Kali Linux is a Debian-based Linux distribution originally designed for offensive information security. It contains tons of tools for penetration testing, network security, bug hunting, cyber security research, digital forensics, and reverse engineering.
At the 10th anniversary, Kali released Kali Purple 2023.1 variation of its original build. It contains additional tools focused on defensive information security plus a new defensive menu structure:
| Identify | Protect | Detect | Respond | Recover |
|---|---|---|---|---|
 |
 |
 |
 |
 |
Note: most of these tools were already part of Kali, they are just arganised in a way that makes sense to a blue/purple team instead of a purely red team approach.
FEATURED DEFENSIVE TOOLS
- Arkime
- CyberChef
- Elastic Security
- Security information and event management tool that combines capabilities of SIEM, EDR, and cloud security [Link].
- Greenbone Vulnerability Manager
- TheHive
- Malcolm – Network traffic analysis tool suite
- Suricata
- A mobile IDS appliance. As it is offered in the Kali Purple build it is NOT mean to be used and a router but to used in campaigns [Link].
- Zeek
- Kali Autopilot
- An attack script builder framework for automated attacks able to share scripts for blue teams to go up against, as well as practice packet captures to train in network analysis [Link].
CHEAT SHEET
Identify
amass- OWASP Amass Project is a great open source tool written in Go for network mapping, attack surface and asset discovery that combine active and passive techniques [Link].
amass intelfor intelligence gathering.-activeenables active methods.-d,-addr,-asn, and-cidrinform list or range of targets in the scope.-dfand-deprovide a file list with the domains to add and exclude to the scope.-whoisand-orgsearch in directories for reverse whois and organisation names (respectively).-
amass intel -list amass intel -whois -d domain.com amass intel -org CompanyName
amass enumfor enumeration.-activeand-passiveenables active methods or defines and purely passive.-df,-ef,-dfand-blfinforms files as source for domains to include, exclude, root names, and blacklisted (respectively).-dns-qps,-max-dns-queries, and-min-for-recursiveset limits-ifaceespecifies the interface to send the traffic from (a VPN is recommended. E.g.tun0).-
amass enum -list amass enum -min-for-recursive 5 -ip -brute -v -src -d domain.com
amass vizcreates a visualisation graph to add structure to the acquired information.-oand-oAuses already existing output file as source and sets the prefix for the output file name (respectively).-graphistry,-maltego, and-dotdefines the type of graph output file.-
amass viz -graphistry -d domain.com amass viz -maltego -d domain.com
amass trackanalyses a target over time, between logged enumerations.-
amass track -d domain.com
-
amass dbperforms viewing of the acquired data in the database or output directory.-
amass db -d domain.com
-
- In all cases other flags can be used for help (
-h), additional verbosity (-v) or quiet standard output (-silent). Check documentation for more [Link].
assetfinder- Helps to find related domains and sub-domains to the domains in the scope passively [Link].
-
sudo apt install assetfinder -y assetfinder -h assetfinder domain.com
cisco-auditing-tool- Used to scan Cisco devices/appliances for common vulnerabilities.
-hand-ffor a single or a list of hosts.-pinforms the port number.-wand-auses word and password lists.-
sudo apt install cisco-auditing-tool -y CAT --help CAT 192.168.1.1
- Used to scan Cisco devices/appliances for common vulnerabilities.
