to copy the file over.
On Proxmox Shell, download the disk file over. Make the necessary adjustments to the URL if needed.
wget http://10.10.10.10:8080/Whonix-Gateway-CLI-disk001.vmdk
PROXMOX NETWORKS
Go to the Proxmox Node (pve) > System > Network > Create > Linux Bridge.
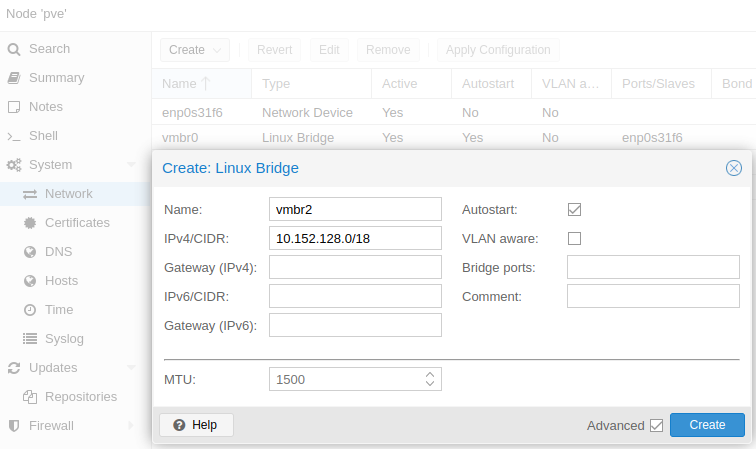
Click on Apply Configuration.
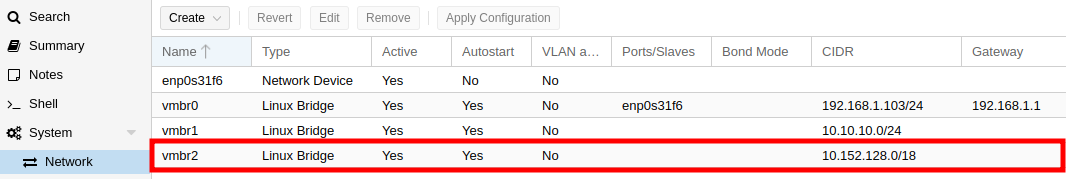
Note that the new bridge does not contain a Gateway nor is attached to any physical port.
CREATE VIRTUAL MACHINE
Click on Create VM on the desired node. The process of manually creating a virtual machine in Proxmox does not need any special setup.
Since the exported VM from VirtualBox had a SATA disk type, I wanted to have the same bus and device number to prevent any mismatch.
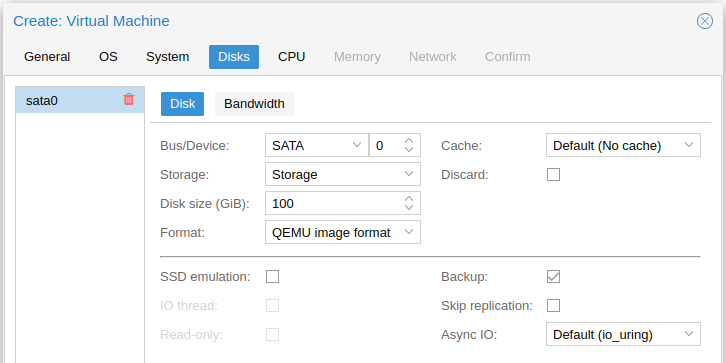
As one can see on the summary of the VM being created, it does not require more than 512 MB of RAM and 2 CPU cores.
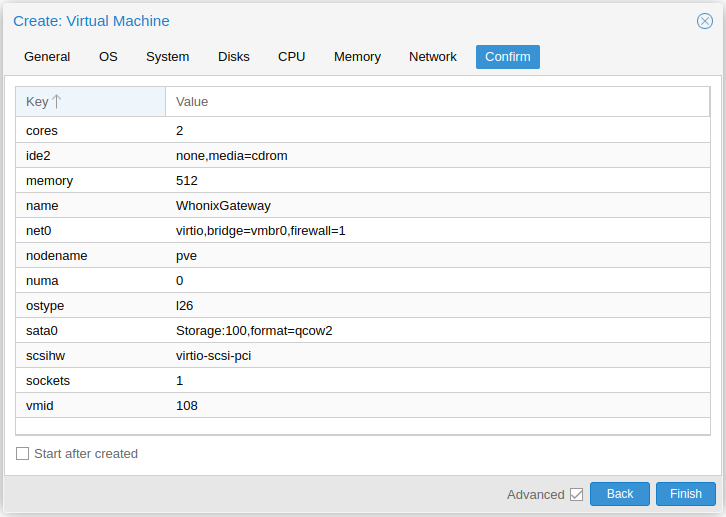
Click on Finish.
