While Linux is not a direct descendant of any particular version of Unix, it was inspired by Unix and designed to be similar to Unix in many ways.
Unix is a family of multi-user, multitasking operating systems that is known for its portability, scalability, and stability. It is the foundation of macOS, by the way.
BSD stands for Berkeley Software Distribution, which is a Unix operating system, and this acronym is carried over to name popular distributions FreeBSD and OpenBSD that will be introduced in this post.
FreeBSD [Link] and OpenBSD [Link] are well-known for performance, stability, and security. The main ideological difference is the license, where FreeBSD allow forks to be proprietary and OpenBSD enforces the same original license of being public to any derivation.
Minimum requirements:
- FreeBSD
- CPU: 1 core
- RAM: 1 GB
- Storage: 2 GB
- OpenBSD
- CPU: 1 core
- RAM: 64 MB
- Storage: 1 GB
The main difference that reflect on the amount of resources each distribution used is the amount of modules that come pre-installed. OpenBSD is more minimalistic and only comes with the bare minimum out of the box, while FreeBSD comes with a collection of features.
Note: TrueNAS (FreeNAS), pfSense, and OPNsense are based on FreeBSD.
INSTALLATION
For Linux users, the CLI installation of both distributions might not be a big deal and it all depends on the environment and what the system will be used for.
The ISO image will provide the most flexible installation source because it contains wider variety of hardware drivers but if it is going to be running a specific hardware such as a SBC (like Raspberry Pi) or as a VM, there are tailored images from them too.
