Proxmox officially does not run on Raspberry Pi but Pimox does [Link].
Pimox is an adapted build of Proxmox that was tailored to work on the Raspberry Pi 4 (ARM64 architecture).
REQUIREMENTS
- Raspberry Pi 4
- 2 GB of RAM works but limited,
- 4 GB of RAM works well,
- 8 GB of RAM is the recommended.
- 1.5 GB needs to be reserved to the host system.
- Storage
- Min of 16 GB microSD / USB,
- Recommended >32 GB of fast SSD / NVMe / M.2 over USB.
- Accessories
- Power supply,
- A closed case,
- Heatsink (passive cooling),
- 5V fan (active cooling) like a Fanshim [Link].
If necessary, update the RPi’s firmware to prioritize USB boot over microSD.
Write the latest Raspberry Pi OS Lite image to the storage media of choice, and fire it up.
PROCEDURES
Do NOT proceed with the installation via SSH because it will drop the connection, interrupting the installation.
Using the console (physical keyboard, mouse, and a monitor), run the following commands as root, do NOT use sudo.
sudo su - curl https://raw.githubusercontent.com/pimox/pimox7/master/RPiOS64-IA-Install.sh > RPiOS64-IA-Install.sh chmod +x RPiOS64-IA-Install.sh ./RPiOS64-IA-Install.sh
Note: it will ask for an static IP because it does NOT work with DHCP. Just follow the prompts.
It will show the address of the Proxmox web interface at the end.
Increasing the default swap of the Host:
nano /etc/dphys-swapfile
... CONF_SWAPSIZE=2048 ...
systemctl enable dphys-swapfile
It is recommended to install GPU driver and libraries for accessing the RPi’s hardware features.
sudo apt update && sudo apt install mesa-utils libraspberrypi-bin -y vcgencmd measure_temp ; vcgencmd get_mem gpu sudo reboot
GUEST SYSTEMS
LXC (Linux Containers) are recommended over VMs to maximize performance and resource utilization. Read more at [Link].
Make sure the LXC repository you will download from is trustworthy. Only the file rootfs.tar.xz is required [Link].
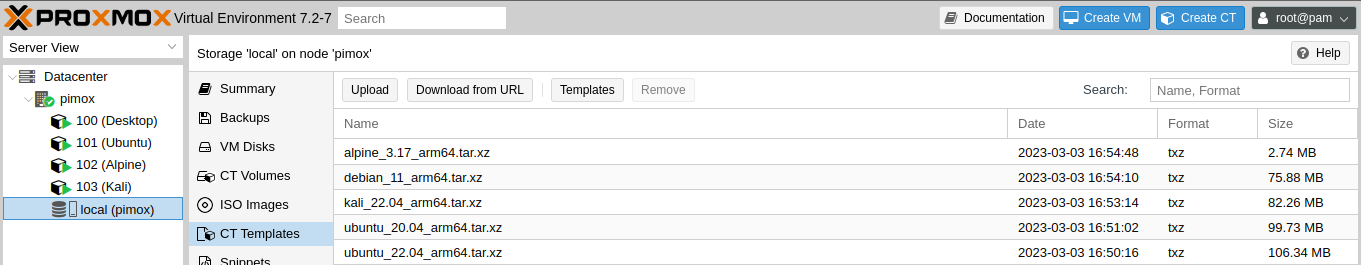
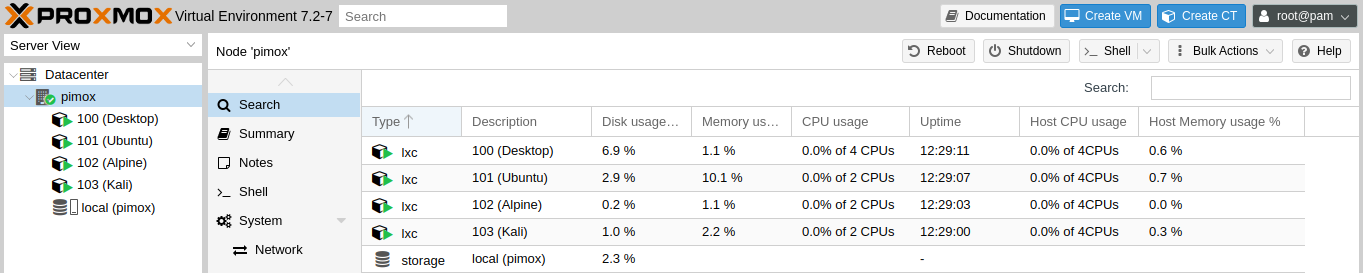
Note: VMs (Virtual Machines) do not work on this platform. CTs are much better anyway.