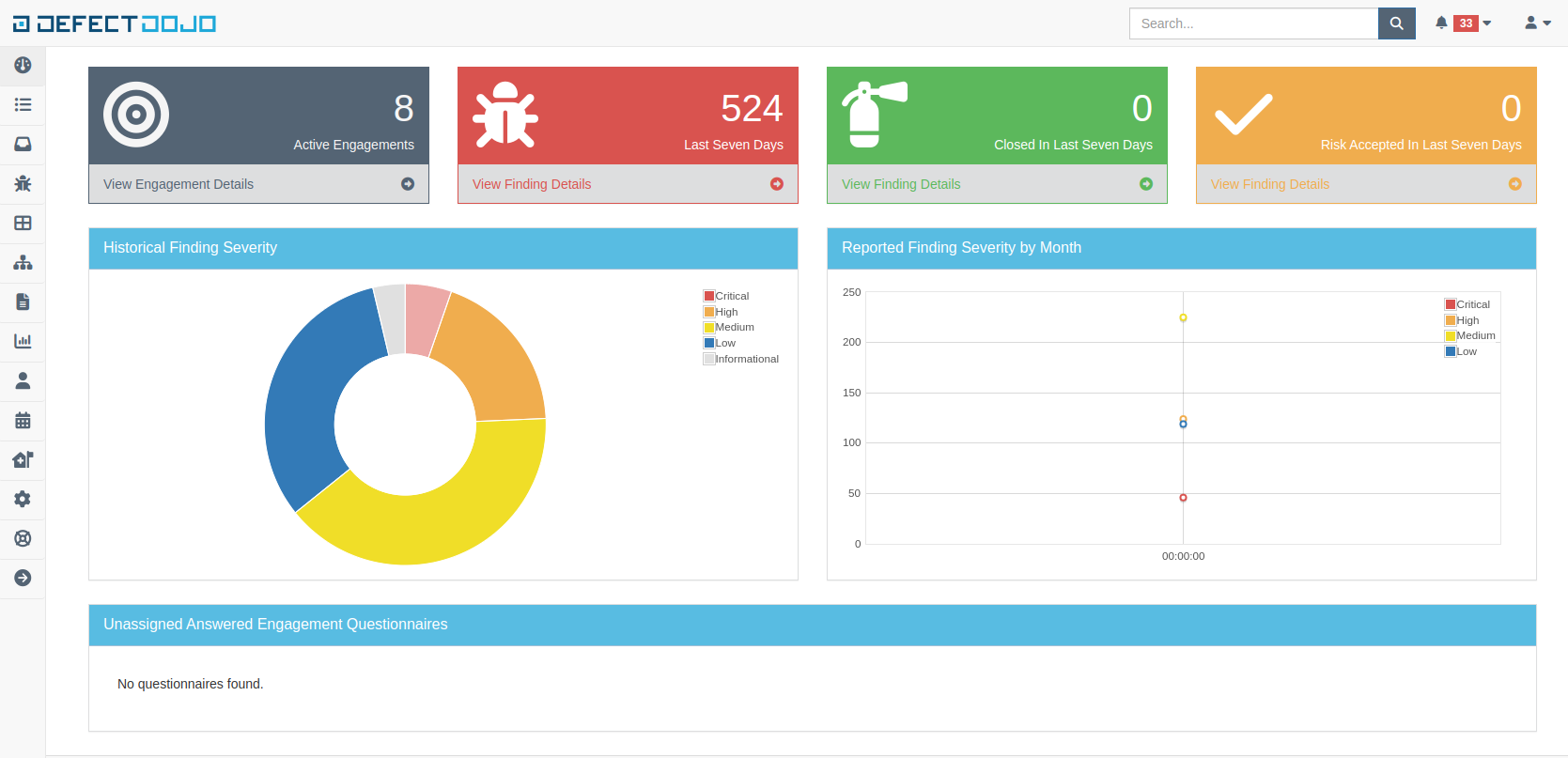
defectdojo- It is a vulnerability management platform for DevSecOps teams [Link]. From triage information to integrations with Jira and Slack.
-
sudo apt install defectdojo -y defectdojo start defectdojo stop
- Navigate to http://127.0.0.1:42003 and use the following command to create andmin user for your self:
-
cd /usr/lib/defectdojo && sudo -u _defectdojo -- python3 manage.py createsuperuser
hb-honeypotmaltego- Maltego helps to graphically illustrate and analyses output files from intelligence and forensics tools [Link]. It makes easy to identify patterns that otherwise easily pass unoticed.
-
sudo apt install maltego -y
maryam- OWASP Maryam is a framework based on OSINT for data acquisition and compilation [Link].
-
sudo apt install maryam -y maryam -e show modules maryam -e crt -q "domain.com" maryam -e github -q "userName"
nipper- A tool for audit configuration of Cisco routers, firewalls, switches, and other network devices looking for security issues [Link]. I believe it has not being maintained.