- FreeBSD
It’s installation is straight forward and does not offer much challenge to a Linux user.
- OpenBSD
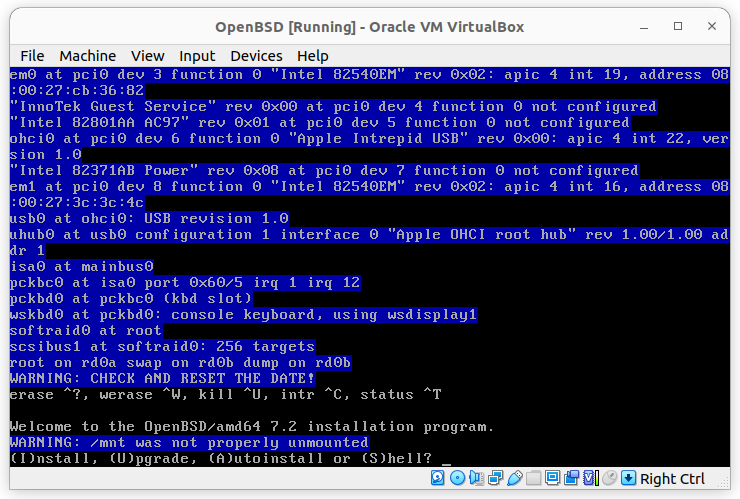
Don’t expect anything fancy on OpenBSD, it is not pretty or friendly.
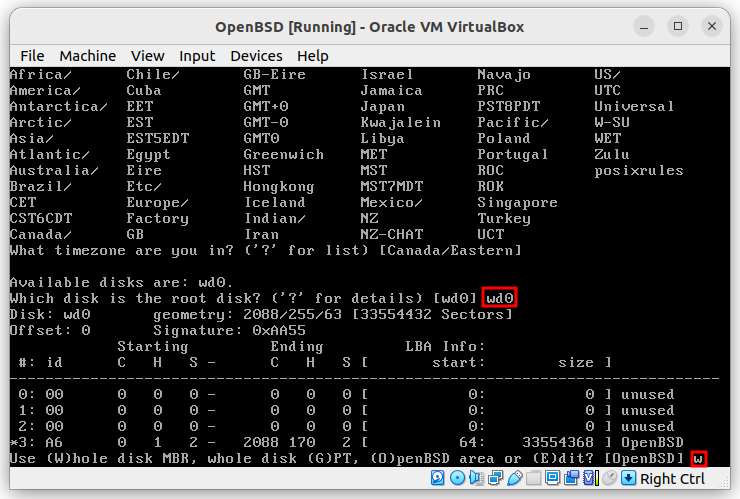
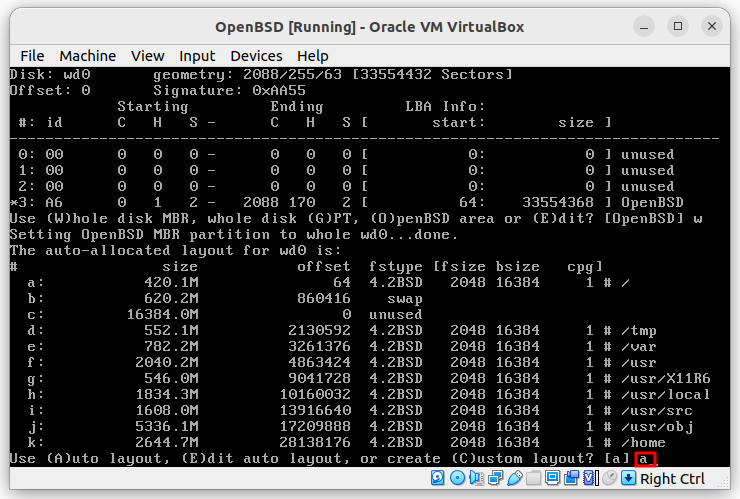
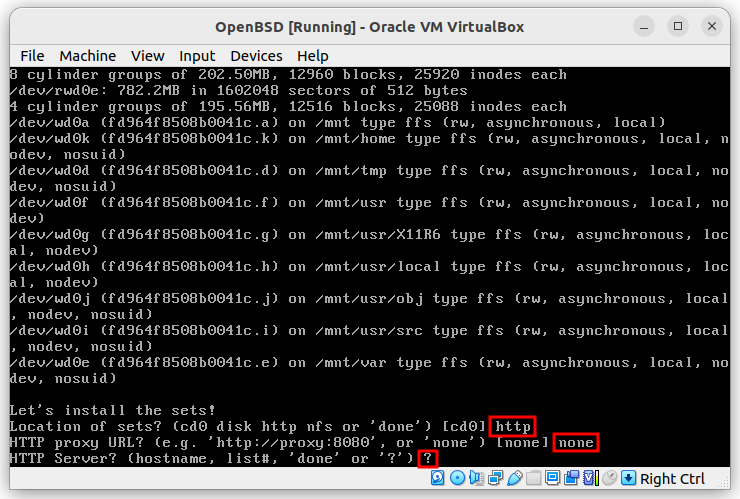
When you see the following screen, don’t panic! That is how it looks.
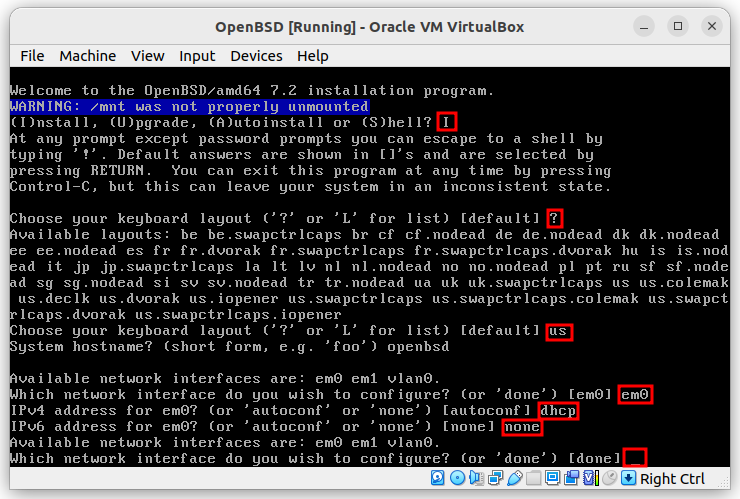
Follow the steps:
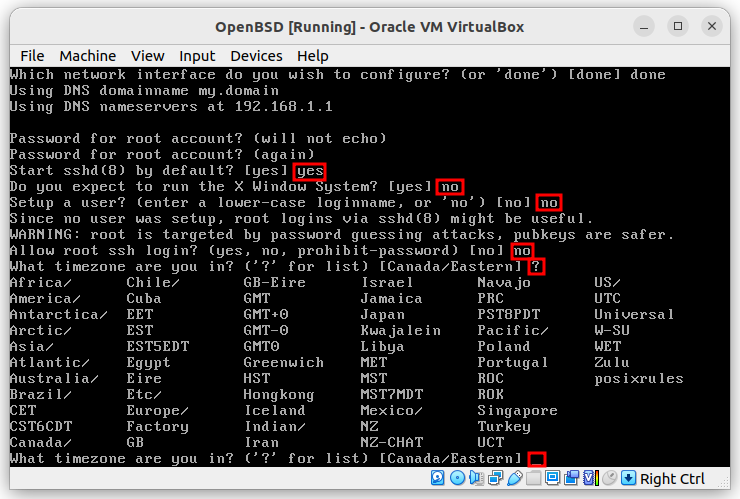
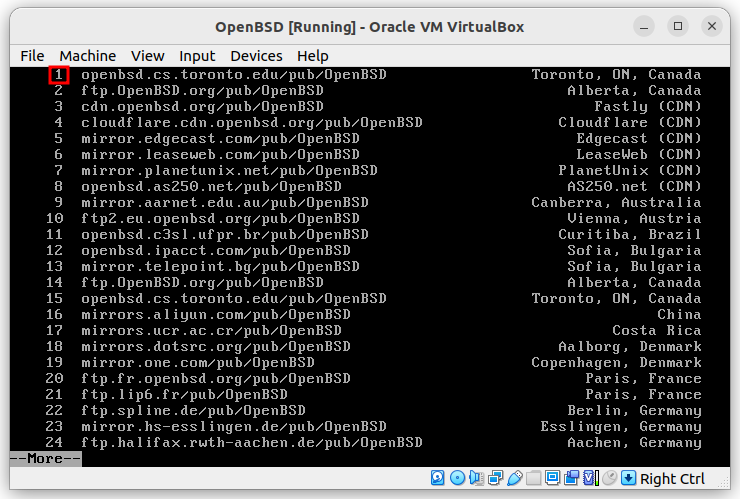
They are sorted by latency after a ping test. It is recommended to use the first.
Remember to remove the installation media or it will keep prompting to start the installation on boot.
FIRST ACCESS
Log with the root credentials set during the installation.
First of all, how to reboot and shut it down.
reboot
shutdown -p now
If not informed -p it will not power off after shutdown, like if you only issue the command halt.
List processes.
ps aux top
UPDATING, UPGRADING, AND INSTALLING PACKAGES
Regular package manager update and upgrade all its packages.
For FreeBSD:
pkg update && pkg upgrade
For OpenBSD:
pkg_add -Uu
Audit the vulnerable installed packages (FreeBSD only).
pkg audit -F && pkg audit
Fetch and install system updates (FreeBSD only).
freebsd-version freebsd-update fetch install
Before it install the updates the vi file editor with some output for review and approval. It is not expected by Linux users, so take time to read and understand before proceeding with the installation if in a production environment. A reboot is always recommended right after.
