Given the scenario, where the blocks blue and red are groups of computers in a different physical location (building of floors).
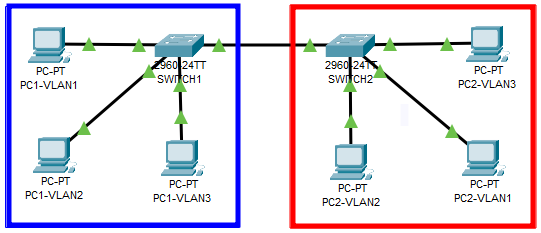
The VLAN1 is the default VLAN on all ports and any computer can reach the others with no filter or restriction.
The connection between both switches works as a “bridge”.
Dividing the network in VLANs increase security, reduces the number of routers and reduces the broadcast messages in the segments.
The “bridge” that interconnects switches becomes a Trunk Link.
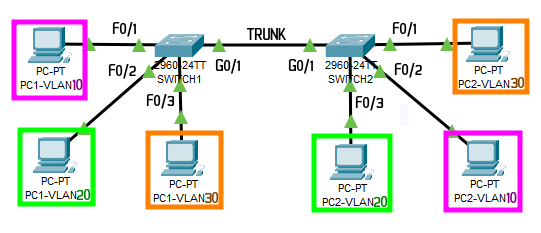
Configuration:
Switch1
enable
configure terminal
hostname Switch1
no ip domain lookup
line con 0
logging synchronous
vlan 10
name Pink
vlan 20
name Green
vlan 30
name Orange
interface f0/1
switchport mode access
switchport access vlan 10
interface f0/2
switchport mode access
switchport access vlan 20
interface f0/3
switchport mode access
switchport access vlan 30
interface range f0/4-24
shutdown
interface g0/1
switchport mode trunk
Switch2
enable
configure terminal
hostname Switch2
no ip domain lookup
line con 0
logging synchronous
vlan 10
name Pink
vlan 20
name Green
vlan 30
name Orange
interface f0/1
switchport mode access
switchport access vlan 30
interface f0/2
switchport mode access
switchport access vlan 10
interface f0/3
switchport mode access
switchport access vlan 20
interface range f0/4-24
shutdown
interface g0/1
switchport mode trunk
Now, even if all the computers get IPs in the same network, they will not be able to communicate with each other if they are not in the same VLAN.
To check the configuration in each Switch issue the commands:
show vlan brief
show interface trunk
Learn more about [VLAN – NexGenT]
Learn more about [TRUNK – Network Direction]
The following Post is about centralizing the VLAN configuration in a server-client hierarchy, called VTP [Read It].