-
sudo apt install nipper-ng -y nipper --ios-switch --input=/PATH/switch.config --xml --output=audit.xml
osrframework- It is a set of libraries that performs OSINT collection tasks [Link].
usufyidentifies the social media websites that contain the informed username.mailfysearch for a given email or username.phonepylook for the existence of a phone number in popular directoriesdomainfylooks for domains that satisfy the query and resolve to an IP.searchfylooks for a string or name through all sources.checkfyfinds potential email addresses based on known aliases and patterns.-
sudo apt install osrframework -y usufy -n userName mailfy -n userName phonefy -n phoneNumber domainfy -n domainPrefix searchfy -q 'Full Name'
searchsploit- A CLI command to fetch results from Exploit Database [Link]. It essentially, search for exploits based on a query strings or filters from a local copy of the DB.
- This database is maintained but the Kali team, but there are other very relevant databases that must be considered during a thorough campaign (does not mean all of them are trustworthy):
-
sudo apt install exploitdb -y searchsploit sftp windows searchsploit sftp windows --json searchsploit -p 40828 searchsploit sftp --exclude="(PoC)|/dos/" searchsploit --cve 2021-44228
tiger- It is a big set of tools to perform internal security audit on UNIX/UNIX-based system and intrusion detection [Link].
sudo tigerto perform a full audit.-lspecify the output directory.-Ggenerates MD5 signature to the binary files to further identify tampering.-eand-Ewill provide explanations to the findings.-qlimits the outputs to the security issues.-
sudo apt install tiger -y sudo tiger tiger -l /PATH/ tiger -G
- In Kali’s documentation they mention the alternative
checksecurity,lsatoryasat.
wapiti- An web-app dynamic tester [Link]. It fuzzes and tries to inject a series of well-known exploits for SQL, XSS, Shell, XXE, CRLF, CSRF, and more.
-
sudo apt install wapiti -y wapiti -u http://domain.com/app
withnessme- Not sure what this tool does because I can’t find it in Kali tools page and it does not has a
manfile either. - Looks like it takes screenshots of a remote host (maybe via VNC).
- Not sure what this tool does because I can’t find it in Kali tools page and it does not has a
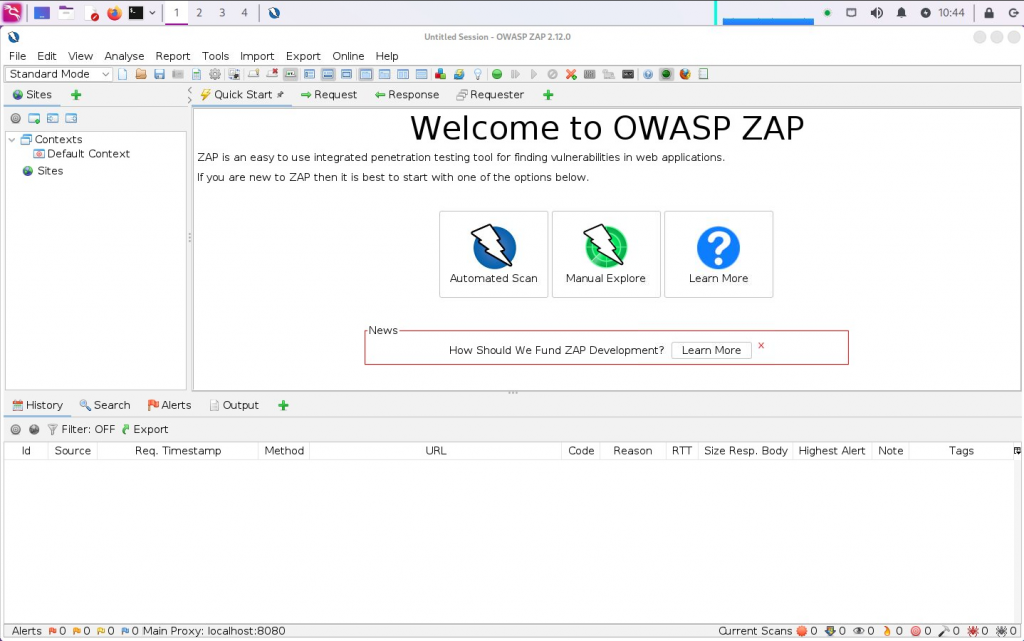
zap- OWASP Zap is a proxy tool similar to Burp Suite used for web-app pentesting [Link].