There is no nano but vi gets the job done for those who like it. I don’t!
For FreeBSD:
pkg install nano
For OpenBSD:
pkg_add nano
It will probably ask you to first install the package manager then it will prompt for the confirmation to install the desired package. But if there is no Internet because the network interfaces need configuration, follow the next steps first.
NETWORK CONFIGURATION
Most likely, two network interfaces will be required and for this demo I will consider the first interface as a WAN (has Internet access) and the second as a LAN (has only internal network access).
ifconfig
Three network interfaces might show up: em0 (WAN), em1 (LAN), and lo0 (loopback). If any was not properly configured during the installation of the system forllow the next steps.
For FreeBSD:
nano /etc/rc.conf
... # WAN (em0) ifconfig_em0="DHCP" # LAN (em1) ifconfig_em1="inet 10.0.0.10 netmask 255.255.255.0" ...
Optionally, if the DHCP does not provide a default a default gateway can be added to this same configuration file as follows:
... defaultrouter="10.1.1.1" ...
Out-of-the-box, FreeBSD and OpenBSD are native routers, capable of routing traffic between all configured interfaces but it requires a single flag to be turned on:
gateway_enable="YES"
Apply the configuration by restarting the network service.
service netif restart
Check the networks and routes.
netstat -r netstat -nr
Setting a static route:
route add -net 192.168.0.0/16 10.2.2.1
To make it persist reboots:
nano /etc/rc.conf
... static_routes="net2" route_net2="-net 192.168.0.0/16 10.2.2.1" ...