ONLINE REPOSITORY OF LXC TEMPLATES
Unfortunately, Pimox does not implement a custom repository for ARM64 templates. Probably because it requires hosting infrastructure and periodical maintenance of the inventory of images.
I have developed and maintained a single source for an updated list of ARM64 images on GitHub called Pimox7 LXC Images [Link].
Installation of the Templates Repository
wget https://raw.githubusercontent.com/davift/pimox7-lxc-images/main/install.sh -O install.sh && chmod +x install.sh && sudo ./install.sh
It will download the latest version of the installation script, and prompt for confirmation before each of the tasks:
- Replace/Update the LXC list of templates (y/N)?
- If confirmed, it will backup the original files (incompatible) and then download the repository list with ARM64 images.
- Download the templates from linuxcontainers.org (y/N)?
- Alternatively, all images can be downloaded from linuxcontainers.org at once. It might require ~1.2 GB.
- Download custom templates (y/N)?
- Lastly, it will ask to download all custom images I produced and shared.
What are the custom images about?
- Kali CLI
- All the look and feel of the Kali command prompt plus all the basic tools.
- Kali Desktop with XRDP
- After creating and stating a CT with this image, use any RDP client to connect to a fully-fledged Virtual Desktop experience.
- Tor Gateway
- This appliance works as a gateway to route (tunnel) all traffic through the Tor Network.
- The first network adapter
eth0onvmbr0(Internet) with DHCP - Create a secondary adapter
eth1on thevmbr2(isolated network) with the IP10.10.10.1. - All inbound traffic on
eth1will be served via Tor. 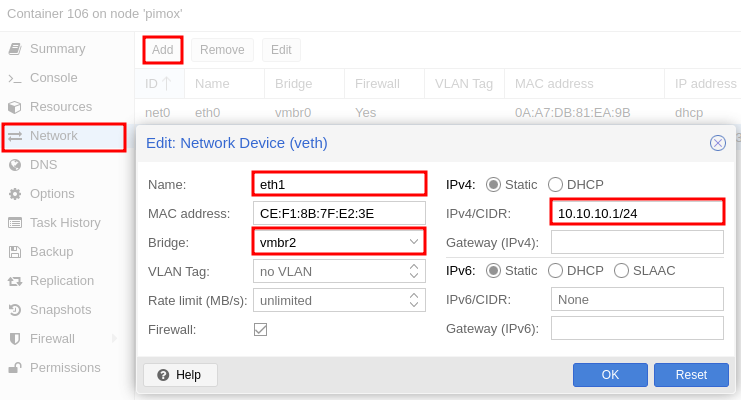
- The first network adapter
- Any other CT that is connected to vmbr2 needs the following network configuration.
- IPv4
10.10.10.2/24to10.10.10.254/24 - Gateway
10.10.10.1. 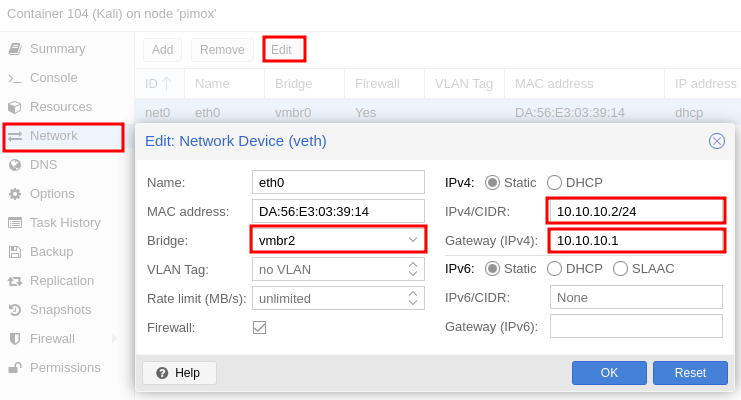
- IPv4
- This appliance works as a gateway to route (tunnel) all traffic through the Tor Network.