- This open source tool is not my favourite but deserves my respect because it gets the job done with no feature throttling (like Burt Community Edition does for non-paying users).
Protect
clamav- Who said there is no virus for Linux? ClamAV is probably the most versatile and widely used antivirus [Link].
- This open source signature-based AV engine is the default in many other open source projects to perform email, traffic, and file scans.
-
sudo apt install clamav clamav-daemon -y sudo clamscan --infected --remove --recursive /PATH
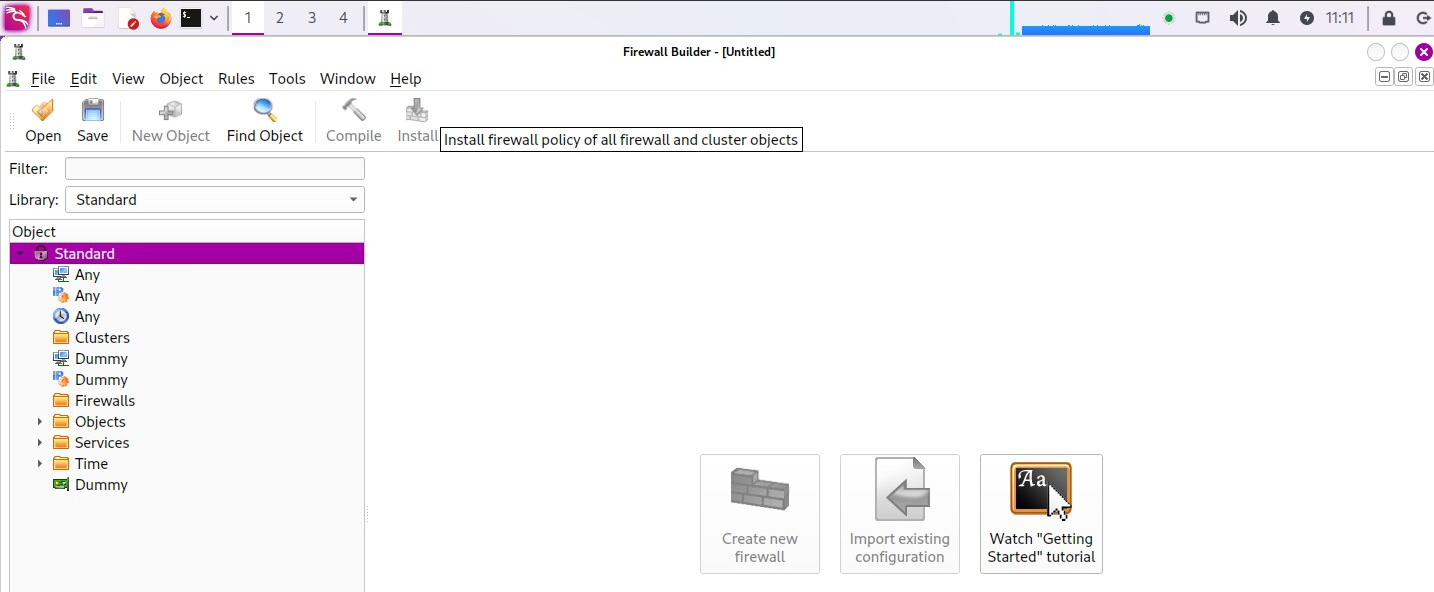
cryptsetup- fwbuilder
- Firewall Builder is a GUI for building, editing, and auditing firewall policies from various vendors/platforms [Link].
- It display rules and policies as objects in a file system directory.
-
sudo apt install fwbuilder -y
Detect
grokevt- GrokEVT used multiple scripts to parse old Microsoft Windows event logs [Link]. It appears to not be maintained anymore.
-
sudo apt install grokevt -y grokevt-parselog -l /var/db/grokevt/mysystem grokevt-parselog /var/db/grokevt/mysystem System grokevt-findlogs dumpDisk.img
sentrypeer- It is a project that does not rely on centralised infrastructure to protect IP SIP (VoIP) servers [Link].
- Using a p2p method it shares IP and phone numbers they tried to call between servers to detect fraud and sent notifications.
