Kasm Workspaces (KW) is a web-native open-source “Container Streaming Platform” [Link]. What does that really mean?
KW used Docker and the technology to runs ephemeral sessions of applications and desktops to end-users and streams them encrypted (no VPN required) to any web browser.
Behind the curtains, KW provides enterprise-class orchestration, data loss prevention, and web streaming technology out-of-the-box. See more features and technical details on the official documentation [Link].
System requirements:
- 4 vCPU (the minimum is 2 but not practical)
- 8GB of RAM (the minimum is 4 but it is not enough for desktops)
- 100GB of Storage (the documentation says 50GB but the installation refuses to proceed)
- Operating system (amd64/arm64):
- Debian 9+ / Ubuntu 18.04+ / RaspberryPi OS 10+ (Debian-based)
- CentOS 7+ / Oracle Linux 7+ (RHEL based)
Note: do not use the base minimum for real usage because will create problems and the experience will be not satisfactory.
INSTALLING KASM WORKSPACE ON DEBIAN 12
Preparing the system:
sudo apt update && sudo apt upgrade -y sudo reboot
If prompted for a new Kernel installation allow it to proceed.
Downloading and installing (replace the version with the latest available):
wget https://kasm-static-content.s3.amazonaws.com/kasm_release_1.15.0.06fdc8.tar.gz tar -xf kasm_release_*.tar.gz && cd kasm_release/ sudo ./install.sh
It is highly recommended to have a SWAP partition/file. Just accept and the installation will proceed on creating one.
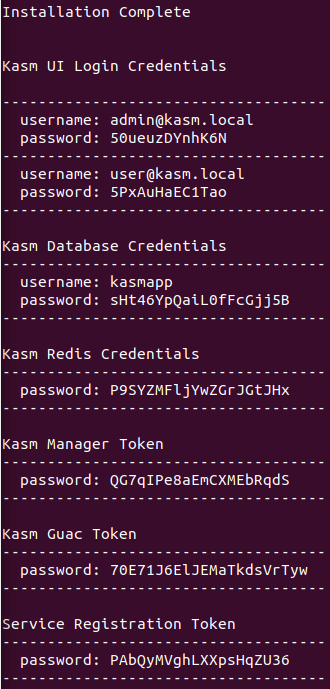
The installation might end with the following output. Make notes of all newly generated credentials (they won’t be shown again):
ACCESSING THE KW DASHBOARD
Navigate to the address of your server https://10.10.10.10/
It already has a self-signed certificate installed but for Internet access, it is recommended (not required) to have a public certificate installed on a reverse proxy server on another server that might work as a shield.
- Admin Dashboard
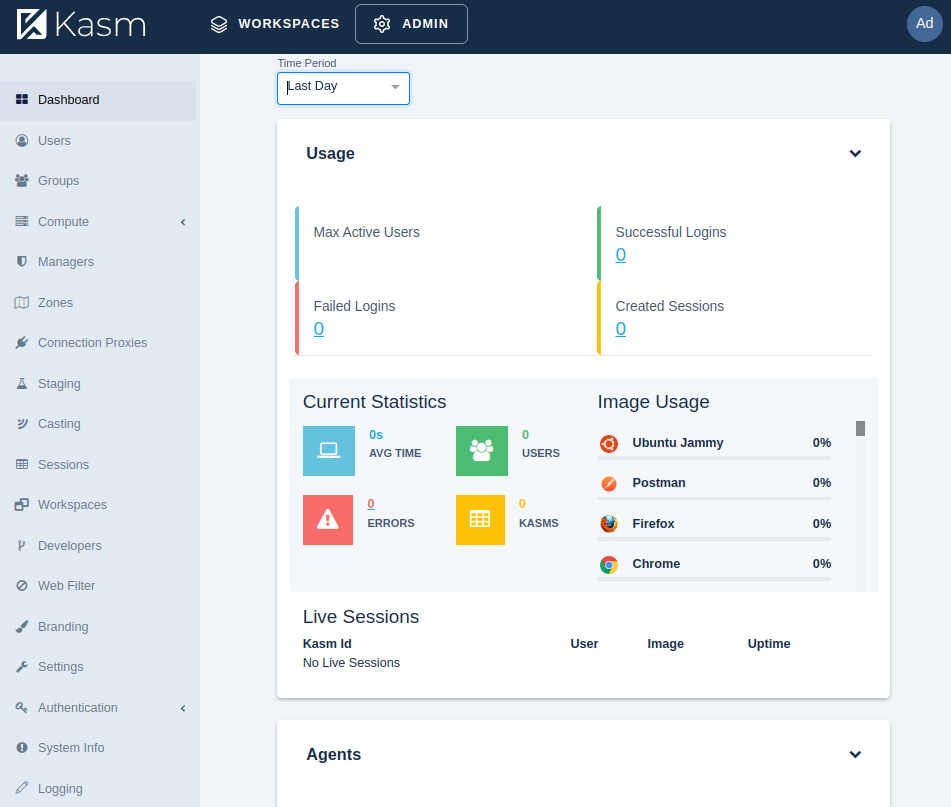
- User Dashboard

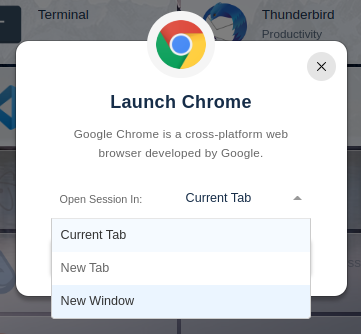
By clicking to launch any session it will prompt:
On a new tab, I open the first session and did a basic fingerprinting test on any free test site:
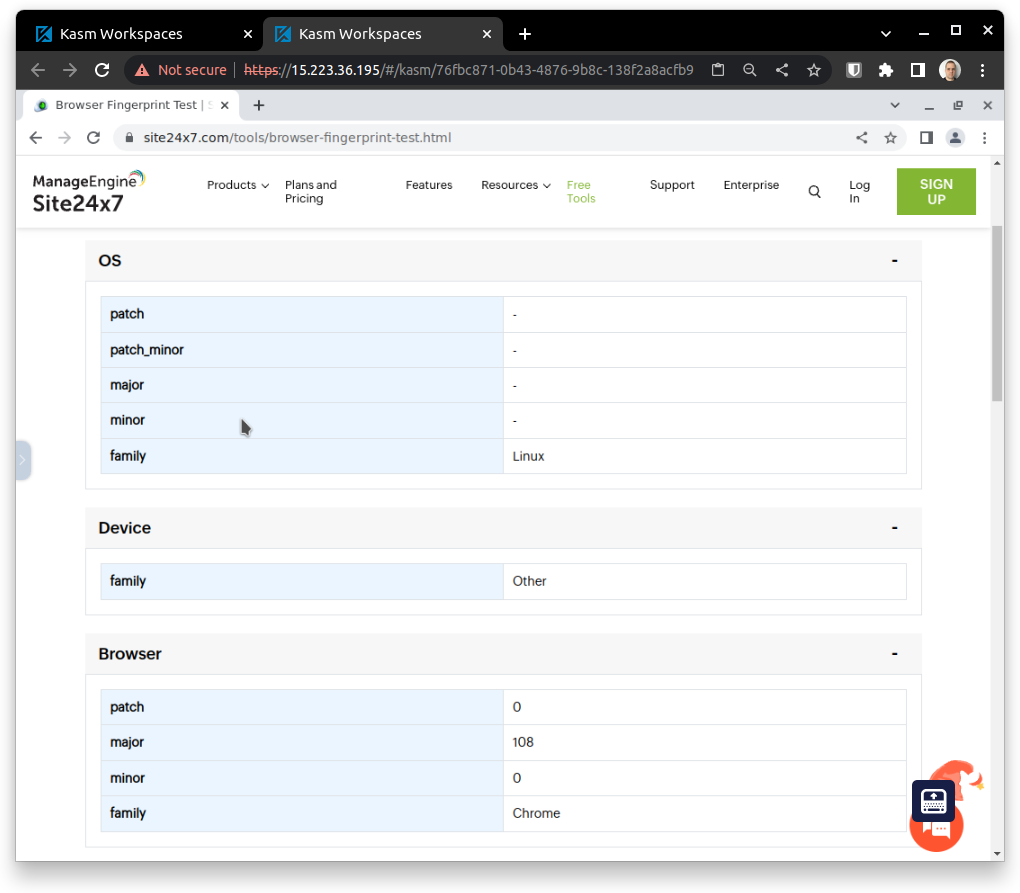
As one can see, it does not reveal much of its operating system and browser, just the base minimum.