INTERNAL NETWORKS
Out-of-the-box Proxmox creates a Bridge network vmbr0 linked to the physical port eth0 and the wireless adapter wlan0 becomes unusable (coming soon a work around for it).
Additional private networks might be required to
vmbr0- Any CT or VM will have its own MAC address to the network interface and will get an IP from the network attached to the Ethernet port.
vmbr1- It is always great to have a private network that applies NAT to provide internet access but recycle the IP address of the Host. See steps ahead.
vmbr2- An isolated network that does not allow internet access can be useful for sandboxing applications or to perform local workloads.
vmbr3- (in progress – a network linked to the wireless interface)
NAT NETWORK WITH DHCP vmbr1
On the Pimox host, navigate to System > Network > click on Create > Linux Bridge.
Enter 172.16.0.1/24 in IPv4/CIDR. No other field is required.
This will create a private network capable of communicating with the Host server but no traffic will be routed out.
Setting up the DHCP server via SSH or Shell to the Host.
sudo apt-get update && sudo apt-get install isc-dhcp-server -y sudo nano /etc/default/isc-dhcp-server
Limit the DHCP server to only bind on vmbr1 only for IPv4 (disabling IPv6).
INTERFACESv4="vmbr1" #INTERFACESv6=""
Specify the DHCP parameters.
sudo nano /etc/dhcp/dhcpd.conf
Append the following to the file content.
default-lease-time 600;
max-lease-time 7200;
option subnet-mask 255.255.255.0;
option broadcast-address 172.16.0.255;
option routers 172.16.0.1;
option domain-name-servers 9.9.9.9;
option domain-name "host.local";
subnet 172.16.0.0 netmask 255.255.255.0 {
range 172.16.0.10 172.16.0.100;
}
Apply the changes.
sudo systemctl restart isc-dhcp-server sudo systemctl enable isc-dhcp-server sudo systemctl status isc-dhcp-server
At this point, any net CT or VM attached to this network will be able to receive an IP automatically.
Setting up the Forwarding / Routing via SSH or Shell to the Host.
sudo ufw enable sudo nano /etc/ufw/sysctl.conf
Uncomment this configuration or add if you do not find it:
net/ipv4/ip_forward=1
Do the same for /etc/sysctl.conf.
Edit/create the startup script:
sudo nano /etc/rc.local
Add the following content.
#!/bin/bash WAN="vmbr0" LAN="vmbr1" iptables -A INPUT -i lo -j ACCEPT iptables -A OUTPUT -o lo -j ACCEPT # Port forwarwind rules must be placed here iptables -A FORWARD -i $LAN -o $WAN -j ACCEPT iptables -A FORWARD -i $WAN -o $LAN -m state --state RELATED,ESTABLISHED -j ACCEPT iptables -t nat -A POSTROUTING -o $WAN -j MASQUERADE exit 0
Apply the changes.
sudo chmod +x /etc/rc.local sudo /etc/rc.local
Traffic might be able to reach the Internet from the guests in vmbr1 now.
Optionally, a DNS server can be installed on the Host [Link] or deploy a Pi-Hole in a CT [Link].
DEPLOYING USEFUL CT SYSTEMS
Kali Remote Terminal
sudo apt update && apt dist-upgrade -y sudo apt install ssh wget curl nano man bind9-dnsutils inetutils-tools iputils-* kali-defaults zsh zsh-syntax-highlighting zsh-autosuggestions kali-linux-arm -y sudo apt purge network-manager -y sudo systemctl start ssh && systemctl enable ssh sudo adduser kali sudo usermod -aG sudo kali
Kali Remote Desktop
Install all the same packets from the Kali Remote Terminal before proceeding.
sudo apt install kali-desktop-xfce xorg xrdp -y sudo systemctl enable xrdp sudo reboot
The routing rules from the Host could be changed as follows to forward the RDP port to the Remote Desktop.
#!/bin/bash WAN="vmbr0" LAN="vmbr1" iptables -A INPUT -i lo -j ACCEPT iptables -A OUTPUT -o lo -j ACCEPT iptables -A FORWARD -i $WAN -o $LAN -p tcp --dport 3389 -m state --state NEW,RELATED,ESTABLISHED -j ACCEPT iptables -t nat -A PREROUTING -i $WAN -p tcp --dport 3389 -j DNAT --to-destination 172.16.0.13:3389 iptables -A FORWARD -i $LAN -o $WAN -j ACCEPT iptables -A FORWARD -i $WAN -o $LAN -m state --state RELATED,ESTABLISHED -j ACCEPT iptables -t nat -A POSTROUTING -o $WAN -j MASQUERADE exit 0
Tor Proxy Gateway
A Tor Proxy Gateway is a server that offers SOCKS5 Proxy through Tor Network for maximum privacy.