-
sudo apt install sentrypeer -y sentrypeer -w -j -f /PATH/sentrypeer.db -l /PATH/json.log
Respond
dc3dd- It is forensics tool for that is similar to
ddbut with additional features, such as auto skip bad sectors on the disk, create a hash over the same data streamof the copy, compression, and ecryption [Link]. -
sudo apt install dc3dd -y dc3dd -i dc3dd if=/dev/sda of=image.dd hash=sha512
- It is forensics tool for that is similar to
ewf-tools- It is a forensics set of tools and libraries with support for EWF (Expert Witness Format) image files [Link].
ewfacquirewrites device storage to EWF files.ewfacquirestreamwrites data from standard input to EWF files.ewfexportexports storage media data in EWF files to RAW or a specific version of EWF.ewfinfoshows EWF metadata.ewfmountmounts EWF files.ewfrecovercreates a new set of EWF files from a corrupt set.ewfverifyverifies EWF integrity and authenticity.-
sudo apt install ewf-tools -y ewfinfo image.E01 ewfverify image.E01 ewfmount image.E01 /PATH ewfrecover image.E01 /PATH sudo ewfacquire /dev/sda image.E01 sudo ewfacquirestream /dev/sda - | ssh [email protected] "cat > /PATH/image.E01" ewfacquirestream image.raw | ssh [email protected] remote.example.com "cat > /PATH/image.E01" ewfexport image.E01 -f raw -t image.dd
- It is a forensics set of tools and libraries with support for EWF (Expert Witness Format) image files [Link].
foremost- File recovery tool that can read from image files or directly from a storage device [Link].
-
sudo apt install foremost -y foremost -t jpg,png -i /dev/sdb1 -o /PATH/RECOVERED/ foremost -c custom.conf -i image.dd -o /PATH/RECOVERED/ foremost -t pdf -i /dev/sdc1 -o /PATH/RECOVERED/ -s /usr/share/foremost/pdf.confidential
galleta- A tool to extract cookies from the defunct Microsoft Internet Explorer.
-
sudo apt install galleta -y galleta -d";" output.txt galleta example.cookie > output.txt
ghidra- Ghidra is an open-source GUI tool for software reverse engineering developed by NSA [Link]. It allows one to disassemble, decompile, and debug, among other features used to analyse binary files and software (including malware, firmware, and compiled programs).
guymager- A graphic forensic imager tool for media acquisition that support different image file formats (
dd,ewf, andaffplus disk cloning) and multi-threaded engine for parallel, providing great performance during compression [Link]. 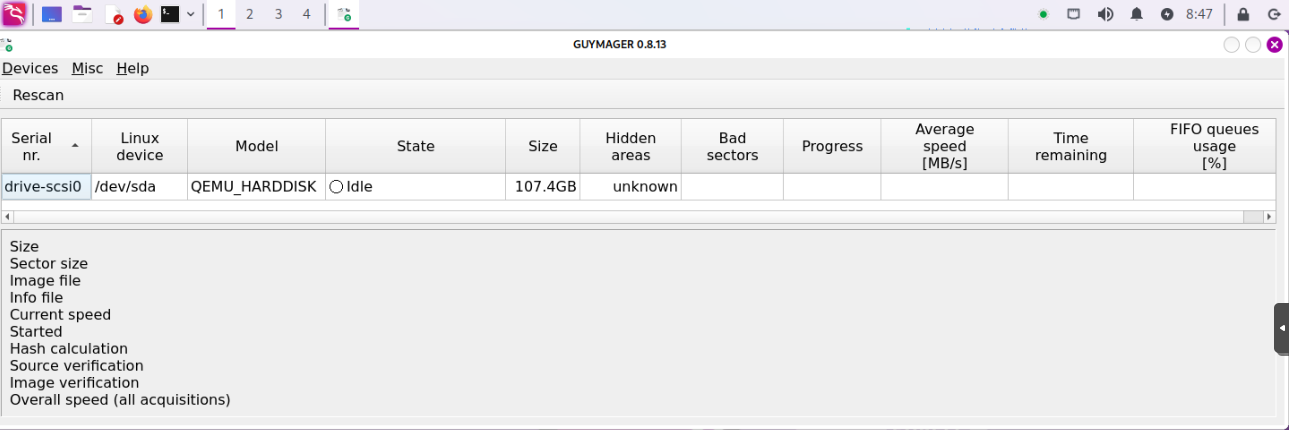
- A graphic forensic imager tool for media acquisition that support different image file formats (
hashrat- Hashrat is program to generate md5, sha1, sha256, sha512, whirlpool, jh-244, jh256, jh-384, jh-512, and other hash functions for Password Generation, File Integrity and Duplicated [Link].