ATTACH THE DISK
On Proxmox Shell, from the location where the disk was previously downloaded, issue the following commands.
qm importdisk 109 Whonix-Gateway-CLI-disk001.vmdk local-lvm -format qcow2
Note: customise the VM number and the storage location accordingly.
The original VMDK file can be deleted now or kept for further usage.
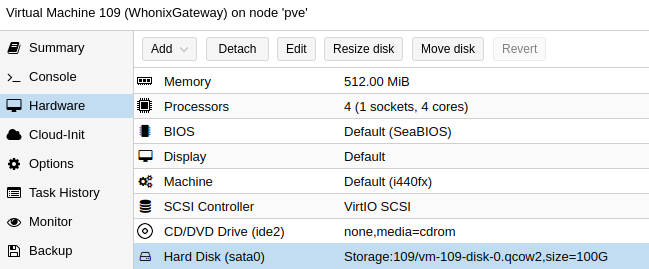
Go to WhonixGateway > Hardware > select Hard Disk (sata0) > click on Detach > click on Remove > double-click on Unused Disk 0 > select SATA > click on Add.
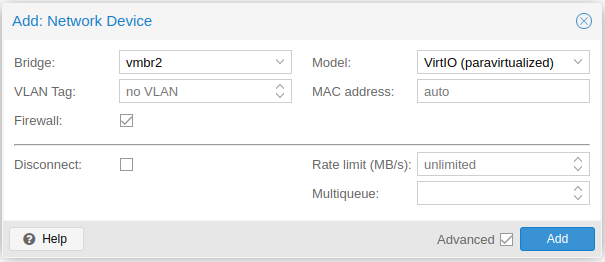
ATTACH SECOND NETWORK
On the same Hardware configuration, click on Add > Network Device > select vmbr2 > click on Add.
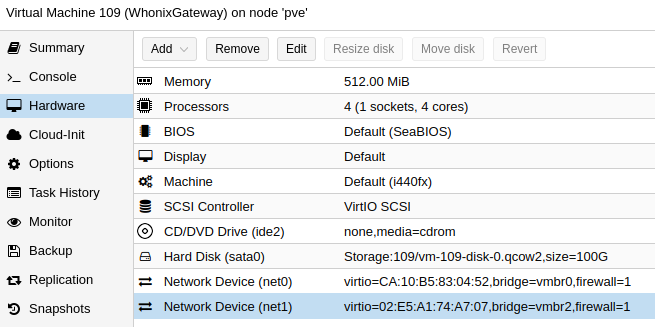
This is how it will look like:
BOOT SEQUENCE
Go to Options > select Boot Order > click on Edit > check only sata0.
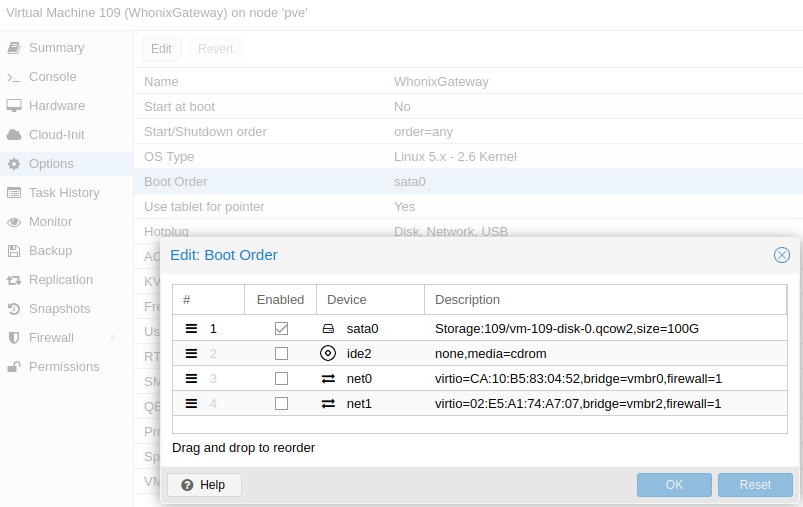
Click OK.
CONFIGURE NETWORK INTERFACE
Start the VM and open the Console.
If everything went well, you might see the bootloader and the VM will be up in few seconds.