It can be located between vmbr0 or vmbr1, that have Internet access, and an isolated network, suck as vmbr2.
apt update && apt upgrade -y && apt install tor nano curl -y nano /etc/tor/torrc
... SocksPort 0.0.0.0:9050 ...
systemctl restart tor && systemctl enable tor curl --socks5-hostname 127.0.0.1:9050 http://ip.me
Compare the output IP with your real public IP. The applications on guest systems in the isolated network vmbr2 shall use SOCKS5 Proxy from the Tor Gateway server.
CloudFlare Bridge
Navigate to CloudFlare > Zero Trust > Access > Tunnels
apt update && sudo apt upgrade -y && sudo apt install curl -y curl -L --output cloudflared.deb https://github.com/cloudflare/cloudflared/releases/latest/download/cloudflared-linux-arm64.deb dpkg -i cloudflared.deb cloudflared service install **********
Replace ********** with the connector string.
Installing a GUI on Ubuntu 22.04
Prepare the system.
apt update && apt upgrade -y
Choose one of the option below:
For Xfce (lighwight)
apt install xfce4 xrdp -y
For Gnome
apt install ubuntu-desktop-minimal xrdp -y
For KDE (heaviest)
apt install kde-plasma-desktop xrdp -y
Complete by enabling RDP by on startup.
systemctl enable xrdp && reboot
CREATING CUSTOM LXC TEMPLATES
Deploy a new CT using the base images of your choice and customize it.
When ready to transform the CT instance into a shareable template, back it up and select the compression format GZIP.
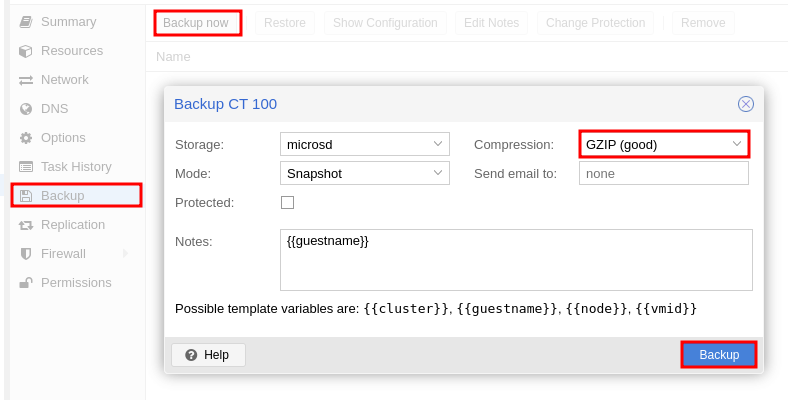
It will produce a backup file /<PATH>/dump/vzdump-lxc-<CT_ID>-<TIMESTAMP>.tar.gz.
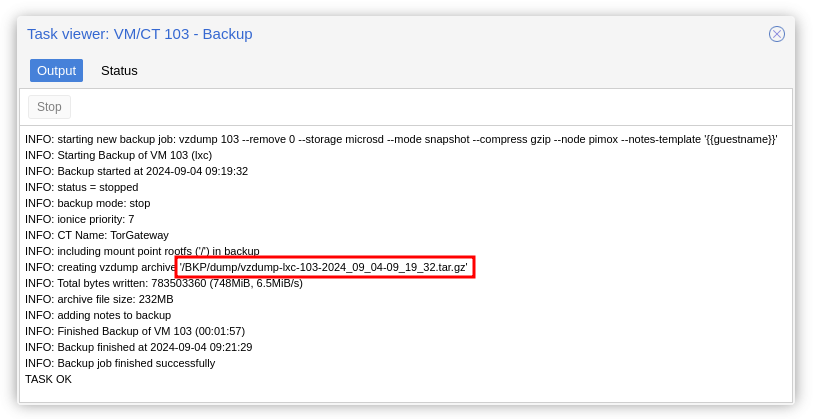
Transfer the file over via SCP, that is all!