-
sudo apt install hashrat -y cat fileName | hashrat -md5
- Note: the example command above is equivalent to
md5sum fileNamebut Hashrat can do much more than that
sleuthkit- TSK (The Sleuth Kit) is a digital forensics library and collection of command line tools that allows one to analyse volumes and file systems [Link].
-
sudo apt install libtsk-dev libtsk19 sleuthkit -y
blkcalcblkcatblklsblkstatfcatffindfiwalkflsfsstathfindicatifindilsimg_catimg_statistatjcatjlsjpeg_extractmactimemmcatmmlsmmstatpstatsigfindsortersrch_stringstsk_comparedirtsk_gettimestsk_imageinfotsk_loaddbtsk_recoverusnjls
mac-robber- It is a sibling project of TSK and Autopsy. Mac-Robber is a digital investigation and incident response tool that collects data (meta-data) from allocated files and directories in a mounted file system [Link].
-
sudo apt install mac-robber -y mac-robber /PATH/ mac-robber /PATH/ | mactime -z EST
impacket-scripts- Impacket is a Python library with tools for interacting with network services, such as SMB, MSSQL, LDAP, and others. It is commonly used as password cracking, network sniffing, packet manipulation, password spraying and privilege escalation by cyber security researches [Link]. Impacket-Scripts can be used on offensive (pentesting) and defensive (network monitoring, detection, and incident response).
-
sudo apt install impacket-scripts -y
-
impacket-addcomputerimpacket-atexecimpacket-dcomexecimpacket-dpapiimpacket-esentutlimpacket-exchangerimpacket-findDelegationimpacket-GetADUsersimpacket-getArchimpacket-Get-GPPPasswordimpacket-GetNPUsersimpacket-getPacimpacket-getSTimpacket-getTGTimpacket-GetUserSPNsimpacket-goldenPacimpacket-karmaSMBimpacket-keylistattackimpacket-kinterceptimpacket-lookupsidimpacket-machine_roleimpacket-mimikatzimpacket-mqtt_checkimpacket-mssqlclientimpacket-mssqlinstanceimpacket-netviewimpacket-nmapAnswerMachineimpacket-ntfs-readimpacket-ntlmrelayximpacket-pingimpacket-ping6impacket-psexecimpacket-raiseChildimpacket-rbcdimpacket-rdp_checkimpacket-regimpacket-registry-readimpacket-rpcdumpimpacket-rpcmapimpacket-sambaPipeimpacket-samrdumpimpacket-secretsdumpimpacket-servicesimpacket-smbclientimpacket-smbexecimpacket-smbpasswdimpacket-smbrelayximpacket-smbserverimpacket-sniffimpacket-snifferimpacket-splitimpacket-ticketConverterimpacket-ticketerimpacket-wmiexecimpacket-wmipersistimpacket-wmiquery- This list of script diserver
-
netsniff-ng- Netsniff-ng is a free Linux networking toolkit can be used for network development and analysis, debugging, auditing or network reconnaissance [Link]. Source code available at [Link].
