This post was last tested and updated for Ubuntu 22.04 LTS (not available for 24.04 yet).
The Tor network relies completely on volunteers to route the traffic from the origin to the destination.
If you are willing to run an exit node, for peace of mind, I recommend using a VPS such as 1984Hosting [Link] (Iceland) or Njalla [Link] (Sweden) which are known for privacy advocates. See this reference list [Link].
TYPES OF TOR NODE
There are 3 main types of nodes:
- Guard
- The entry point of the Tor network.
- Relay
- Middle node.
- Exit
- Exit node to the public internet.
Other types such as Bridges and Snowflakes are additional non-advertised hosts that prevent nations or organizations from blocking publicly listed nodes.
SETTING UP UNATTENDED UPDATES
Prepare the server and ensure it will automatically patch any vulnerable application and upgrade itself.
sudo timedatectl set-timezone America/New_York sudo apt update && sudo apt upgrade -y sudo apt install unattended-upgrades apt-listchanges -y sudo nano /etc/apt/apt.conf.d/50unattended-upgrades
And uncomment the following lines:
"${distro_id}:${distro_codename}-updates";
Unattended-Upgrade::Remove-Unused-Kernel-Packages "true";
Unattended-Upgrade::Remove-Unused-Dependencies "true";
Unattended-Upgrade::Automatic-Reboot "true";
Unattended-Upgrade::Automatic-Reboot-Time "17:00";
Unattended-Upgrade::Automatic-Reboot-WithUsers "true";
Configure the auto-upgrade parameters:
sudo nano /etc/apt/apt.conf.d/20auto-upgrades
Replace the content of the file with:
APT::Periodic::Update-Package-Lists "1"; APT::Periodic::Unattended-Upgrade "1"; APT::Periodic::AutocleanInterval "5"; APT::Periodic::Verbose "1";
Test for errors.
sudo unattended-upgrades --dry-run sudo cat /var/log/unattended-upgrades/unattended-upgrades.log
Then, activate the Unattended-Upgrades.
sudo dpkg-reconfigure -plow unattended-upgrades
Answer YES to allow it to automatically download and install stable updates.
For Enterprise Linux derivatives (e.g., CentOS, Alma, Rocky), use yum-cron to accomplish the update of the packages but note it does not automatically reboot your system if necessary to apply a Kernel upgrade, for example.
INSTALLING AND CONFIGURING THE TOR NODE
sudo apt install apt-transport-https -y sudo nano /etc/apt/sources.list
Add the following content:
deb http://deb.torproject.org/torproject.org jammy main deb-src http://deb.torproject.org/torproject.org jammy main
Then,
wget -O- https://deb.torproject.org/torproject.org/A3C4F0F979CAA22CDBA8F512EE8CBC9E886DDD89.asc | sudo apt-key add - sudo apt update && apt upgrade -y sudo apt install tor deb.torproject.org-keyring -y sudo nano /etc/tor/torrc
Append or replace the content of the whole file with:
Nickname NodeNick ORPort 443 ExitRelay 0 SocksPort 0 ControlSocket 0 ContactInfo [email protected]
Note: ExitRelay value 0 can be changed to 1 to become an ExitRelay (not recommended).
sudo systemctl restart tor@default sudo ufw enable sudo ufw allow 443 sudo ufw status
ADDITIONAL INFORMATION
Takes less than 3 hours for the server to be listed in the directory [Link].
Each node goes through 4 phases in its cycle-life:
- 1st – 0 to 3 days
- Unmeasured
- 2nd – 3 to 8 days
- Remote Measurement
- 3rd – 8 to 68 days
- Ramping Up as a Guard Relay
- 4th – 68+ days
- Steady-state Guard Relay
Read more about the node cycle-life at [Link].
It is recommended to backup the Tor Identity Keys:
scp -r [email protected]:/var/lib/tor/keys .
Note: port 22 may be allowed on the firewall before the copy. Remember to block the port after using it or allow it to be accessible only from a trusted source.