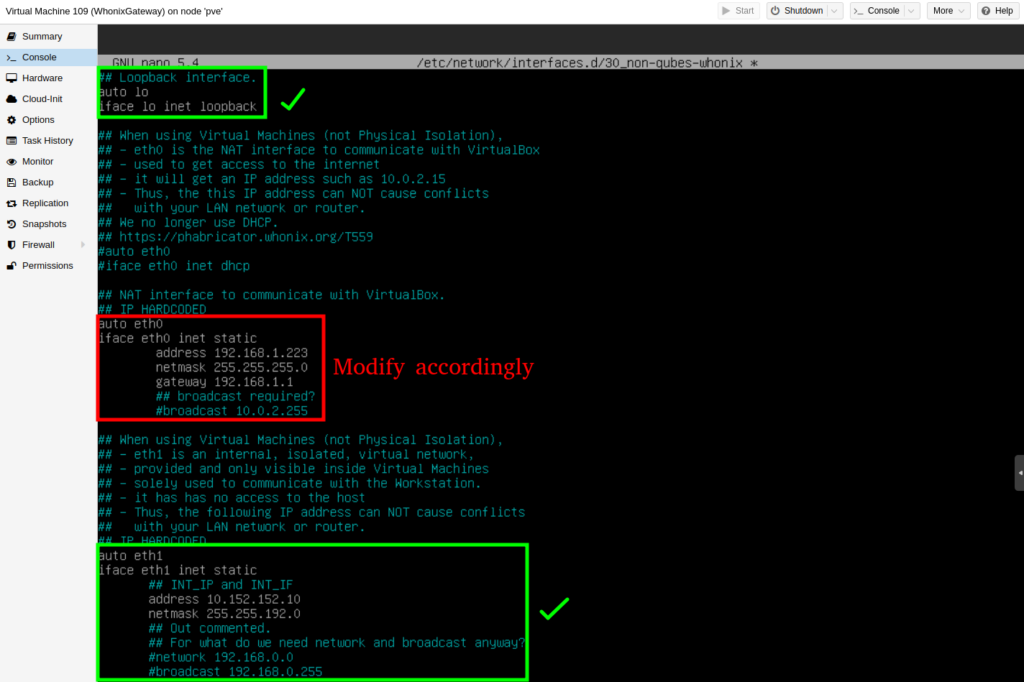
sudo nano /etc/network/interfaces.d/30_non-qubes-whonix
The eth0 interface is the public side of the Whonix gateway. And the eth1 is the private side.
On the private side, no changes are required, but on the public side it needs to have hard-coded an IP that is not in use from your local network.
For some reason, Whonix does not allow DHCP. So make sure you pick ne IP that is out of the rance of your LAN’s DHCP Server leasing range.
Reboot the VM.
sudo reboot
Then test for Internet connectivity.
sudo apt update
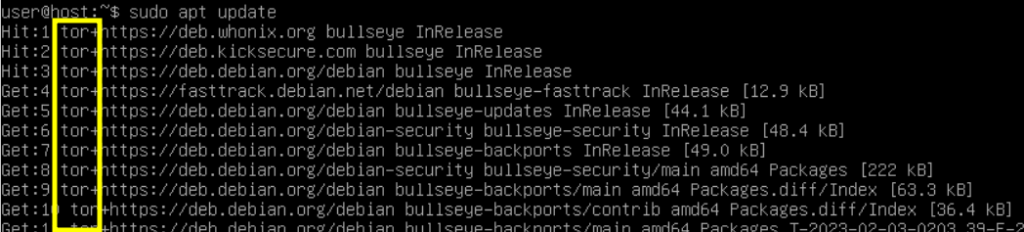
Note: the repositories are being reached through Tor. Worked!
RUN A CLIENT ON THE SECONDARY NETWORK
Attach any client VM or CT to the secondary isolated network vmbr2 and start it.
Out-of-the-box it will not work. It is because Whonix Gateway does not provided an IP to the clients. It has to be done manually too.
Use the Console to configure the network interface. I my case, I deployed a Debian Container:
nano /etc/network/interfaces
auto lo
iface lo inet loopback
auto eth0
iface eth0 inet static
address 10.152.152.11/18
gateway 10.152.152.10
reboot
Test it for connectivity. All your traffic is now anonymous!
BONUS
Have you heard about Qubes OS [Link]. While Whonix + Tails are privacy focus and exclusively access the internet though Tor, while Qubes OS has a security driven focus by compartmentalization between virtual machines.
Qubes OS is a hypervisor type 1 based on Xen Project that isolates workloads for maximum security and reliability weather running production + development environments or safely analyzing malware without infecting other systems.