-
sudo apt install netsniff-ng
netsniff-nga zero-copy analyzer, pcap capturing/replay tool compatible withtcpdumpandwireshark.trafgena multi-threaded low-level zero-copy network packet generator (including raw 802.11 frames).mausezahna high-level packet generator for network appliances with Cisco-CLI. Good for stress, malformed, or malicious packets testsbpfca BPF (Berkeley Packet Filter) compiler and disassembler. It supports undocumented Linux filter extensions, that high-level filters fail to support.ifppsa top-like kernel networking statistics tool.-dor--devto specify the device.-nor--num-cpusd specifies the number of CPUs/cores to display in ncurses mode, default is 10.-tor--intervalis the desired refresh interval, default is 1000ms.-cor--csvto output to a CSV (more human friendly than raw) format.-oor--omit-headerto be used with-cit asks to not write the headers in the file.-lor--loopwill continuously output to the terminal data after a refresh interval. Requires-c.-mor--medianis the flag that shows the median values across all CPUs/cores for a load calculation and interrupts.-por--promiscturns on the promiscous mode on the NIC. In virtualized envinronments it might also require tweaks on the hypervisor.-Por--percentagewill show relative values to the line rate.-Wor--no-warnsuppresses warnings.-
ifpps eth0 sudo ifpps -pd eth0 sudo ifpps -lpcd eth0 > eth0raw.data sudo ifpps -lpcd wlan0 > wlan0raw.data
flowtopa top-like netfilter connection tracking tool.-4or--ipv4for only IPv4.-6or--ipv6for only IPV6.-Tor--tcpfor only TCP (Transmission Control Protocol) traffic.-Uor--udpfor only UDP (User Datagram Protocol) traffic.-Ior--icmpfor only ICMP (Internet Control Message Protocol) traffic.-Dor--dccpfor only DCCP (Datagram Congestion Control Protocol) traffic.-Sor--sctpfor only SCTP (Stream Control Transmission Protocol) traffic.-nor--no-dnsdo not DNS replace IPs with reverse lookup names.-sor--show-srcshow source IP.-bor--bitsshow speed in bits/s instead of bytes/s.-Gor--no-geoipdo not use the GeoIP database (buggy).-uor--updateupdates the GeoIP local database.-tor--intervaldefines the refresh interval in seconds, default is 1.- They can and should all be used in combination with each other.
-
sudo flowtop -4UTIGs
- For the GeoIP database:
-
sudo mkdir /usr/share/netsniff-ng sudo flowtop --update
- You might find issues with the file `GeoIP.dat.gz` that is missing and cannot be retrived from the mirrors because they are not available anymore. One alternative is to manually download and place on the specified directory. Or do not use GeoIP (
-G).
-
curvetuna lightweight Curve25519-based IP tunnel that uses TUN/TAP to transfer IPv4/IPv6 TCP/UDP traffic over IPv4/IPv6.astraceroutean autonomous system (AS) trace route utility. Compared totracerouteandtcptracerouteit provides additional information that is about the AS and GeoIP.
ollydbg- OllyDbg is a 32-bit assembler level analysing debugger (decompiler) for Microsoft Windows binaries [Link]. It requires
wineto run on Linux and is a great tool for malware analysis (the source code is not available). It is not open source. -
sudo dpkg --add-architecture i386 && sudo apt update && sudo apt -y install wine32 ollydbg
- It might fail because the library
kernel32.dllcould not be loaded bywine. Work on it!
- It might fail because the library
- OllyDbg is a 32-bit assembler level analysing debugger (decompiler) for Microsoft Windows binaries [Link]. It requires
rkhunter- Rootkit Hunter is a open source Unix-based tool that scans for rootkits, backdoors and exploits in the local system [Link].
- It compares hashes of important local files with known good ones in online databases.
- Then, searching for rootkits, wrong permission and hidden files, suspicious strings in kernel modules, and does special tests for Linux and FreeBSD.
-
sudo apt install rkhunter -y sudo rkhunter --update sudo rkhunter --propupd sudo rkhunter -c --enable all --disable none --rwo sudo rkhunter --check sudo tail -f /var/log/rkhunter.log
- Note: there is no much value to run it on the Kali unless it had mounted a secondary drive cloned from a production server and with the usage of
chrootscan that system instead. Or periodically run in real production environments with email notifications enabled as a cronjob (E.g.0 3 * * * root /usr/bin/rkhunter --cronjob --update --quiet).
- Note: there is no much value to run it on the Kali unless it had mounted a secondary drive cloned from a production server and with the usage of
unhide- Unhide is a forensic tool that looks for hidden processes and open ports by rootkits or LKMs (loadable kernel modules), and other hidden techniques [Link].