Alternatively to a Tor Node, there are also Tor Bridge [Link] and Tor Snowflake [Link]. All types of volunteers are needed to make the Internet free and accessible to everyone.
TRAFFIC MONITORING AND LIMITING
Consider giving some limits to traffic usage in order to prevent overage fees from your ISP (if not unlimited).
Append the following lines to /etc/tor/torrc configuration file:
AccountingStart day 0:00 AccountingMax 50 GBytes RelayBandwidthRate 25 MBytes RelayBandwidthBurst 100 MBytes
Note: the speed is in Mega-Bytes, not in Mega-Bits.
Follow the CPU and bandwidth usage for a new node under different configurations:
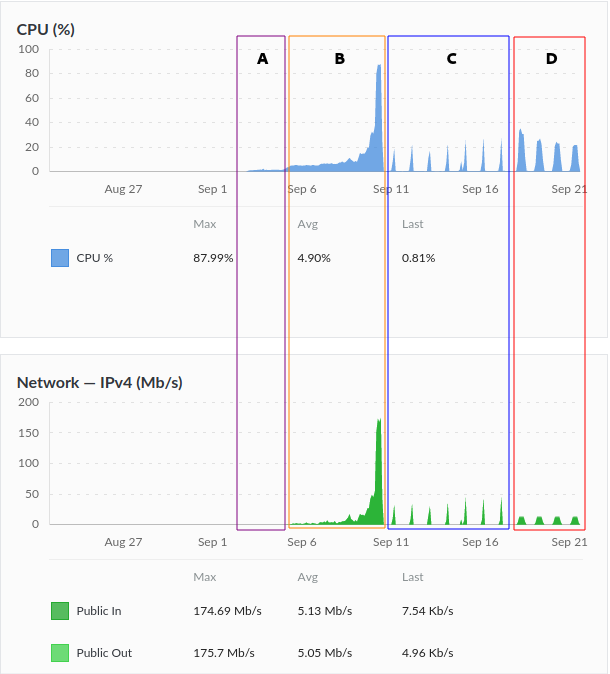
- A – Unmeasured (not relaying traffic yet).
- B – Remote Measurement followed by Ramping Up as a Guard Relay (Relaying traffic progressively).
- C – A limit of 35GB (each direction) was applied to control the total amount of data used.
- D – Not only a daily limit but also speed control up to 1.5MByte/s, which resulted in extra CPU usage.
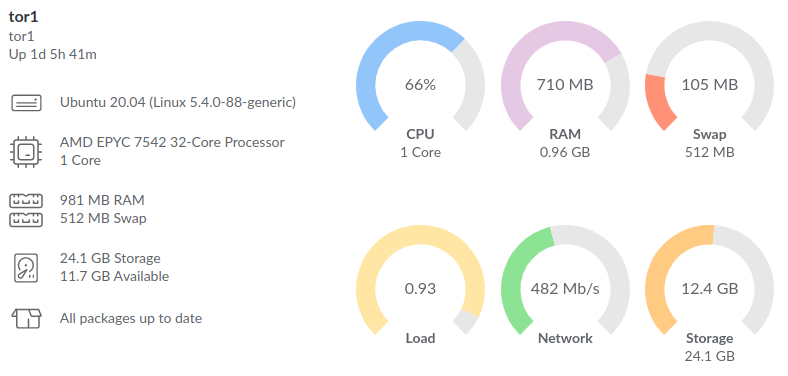
Don’t be surprised if your node consumes 6TB of traffic (inbound + outbound) in less than 3 days:
Monitor traffic in real-time with Tor Nyx [Link].
sudo apt-get install nyx -y sudo nano /etc/tor/torrc
Append the following lines:
ControlPort 9051 CookieAuthentication 1
Restart Tor and execute Nyx:
sudo systemctl restart tor@default nyx
To be able to run Nyx as another user, change the permission of the token file.
sudo chmod 777 /run/tor/control.authcookie
Consider customizing your Nyx console by adding parameters to the file:
nano .nyx/config
Examples can be found at [Link].