IMPORTANT: do not consider this tool as a complete anonymity platform unless you are using the Tor Browser!
Back to the main tab, the running session is shown as a thumbnail and can be resumed, minimised, or terminated at any time.
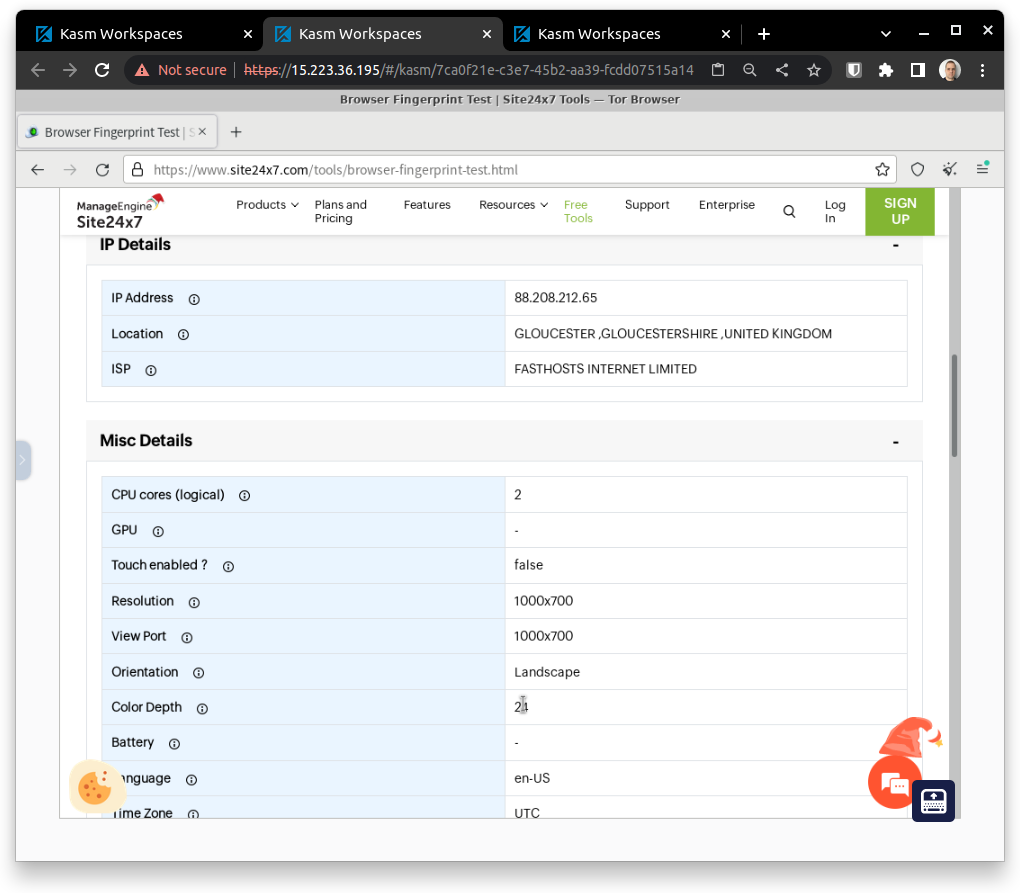
The same test was perform under another session. The Tor Browser was used this time:
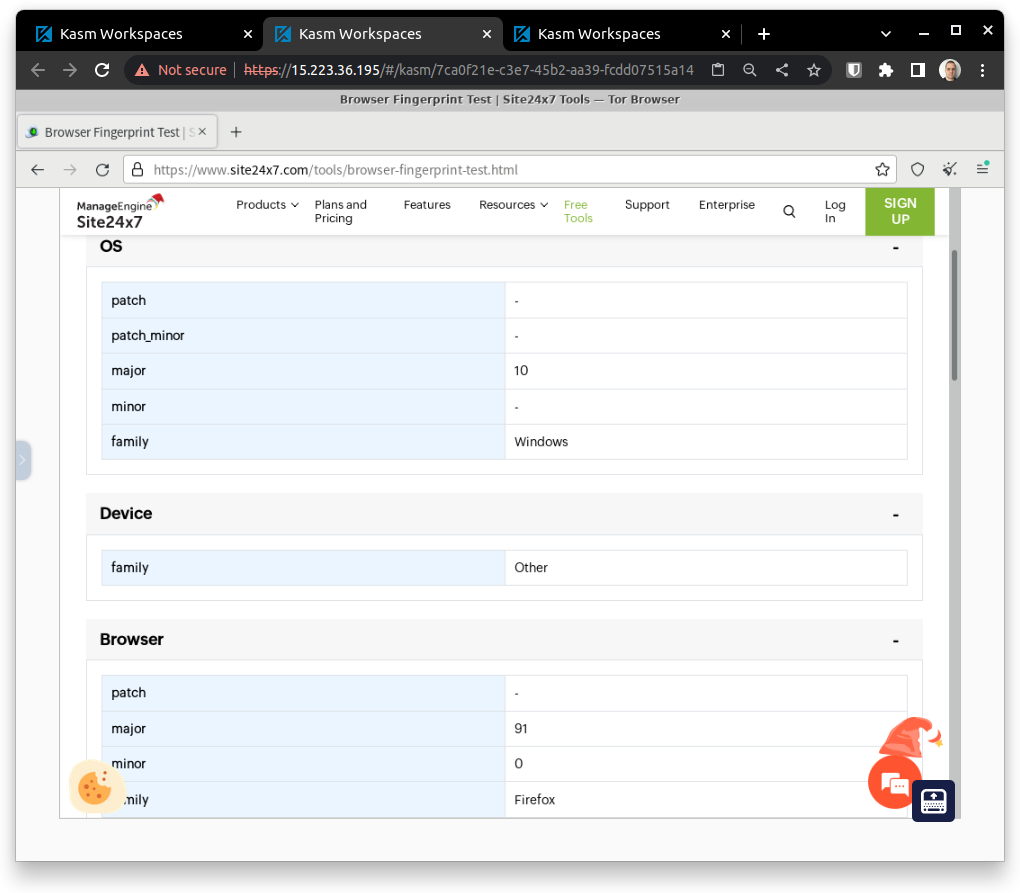
Of course, a much better job was done to cleanup the identifiable information:
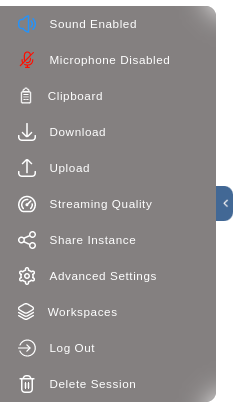
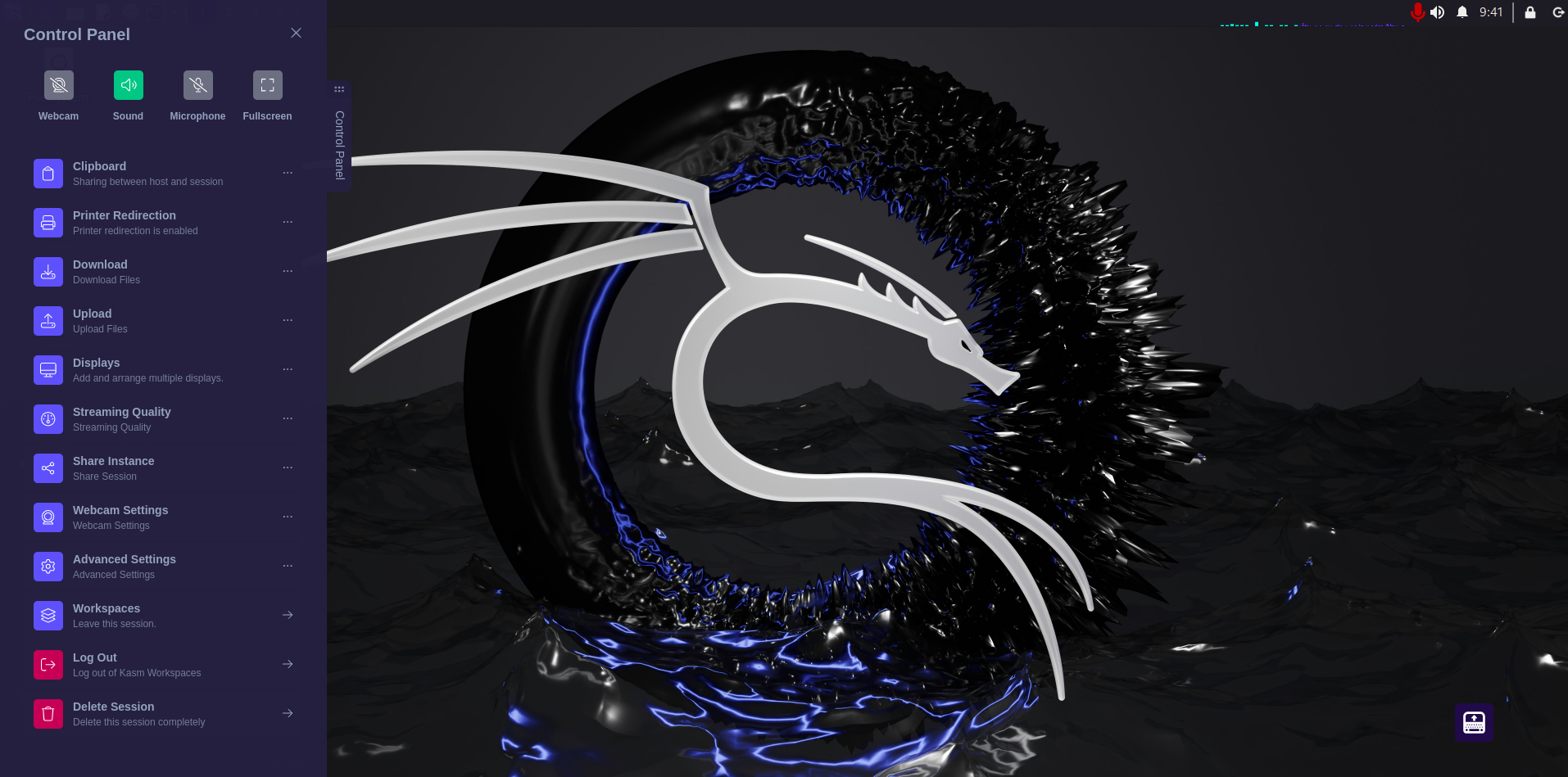
In all sessions there will be a left side menu to help with the interaction over the customized web VNC session:
Back to the main tab (dashboard), the active sessions will be available with a countdown time out for self-termination if not interacted for more than 60 minutes:

Note: all sessions are ephemeral and no data will persist after terminating. It is design intent! If applications, extensions, or retention of any data is needed this might not be the best suitable tool. Custom images can also be created for specific application needs or connecting to a network share or a drive in the cloud might suit most needs for data retention.
UPDATED UI
The new UI is much prettier but offers the same features. That is how it looks like if you get a fresh installation in 2024.
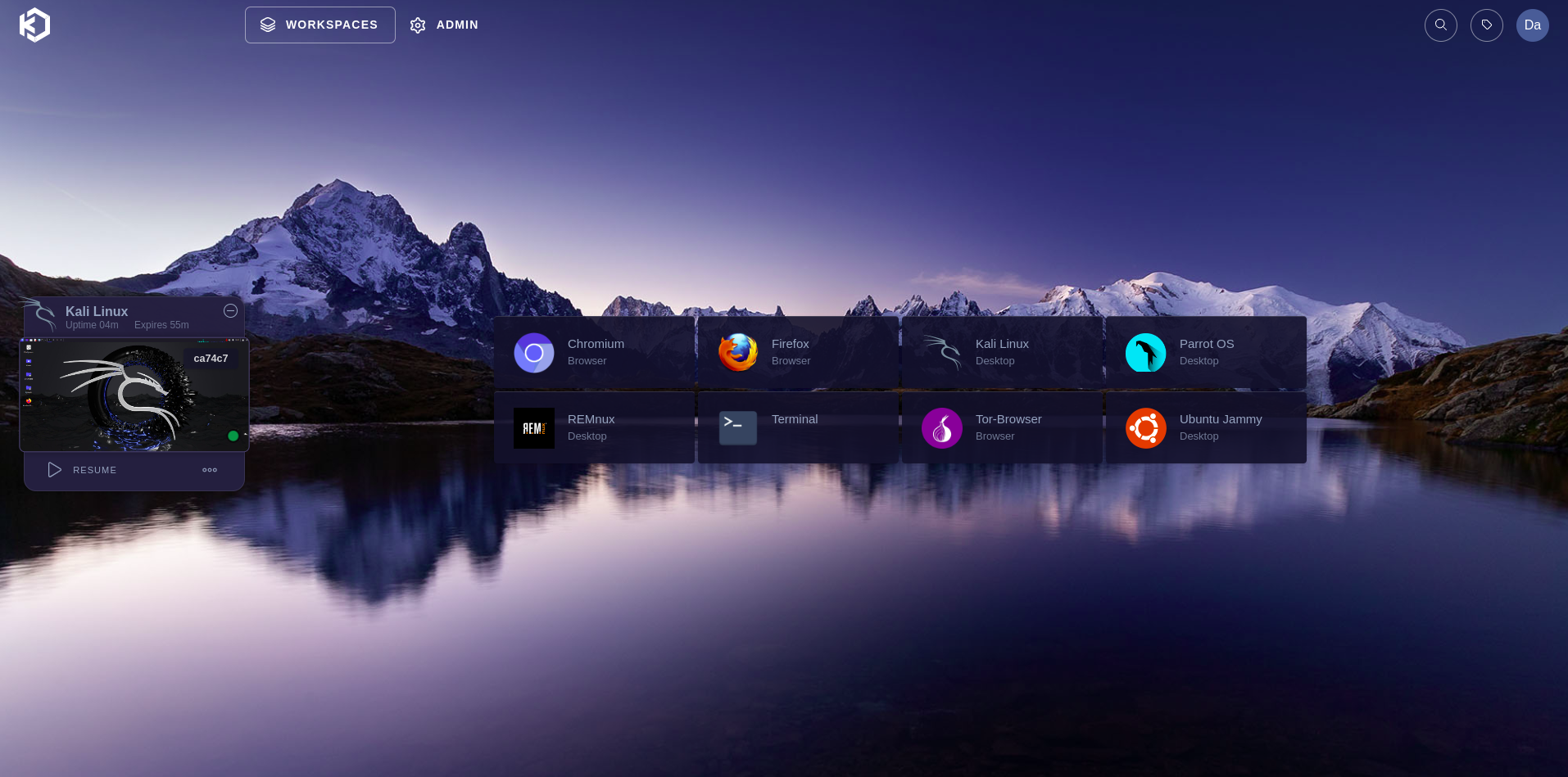
MOREOVER
Karm Workspaces go away and beyond the demonstrated functionalities, such as but not limited to:
- Multi-server load distribution in a single or a multi-zone,
- Users and groups management capable of using LDAP, SAML, OpenID, and 2FA,
- Reporting, logging, web filtering, etc,
- GPU pass-through acceleration,
- Session Staging/Casting/Sharing,
- Optionally, it offers native persistent data and profiles, compatibility with Tailscale, and much more.
Mapping a path from the server’s file system into the container. Admin > Workspaces > Edit > Volume Mappings (JSON):
{
"/server/path": {
"bind": "/container/path",
"mode": "rw",
"uid": 1000,
"gid": 1000,
"required": true,
"skip_check": false
}
Overriding container configuration. Admin > Workspaces > Edit > Docker Run Config Override (JSON):
{
"hostname": "kasm",
"user": "root"
}
Execute a command on lunch to allow kasm_user to use sudo with no password:
{ "first_launch":{ "user":"root", "cmd":"bash -c 'echo \"kasm-user ALL=(ALL) NOPASSWD: ALL\" >> /etc/sudoers' ; apt update" } }
BONUS
Kasm Workspace can be installed in a LXC (Linux Container) in Proxmox. This nested solution will make the best usage of your home lab resources.
Note / Tips
- Upon the creation of the CT, uncheck the box that defines the container as “unprivileged“,
- Edit the container settings at Options > Features and check the box for “nesting“,
- Containers run with the
rootuser, so the scriptsinstall.shandinstall_dependencies.shmust to be manually modified to remove all occurrences of the commandsudoor it will fail the installation.