-
sudo apt install unhide -y
unhidereveals any processes that are hidden from the process list.brutean aggressive method that checks areas that are not checked by default.procchecks an specific process ID.procalluses all available methods includingbrute.procfsrelys on/procto obtain the process list.quicka superficial and less intrusive check.reverseperform the checks in reverse order, starting frombrute.sysrelys onsyscallto obtain the process list.-
sudo unhide proc sudo unhide procall sudo unhide -v brute
unhide-linuxlooks for processes that are hidden using Linux kernel modules.-
sudo unhide-linux reverse
-
unhide-posixchecks for hidden TCP/UDP ports on your system (backdoors).-
sudo unhide-posix sys sudo unhide-posix proc
-
unhide-tcpchecks for hidden TCP/UDP ports on your system (backdoors).-
sudo unhide-tcp -v
-
unhide_rbcheck for hidden processes using C functions that are commonly used in rootkits written in Ruby.-
sudo unhide_rb
-
- Note:
unhide-guidoes not come installed on Kali but does not seems to work anyway.
wireshark- Wireshark is a network protocol analyzer. It captures (sniffs) traffic in real-time, commonly used for troubleshoot, monitoring activity, and identify security vulnerabilities [Link].
xplico- Xplico is a network forensics tool that extract content from a PCAP file [Link]. For example, it can reconstruct a web-page, tranferred files, VoIP calls, etc. It also offer a web interface on http://127.0.0.1:9876 (default credentials admin:xplico).
-
sudo xplico-webui
-
- On the command-line it can be used as follows:
-
xplico -m pcap -f file.pcap sudo xplico -m rltm -i eth0
-
- Xplico is a network forensics tool that extract content from a PCAP file [Link]. For example, it can reconstruct a web-page, tranferred files, VoIP calls, etc. It also offer a web interface on http://127.0.0.1:9876 (default credentials admin:xplico).
yara- YARA Rules are used to identify patterns of specific string in malware binaries to help classifying them (signature based identification) [Link].
-
sudo apt install yara libyara9 libyara-dev -y
Recover
ddrescue- It is a popular tools for recovery corrupted data from drives with damaged sectors and blocks [Link]. Other tools that might help to recovery data when are SpinRite (not open-source but the most powerful and reputable in existence) [Link], MyRescue, Testdisk, Photorec, Foremost, or Scalpel.
-
sudo ddrescue -f --no-split /dev/sdb1 /dev/sdc1 output.log
ext3grep- It can be used as a forensics tool to recover deleted files [Link]. Note that it is not currently under maintenance because ext3 is consider obsolete.
-
sudo apt install ext3grep -y ext3grep --dump-names /dev/sdb1 | grep 'fileName' ext3grep --ls --group 1000 /dev/sdb1 ext3grep --restore-all /dev/sdb1
ext4magic- ext4magic wes inpired on extgrep and extundelete and it is capable of restoring deleted files from ext3/ext4 directly from the file system journal [Link].
-
sudo apt install ext4magic -y sudo ext4magic /dev/sdb1 -M -d /PATH/Recovered/
extundelete- ExtUndelete tries to recover deleted files based of clues found in the partition’s journal [Link].
-
sudo apt install extundelete -y sudo extundelete /dev/sdb1 --restore-all
myrescue- MyRescue is an alternative to ddrescue. It does a best effort to try to recover data for defective drives [Link].
-
sudo apt install myrescue -y
recoverdm- RecoveryDM recovers data from bad sectors by attempting to read the in raw mode while ignoring errors. Unfortunately it is a defunct application that was discontinued and no official web-site is available.
-
sudo apt install recoverdm -y
recoverjpeg- RecoverJPEG tries to recover deleted JPEG and MOV (using recovermov) from a partition [Link].
-
sudo apt install recoverjpeg -y
scrounge-ntfs- Scrounge NTFS is a data recovery tool that reads each block of the disk and tries to rebuild the original file system structure into an output directory [Link].
-
sudo apt install scrounge-ntfs -y sudo scrounge-ntfs -l /dev/sdb scrounge-ntfs -m <MFT_OFFSET> -c <CLUSTER_SIZE> <START_SECTOR> <END_SECTOR> -o /PATH/Recovered/ /dev/sdb
undbx- UnDBX recovers deleted email from the respective MS Outlook
.dbxfile [Link]. Eventually it can also recover emails or fragments of them from corruped -
sudo apt install undbx -y
- UnDBX recovers deleted email from the respective MS Outlook