For more then one:
... static_routes="net2 net3" route_net2="-net 192.168.0.0/16 10.2.2.1" route_net3="-net 172.16.0.0/24 10.2.2.1" ...
If configured to use DHCP, it will automatically populate the file /etc/resolv.conf, and like on Linux it can always be manually managed and the auto population can be suppressed as follows:
/etc/dhclient-enter-hooks
...
add_new_resolv_conf() {
# Do not overwritte /etc/resolv.conf with the DHCP configuration.
return 0
}
...
For OpenBSD:
nano /etc/hostname.em0
For HDCP:
inet autoconf
For static IP:
inet 10.1.1.2 255.255.255.0 10.1.1.1
Apply
sh /etc/netstart
MANAGING USERS
Create a new used.
adduser userName
Delete a user:
rmuser userName
Changing current user’s password and another user’s password:
passwd
passwd userName
To make it an administrator add it to the wheel group.
For FreeBSD:
pw groupmod -n wheel -m userName
To remove, replace the argument -m with -d. Then, list the members of the wheel group.
pw groupshow -n wheel
For OpenBSD:
usermod -G wheel userName
List what groups the user is part of.
id userName
Since by default the root user is not allowed to SSH (like in most Linux systems), use the newly created user to connect from remote then switch to root with the command su.
Probably it will require to restart the the SSHd service to allow the new user to connect.
For FreeBSD:
service sshd restart service status restart
For OpenBSD:
rcctl restart sshd rcctl check sshd
FILE SYSTEM
Originally, UFS (Unix File System) was the default file system but now ZFS (Zettabyte File System) is the default one because it supports advanced features like snapshots, compression, RAID…
Besides UFS and ZFS, there is also another native file systems called HUMMER (Highly Available, Multi-Master, Elastic Replicated Object Store). It was developed by DragonFly BSD that can provide high availability and fault tolerance. It is worthy taking a look into it if these features are desirable for your use case.
It also supports FAT, NTFS, EXT2 to EXT4, APFS, and ISP 9660 plus the network NFS (Linux) and CIFS (Windows). Note that it does NOT officially suport XFS.
Linux users feel familiar with most of the Directory Structure and how to navigate and manager files, directories, permissions and so on.
FIREWALL ON FREEBSD
Enable the firewall.
nano /etc/rc.conf
... firewall_enable="YES" ...
Create the set of rules.
nano /etc/ipfw.rules
ipfw add allow tcp from any to any 80 in ipfw add allow ip from any to any 21 out ipfw add allow tcp from 10.20.30.0/24 to 10.1.1.1 22 in ipfw add deny udp from any to any 53 ipfw add deny all from 192.168.0.10 to any in ipfw add deny tcp from any to any 22 in via em0 ipfw add deny tcp from any to any 10000-2000 fwd em0
- in / out
- only applied to and from the local system.
- in via / out via
- applied the rule to the traffic on the interface, which also applied to the forwarded packets.
- fwd
- only applied the filter to the packets being forwarded to the specified interface.
Load the rules to the kernel.
/sbin/ipfw /etc/ipfw.rules
Make firewall rules persist to reboots, add the same line to the following file.
nano /etc/rc.local
... /sbin/ipfw /etc/ipfw.rules ...
FIREWALL ON OPENBSD
nano /etc/pf.conf
wan="em0"
lan="em1"
set skip on lo0
set block-policy drop
block drop all
block in all
block out all
pass quick in all keep state
pass in on $wan proto tcp from any to any port 80
pass in on $lan proto { tcp udp } from $lan:network to port { 139 445 }
pass out inet proto icpm icmp-type { echoreq }
pass in on $lan proto icmp all icmp-type { echoreq, echorep }
Optionally, replace keep state with modulate state for additional security because it randomises the initial sequence number pf TCP packet to prevent prevention and TCP session hijacking attack.
Apply
pfctl -f /etc/pf.conf
Enable the firewall on boot.
nano /etc/rc.conf.local
... pf=YES ...
Check the status of the firewall.
pfctl -si
Check the applied roles.
pfctl -sr
TROUBLESHOOTING
- System Logs
Watch the logs as they happens.
tail -f /var/log/messages
Search for a specific entry type.
tail -f /var/log/messages | grep error
grep ssh /var/log/messages
- Diagnostic Tools
ping 8.8.8.8
traceroute 1.1.1.1
top
tcpdump -i em0
dmesg | less